
Receiving an unprompted one-time passcode (OTP) sent as an email or text should be a cause for concern as it likely means your credentials have been stolen.
One of the initial components of a cyberattack is the theft of legitimate credentials to corporate networks and online services. These credentials can be stolen in phishing attacks, credential stuffing attacks, via information-stealing malware, or social engineering attacks.
The stolen credentials are then used to breach corporate networks for data theft, espionage, and ransomware attacks or to conduct financial fraud in consumers' online retail accounts.
Marketplaces devoted to selling stolen consumer online accounts make financial fraud easy, where threat actors can buy accounts for as little as $1.50 to Amazon, Marriot Bonvoy rewards accounts, Dunkin, Instacart, and many other well-known retail stores.

Source: BleepingComputer
To better secure your online accounts, many companies offer a security feature called multi-factor authentication (MFA), which when configured, requires users to enter an additional form of verification before being allowed to log in to their account.
This verification could be a one-time passcode sent as an email or text message that must be inputted into the site, a passcode from an authenticator app, or the presence of a configured hardware security key.
By using MFA, even if a threat actor successfully obtains your account credentials, they cannot log in without first passing the multi-factor verification prompt, significantly reducing successful account breaches.
Unprompted OTP codes
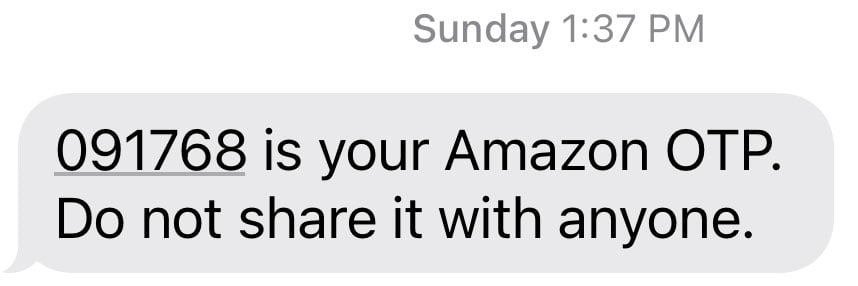
This week, both a friend and a family member reached out to me stating that they received a text message from Amazon containing an MFA OTP required to log in to their account.
Source: BleepingComputer
The text message came from the same number used in previous Amazon texts, contained no links, and simply displayed an OTP used for login.
The only difference is that they had not attempted to log into Amazon, so the OTP was unprompted and unexpected.
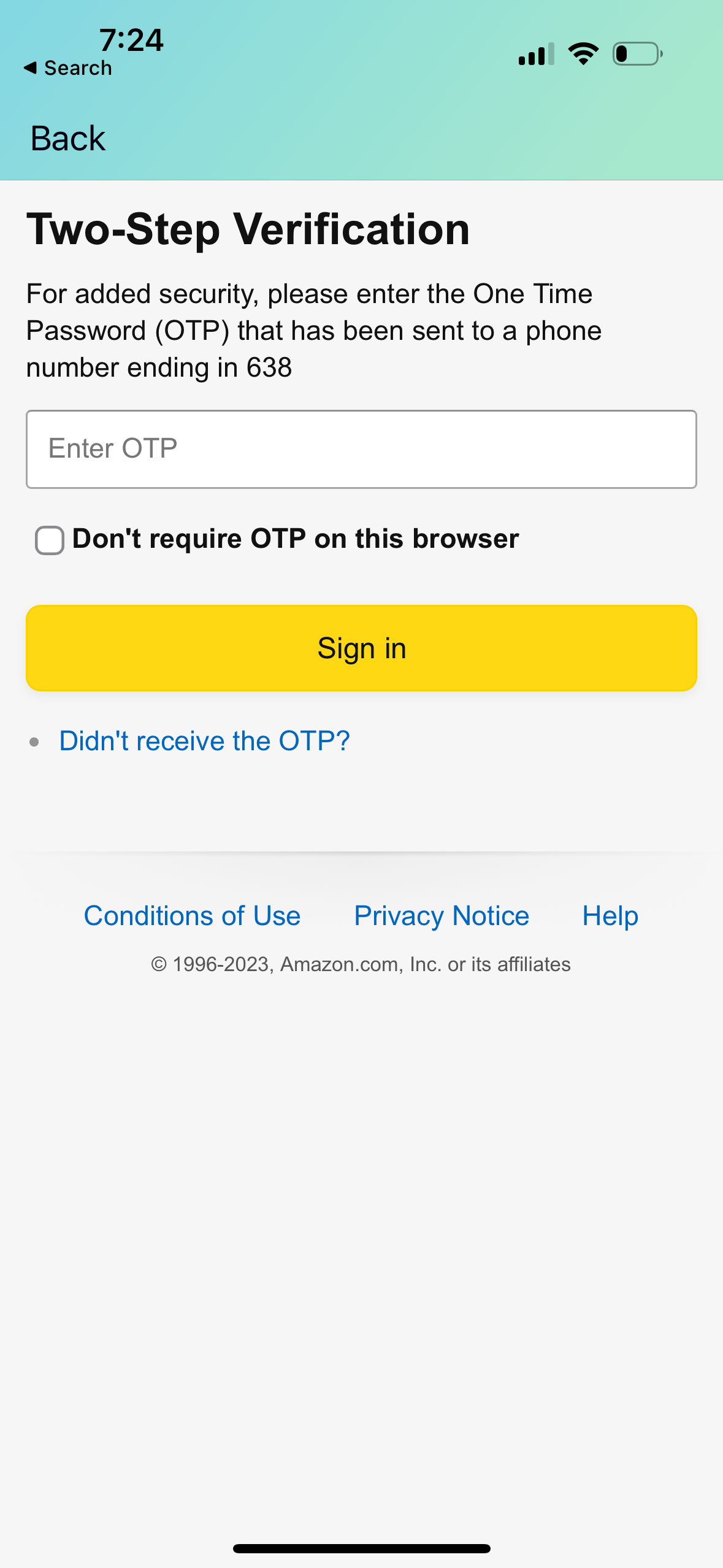
This meant someone else attempted to use the person's credentials at Amazon but was stopped by the two-factor verification prompt (Amazon calls it two-step verification).
Source: BleepingComputer
When receiving an unprompted 2FA code, the account holder should assume their credentials were stolen and log directly into Amazon, without clicking on any links in text messages or emails, to change their password.
If that same password is used with any of your other accounts, it should also be changed immediately on those sites.
It is also important to not think that since 2FA protected your account you no longer need to change your password. This is a false sense of security, as threat actors have figured out ways to bypass MFA in the past, so there is no reason to give them the opportunity to do so with your account.
Furthermore, while SMS and email 2FA provide extra protection to your accounts, they are the most risky MFA method to use. This is because if someone gains access to your email or phone number, such as through a SIM swapping attack, they'll also have access to your OTP codes.
This would allow them to reset your password without you knowing until it was too late.
Instead, if a site provides support for authentication apps, hardware security keys, or passkeys, you should use one of these options instead as they’ll require attackers to have access to your device to pass the multi-factor authentication challenge.



Comments
EhWhatsUpDoc - 6 months ago
What I like about SMS second-factor is that I receive an immediate notification that my account credentials have been compromised. I use a VOIP number for my second factor that is also protected by 2-factor authentication, so I think I am less susceptible to Sim-swapping. Unfortunately many companies do not accept VOIP numbers for second-factor authentication. Ideally, I would like to use a TOTP second factor, but still receive a notification of the login attempt. Long live SQRL.
tech_engineer - 6 months ago
The SMS factor is confusing sometimes, I get every 2-3 months an SMS from Google, but I know my password is secure (in addition to using PassKey). The messages from Google don't say why they were sent or for which account.
Example message: G-xxxxxx is your Google verification code.