
General Electric is investigating claims that a threat actor breached the company's development environment in a cyberattack and leaked allegedly stolen data.
General Electric (GE) is an American multinational company with divisions in power, renewable energy, and aerospace industries.
Earlier this month, a threat actor named IntelBroker attempted to sell access to General Electric's "development and software pipelines" for $500 on a hacking forum.
After not selling said alleged access, the threat actor posted again that they are now selling both the network access and allegedly stolen data.
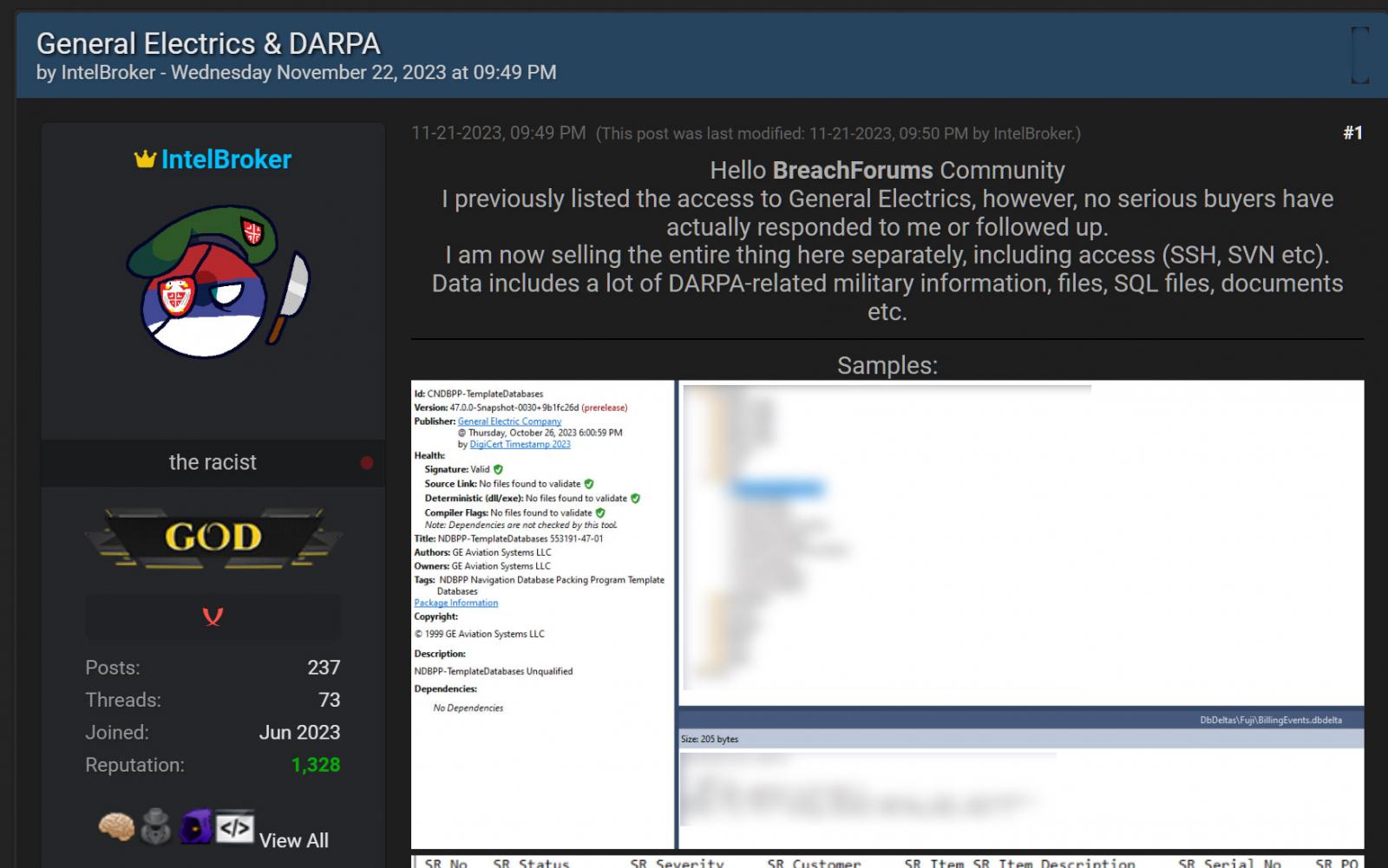
"I previously listed the access to General Electrics, however, no serious buyers have actually responded to me or followed up. I am now selling the entire thing here separately, including access (SSH, SVN etc)," the threat actor posted to a hacking forum.
"Data includes a lot of DARPA-related military information, files, SQL files, documents etc."
Source: BleepingComputer
As proof of the breach, the threat actor shared screenshots of what they claim is stolen GE data, including a database from GE Aviations that appears to contain information on military projects.
In a statement to BleepingComputer, GE confirmed they are aware of the hacker's claims and are investigating the alleged data leak.
"We are aware of claims made by a bad actor regarding GE data and are investigating these claims. We will take appropriate measures to help protect the integrity of our systems," a GE Spokesperson told BleepingComputer.
While the breach has not been confirmed, IntelBroker is a hacker known for successful, high-profile cyberattacks in the past.
This includes a Weee! grocery service breach and the theft of sensitive personal information from the District of Columbia's D.C. Health Link program.
DC Health Link is a healthcare marketplace for Washington, D.C., used by many White House and House staffers and their families.
In March, IntelBroker breached DC Health Link and claimed to have sold a stolen database containing the personal information of thousands of people.
This breach led to wide media coverage and a congressional hearing to learn more about and investigate how the breach occurred.
During the hearing, Mila Kofman, Executive Director of the District of Columbia Health Benefit Exchange Authority, explained that the data was exposed through a server that was misconfigured so that it was accessible online.



Comments
Hunze - 7 months ago
<p>Why doesn't that really surprise me? For years I have been asking GE administrators to please secure their email domain ge.com. To date, the domain is unsecured against spoofing attacks. So it's only a matter of time before someone takes advantage of this.</p>
IhateMicroSoft - 7 months ago
Well, this is surprising to see @Hunze. DMARC Quarantine/Reject policy not enabled. Additionally, the mail server is using ProofPoint so its just another attack vector, if/when someone finds a vulnerability with ProofPoint. Note, no hacking was done to gather this information. Its all in the MX records.
Hunze - 7 months ago
Yes, you are right, but the existence of SPF and co would improve the situation for customers and suppliers in the event of supply chain attacks. The lack of these simple mechanisms also shows a certain amount of attitude towards the topic
arkysaw - 7 months ago
Is that affecting GE? or is it affecting GE Aerospace? since they are different companies.