
Poorly configured Docker servers and being actively targeted by the TeamTNT hacking group in an ongoing campaign started last month.
According to a report by researchers at TrendMicro, the actors have three distinct goals: to install Monero cryptominers, scan for other vulnerable Internet-exposed Docker instances, and perform container-to-host escapes to access the main network.
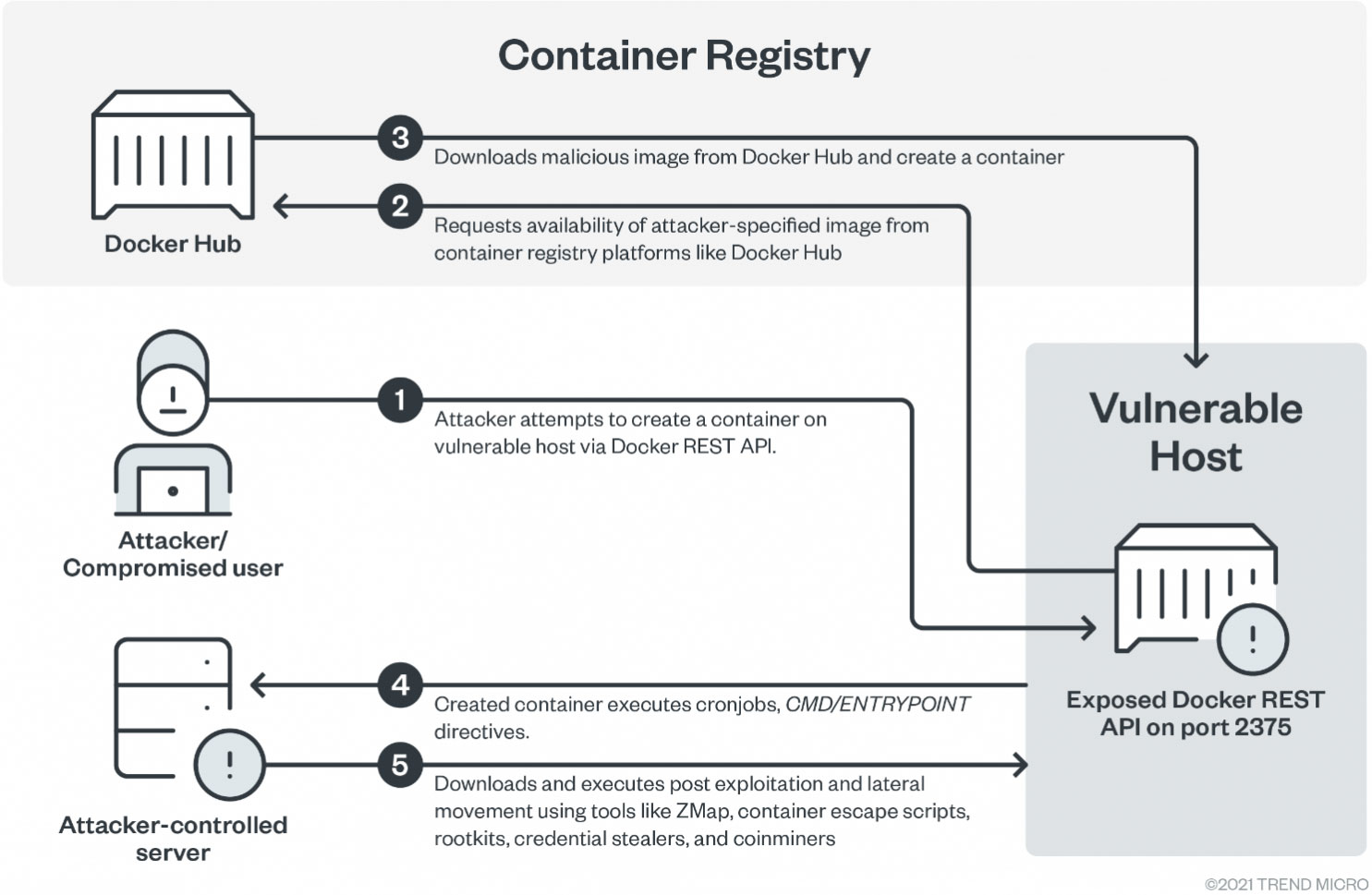
As illustrated in an attack workflow, the attack starts with creating a container on the vulnerable host using an exposed Docker REST API.
Source: TrendMicro
TeamTNT then uses compromised, or actor-controlled Docker Hub accounts to host malicious images and deploy them on a targeted host.
TrendMicro has seen over 150,000 pulls of images from the malicious Docker Hub accounts as part of this campaign.
Next, the dropped container executes cronjobs and fetches various post-exploitation and lateral movement tools, including container escaping scripts, credential stealers, and cryptocurrency miners.
When scanning for other vulnerable instances, the threat actors check ports 2375, 2376, 2377, 4243, 4244, which has been observed in past DDoS botnet campaigns.
The actors also attempt to collect server info such as the OS type, architecture, number of CPU cores, container registry, and the current swarm participation status.
The container image that is created is based on the AlpineOS system and is executed with flags that allow root-level permissions on the underlying host.
Source: TrendMicro
Finally, the IP address that is used for TeamTNT’s current infrastructure (45[.]9[.]148[.]182) has been associated with multiple domains that served malware in the past.
Previous campaign laid the groundwork
TrendMicro reports that this campaign also uses compromised Docker Hub accounts controlled by TeamTNT to drop malicious Docker images.
Using compromised Docker Hub accounts makes the distribution points more reliable for the actors, as they are harder to map, report, and takedown.
The actors were spotted collecting Docker Hub credentials in a previous campaign analyzed by TrendMicro in July when credentials stealers were deployed in attacks.
"Our July 2021 research into TeamTNT showed that the group previously used credential stealers that would rake in credentials from configuration files. This could be how TeamTNT gained the information it used for the compromised sites in this attack," explains TrendMicro's research published today.
As such, TeamTNT demonstrates a high level of operational planning, being organized and purposeful in their goals.
Permanent threat to Docker systems
TeamTNT is a sophisticated actor that constantly evolves its techniques, shifts short-term targeting focus but remains a constant threat to vulnerable Docker systems.
They first created a worm to exploit Docker and Kubernetes en masse back in August 2020.
In October 2020, the actors added Monero mining and credential-stealing capabilities, targeting Docker instances.
In January 2021, TeamTNT upgraded its miners with sophisticated detection evasion tricks while still harvesting user credentials from the compromised servers.
Docker provides some "mandatory" tips that can be used lock down Docker's REST API and prevent these types of attacks.
"Therefore it is mandatory to secure API endpoints with HTTPS and certificates. It is also recommended to ensure that it is reachable only from a trusted network or VPN," explains Docker's security guide.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now