
Uniswap, a popular decentralized cryptocurrency exchange, lost close to $8 million worth of Ethereum in a sophisticated phishing attack yesterday.
While the protocol hasn't been compromised by exploiting a vulnerability as initially suspected, the cyberattack has impacted many investors in digital assets.
The threat actors used the lure of free UNI tokens (airdrops) to trick victims into granting a transactions that gave hackers full access to wallets.
The trap was a masked "setApprovalForAll" function that assigns or revokes full approval rights to the operator, essentially allowing the attacker to redeem all Uniswap v3 LP tokens for ETH in the victim wallet.
1/ Yesterday, some Uniswap LPs unfortunately fell for a phishing scam, a problem far too common in crypto today. To be clear: there was no exploit. The Protocol always was — and remains — secure. Here’s what happened.
— Uniswap Labs (@Uniswap) July 12, 2022
In total, the threat actors siphoned 7,574 ETH to a wallet address under their control and quickly moved 7,500 to the Tornado Cash service for mixing (laundering).
Spoofing Uniswap
The phishing actors created an ERC20 token and airdropped it to 73,399 users who held UNI tokens, spending 8.5 ETH in TX fees for the high volume of the transactions.
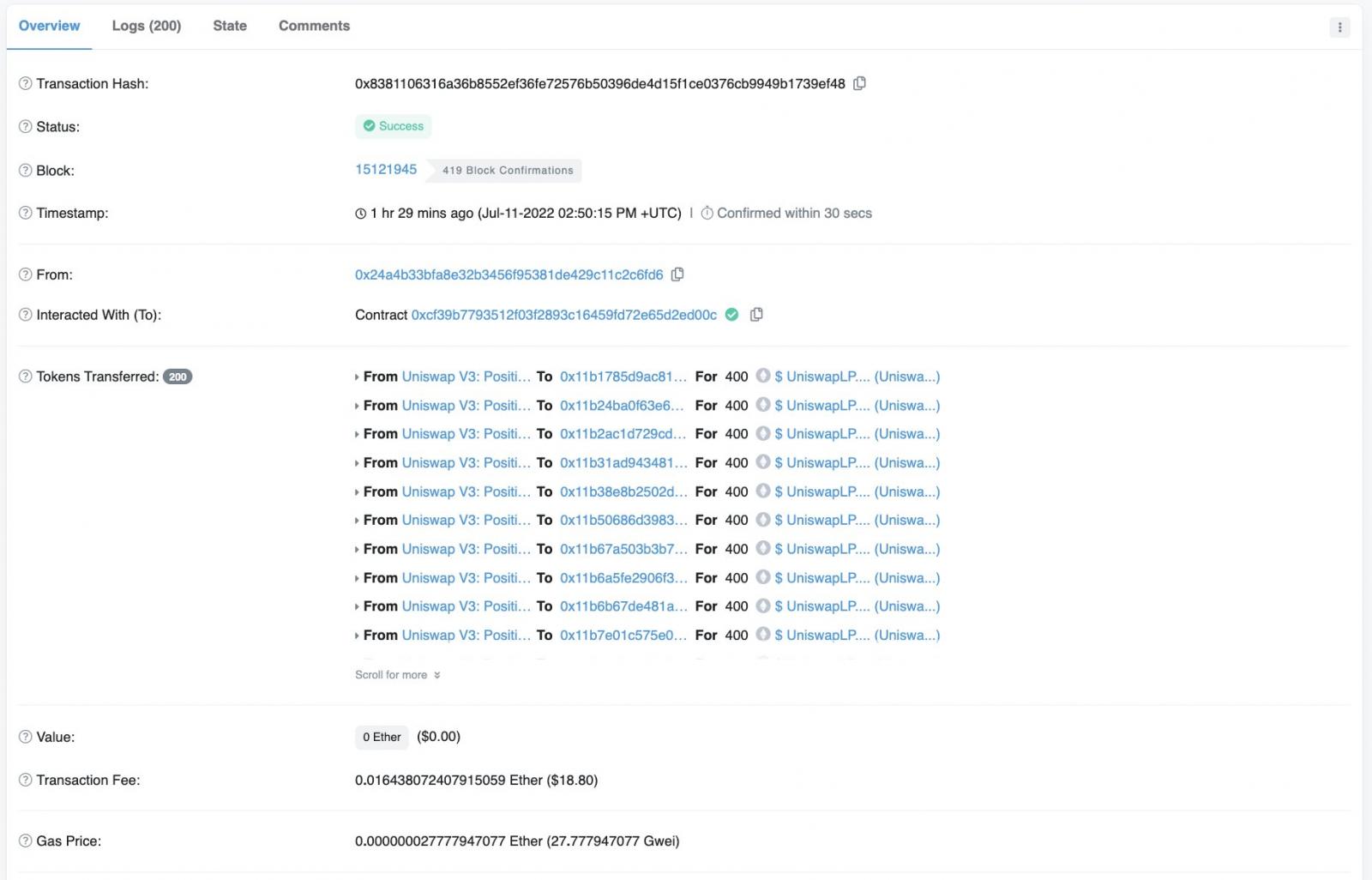
The goal was to re-direct the recipients to a scam website on the domain "uniswaplp[.]com," which impersonates the official Uniswap domain "uniswap.org."
The operator appeared as "Uniswap V3: Positions NFT" to the victims, thus tricking them into allowing the approval rights.
To understand more on how the scammers spoofed the sender's address, check out this detailed post by blockchain security expert Harry Denley.
In short, the attackers polluted the emit function of the contract with false data tricking the block explorer into displaying Uniswap as the sender, researchers at Check Point explain.
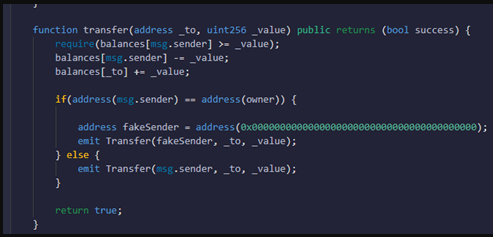
Since there's no validation between the actual sender's address and the emit function, the latter can be abused to spoof any entity in the transaction log.
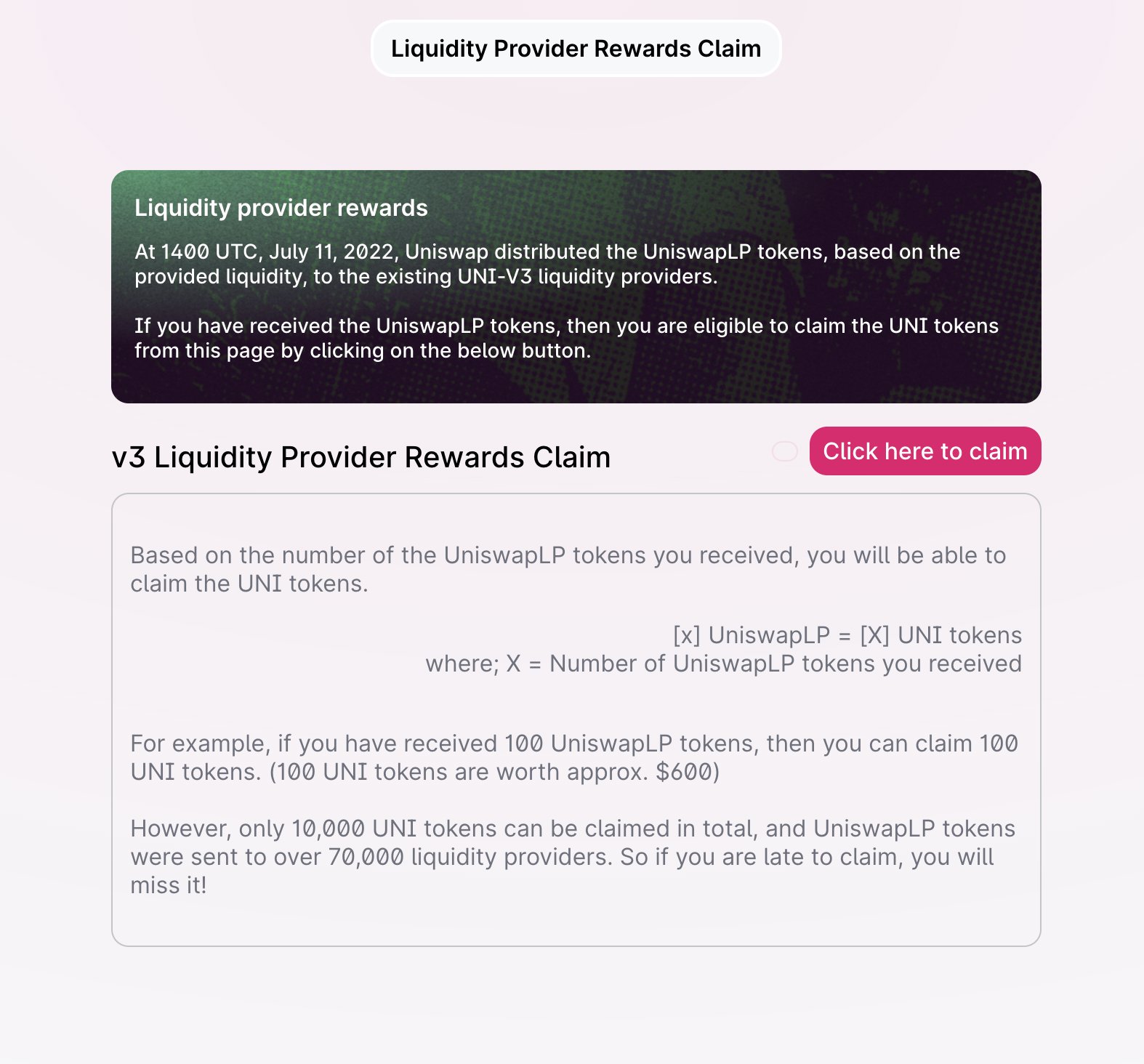
The users who pressed the "Click here to claim" button thinking they were about to receive their reward essentially granted the attackers full access to their assets.
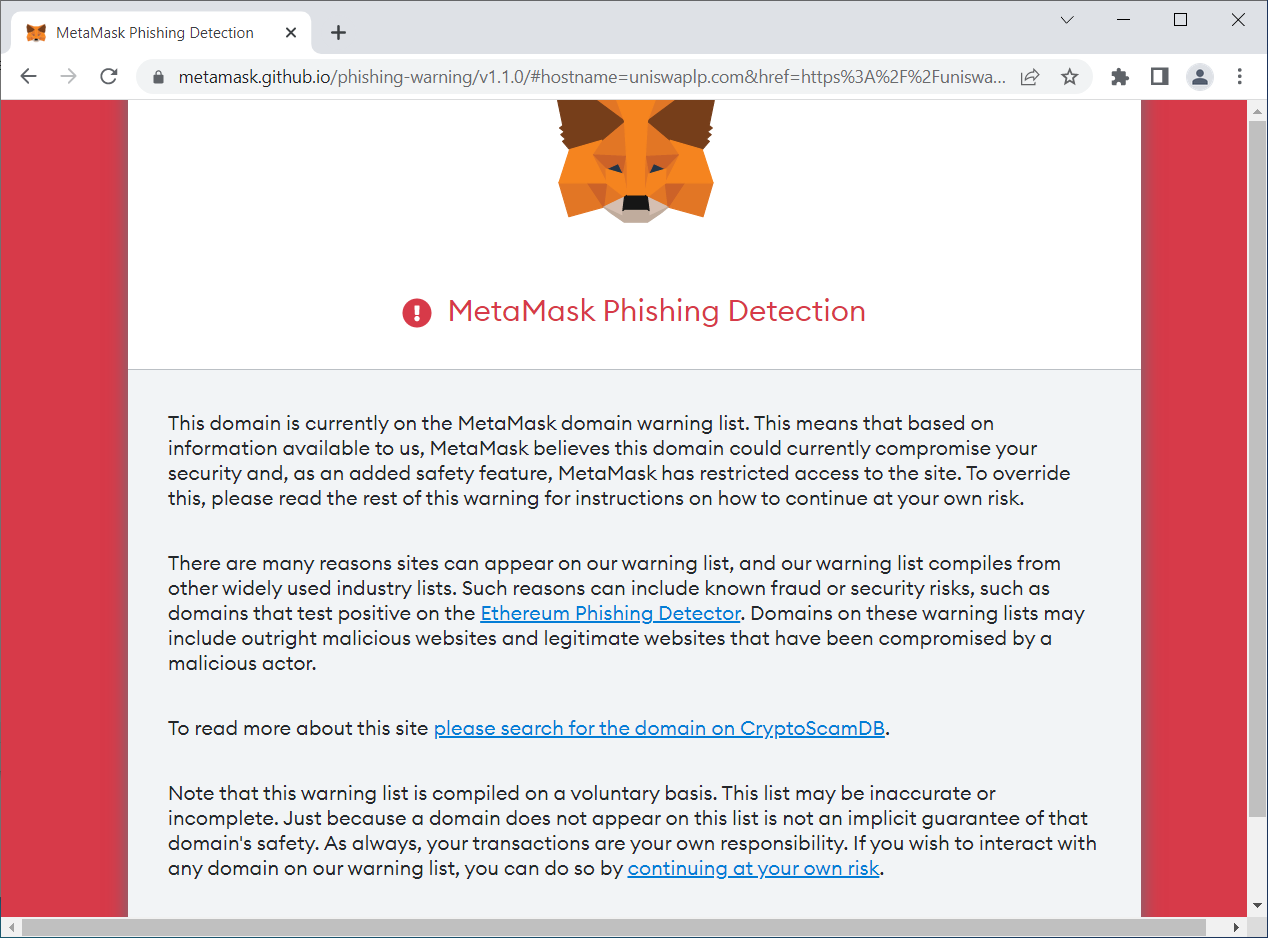
Software cryptocurrency wallet MetaMask has added to its warning list the domain used in the Uniswap phishing, thus preventing new users from getting scammed.
How to protect yourself
When receiving an airdrop, make sure to validate everything before clicking any buttons, starting with the domain name of the website you've landed on.
Before responding to promotional events or giveaways, users of digital assets should also check the platform's official website and social media channels that the offer is genuine.
Verifying the source of an airdrop is also a good way to avoid falling victim to scammers seeing to take control of transactions with a single click.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now