
Someone is flooding Cobalt Strike servers operated by former members of the Conti ransomware gang with anti-Russian messages to disrupt their activity.
The operators of Conti ransomware completed turning off their internal infrastructure in May this year but its members have dispersed to other ransomware gangs, such as Quantum, Hive, and BlackCat.
However, former Conti members continue to use the same Cobalt Strike infrastructure to conduct new attacks under other ransomware operations.
Server flood
Someone is now tracking the TeamServers (C2) used by ransomware actors to control the Cobalt Strike (CS) Beacon payloads on compromised hosts (clients), which allow lateral movement on the network.
When flooding the CS servers, these people are using the username “Stop Putin!” on multiple computers and changing their computer name to various messages, such as “Stop the war!,” “15000+ dead Russian soldiers!,” and “Be a Russian patriot!”
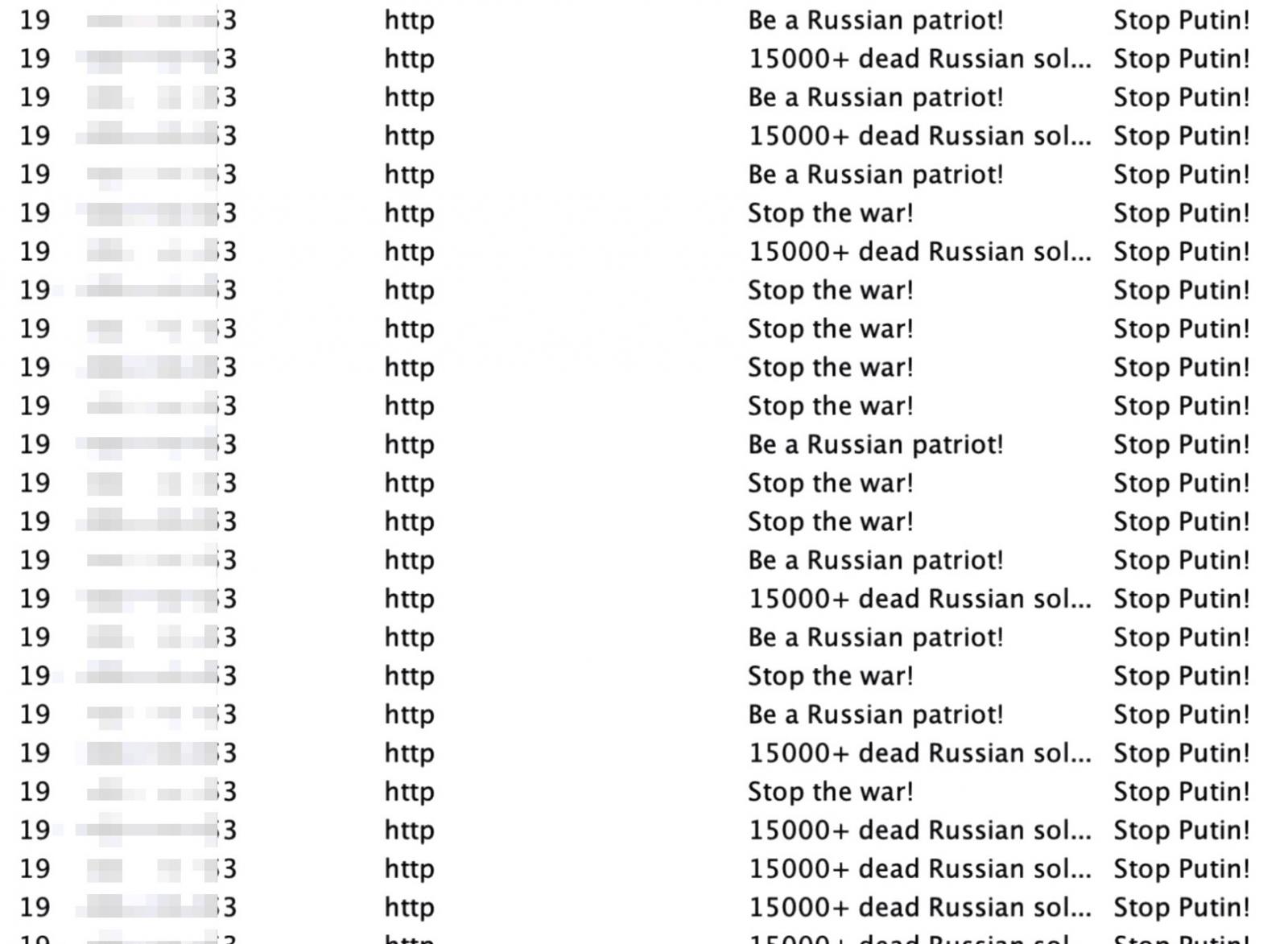
source: Vitali Kremez (AdvIntel)
Vitali Kremez, the CEO of cyber intelligence company Advanced Intelligence (AdvIntel), told BleepingComputer that whoever is running these attacks initially targeted at least four Cobalt Strike servers allegedly controlled by ex-Conti members.
The researcher says that the messages are flooding the servers at a high rate of about two every second.
As an effect of this large number of pings, TeamServer’s Java application is overloaded and activity is disrupted in a similar way a denial-of-service (DoS) condition would.
Running Cobalt Strike TeamServer from a Java application was possible in versions of the toolkit up to 4.6, released this year in April. In more recent releases, the component runs from an executable image (TeamServerImage).
Kremez says whoever is behind this activity is constantly targeting Cobalt Strike servers believed to be operated by previous Conti ransomware members, resuming the flood whenever a new server is discovered.
Turning the tables on cybercriminals
It is unclear who is behind these messages (it could be anyone from a security researcher, to law enforcement agencies, to a cybercriminal with a grudge for siding with Russia) but it looks like they’re keeping the threat actor busy.
Disrupting ransomware gangs’ activity with denial-of-service has happened before, the LockBit operation being a recent target, allegedly for encrypting systems belonging to digital security company Entrust.
The attack was serious enough for LockBit to shut down its leak sites and start reorganizing its infrastructure. In the meantime, none of the data the gang published was available.
The hackers blamed the DDoS on Entrust since the HTTPS requests came with the message to delete the company’s data.
However, the disruption was temporary and the ransomware actor came online with stronger infrastructure allowing them to keep the stolen data available even when facing distributed denial-of-service (DDoS) attacks.



Comments
EndangeredPootisBird - 1 year ago
Maybe dont make pen testing tools open source? That way cybercriminals cant abuse them, if it was the case almost all cyberattacks against businesses and governments nowadays would never have happened
b00meraang - 1 year ago
I am not sure who but Cobalt Strike was leaked in GitHub. So not intentionally made to be open source. Deep Blue for example was a zero day hoarded by US gov and then stolen by apt's then released in the open.
EndangeredPootisBird - 1 year ago
Even so, penetration testing companies should be treated as cybercriminals as they have aided in the biggest advancement of cyberattacks in history, even if their intent was benign.
h_b_s - 1 year ago
"Even so, penetration testing companies should be treated as cybercriminals as they have aided in the biggest advancement of cyberattacks in history, even if their intent was benign."
Sure, let's through the baby out with the bath water and just lock up every single security researcher out there. Cuz you know... they might have shown a criminal how to break into AD servers. Can't have that! Oh wait... if you lock up all the security researchers... then the only people attacking systems... will be... those very same criminals (they just had to do a little more work - it's not difficult to find exploitable flaws in most software)....
Brilliant!!!
Instead, these PoC allow competent security practitioners to discover if their own software is vulnerable, or it's mitigated for some other reason. Competence is key. Unfortunately, it's often hamstrung by management & political decisions. Be very clear, the criminals are the ones carrying out the attacks are the people liable for their own deeds, NOT the people trying to inform the IT and software development communities at large to the existence of these flaws. Many times, the ONLY way to get these corporations and governments to fix their crap, is to make the information public and shame them into fixing it.