
The Brute Ratel post-exploitation toolkit has been cracked and is now being shared for free across Russian-speaking and English-speaking hacking communities.
For those unfamiliar with Brute Ratel C4 (BRC4), it is a post-exploitation toolkit created by Chetan Nayak, an ex-red teamer at Mandiant and CrowdStrike.
Red teamers are cybersecurity professionals whose job is to try and breach a corporate network to learn its flaws, while those on the blue team attempt to defend against these attacks.
After these exercises, both groups discuss what was found to shore up defenses and enhance security.
Similar to Cobalt Strike, Brute Ratel is a toolkit used by red teamers to deploy agents, called badgers, on compromised network devices and use them to execute commands remotely and spread further on a network.
Brute Ratel is cracked
Over the past few years, cracked versions of Cobalt Strike have been so heavily abused by threat actors and ransomware gangs that it is more easily detected by security software.
Due to this, some threat actors and ransomware gangs have been quietly switching to Brute Ratel for their attacks by allegedly creating fake US companies to pass the licensing verification system.
However, things are about to change, as cyber threat intelligence researcher Will Thomas (aka BushidoToken) has reported that a cracked copy of Brute Ratel is now circulating widely among threat actors in online hacking forums.
"There are now multiple posts on multiple of the most populated cybercrime forums where data brokers, malware developers, initial access brokers, and ransomware affiliates all hang out," warns Thomas in a new report on the cracked version of Brute Ratel.
"This includes BreachForums, CryptBB, RAMP, Exploit[.]in, and Xss[.]is, as well as various Telegram and Discord groups."
From a brief search on both the XSS and Breached hacking forums, threat actors have created multiple topics where they have been sharing the cracked version of Brute Ratel C4 version 1.2.2 since the middle of September.
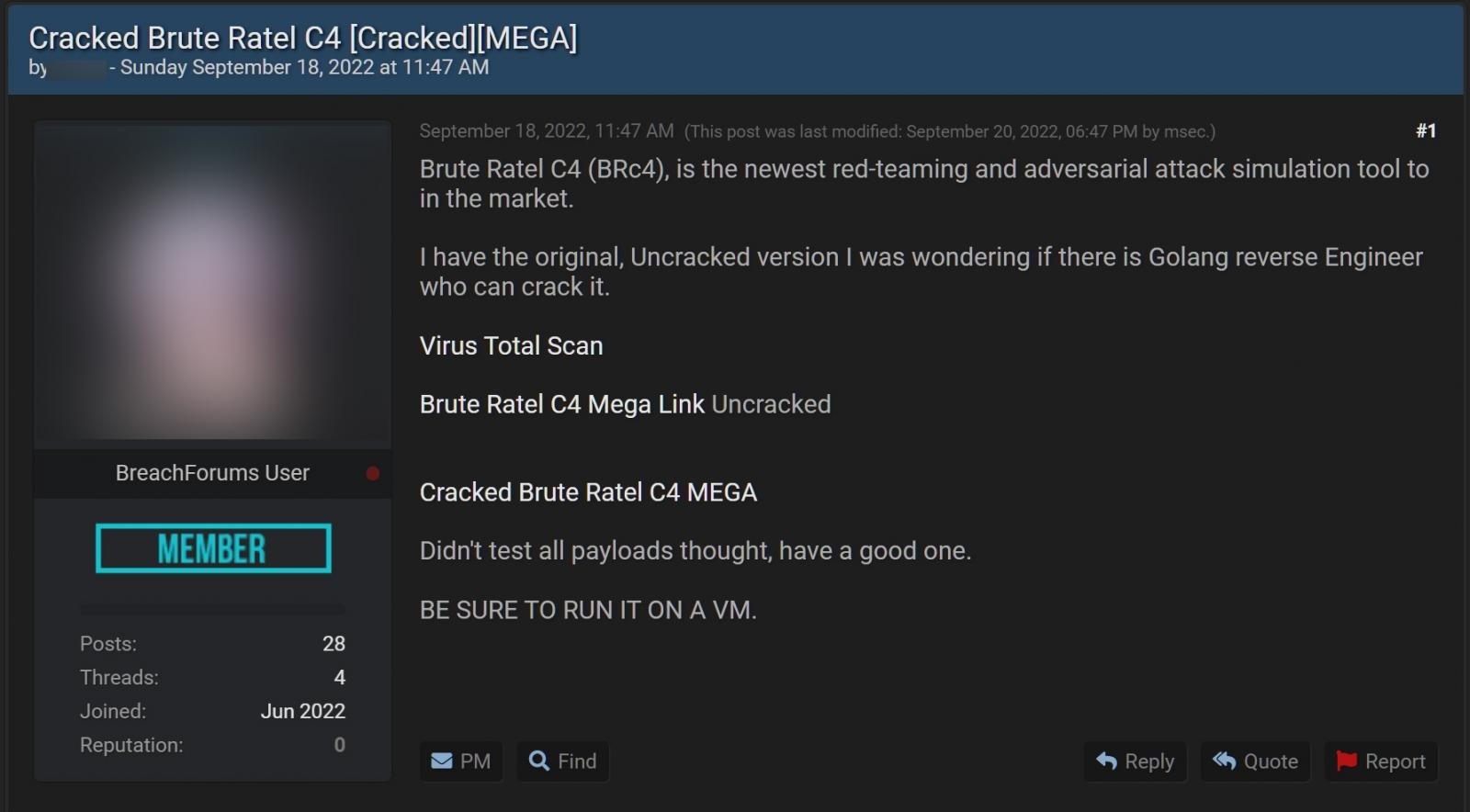
Source: BleepingComputer
In the past, Brute Ratel developer Chetan Nayak told BleepingComputer that he could revoke the licenses for any customers abusing Brute Ratel for malicious purposes.
However, Nayak claims that the uncracked version was uploaded to VirusTotal, which was then cracked by the "Russian group Molecules" to remove the license check.
Regardless of how the software was leaked, it is unfortunately too late.
Thomas has told BleepingComputer that the cracked version works and does not appear to be tampered with, meaning we will likely see wide usage of the toolkit shortly.
"Yes, you don't need to enter the license key, and no doesn't look tampered to me or my colleagues in Curated Intel," explained Thomas in a conversation with BleepingComputer.
In fact, threat actors have already begun sharing screenshots on hacking forums of them testing the toolkit.
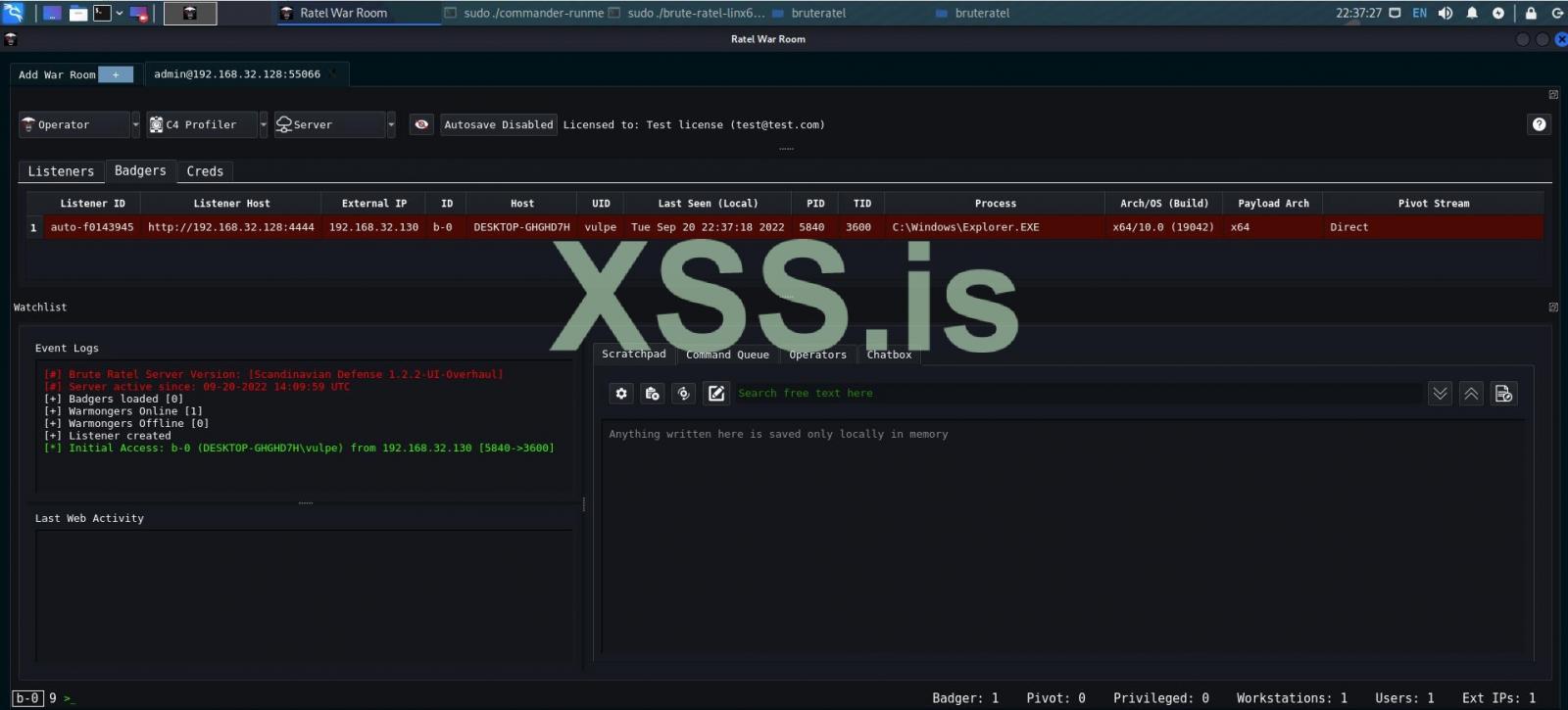
Source: XSS
What is most concerning to Thomas is that Brute Ratel has the ability to generate shellcode that is not easily detected by security software at this time.
"One of the most concerning aspects of the BRC4 tool for many security experts is its ability to generate shellcode that is undetected by many EDR and AV products," explained Thomas in his report.
"This extended window of detection evasion can give threat actors enough time to establish initial access, begin lateral movement, and achieve persistence elsewhere."
Thomas recommends security, windows, and network admins review MdSec's blog on Brute Ratel C4 to learn more about detecting the software on their networks.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now