
Chinese hackers used a zero-day exploit for a critical-severity vulnerability in Sophos Firewall to compromise a company and breach cloud-hosted web servers operated by the victim.
The security issue has been fixed in the meantime but various threat actors continued to exploit it to bypass authentication and run arbitrary code remotely on multiple organizations.
Sophos Firewall 0day used for webshell drop
On March 25, Sophos published a security advisory about CVE-2022-1040, an authentication bypass vulnerability that affects the User Portal and Webadmin of Sophos Firewall and could be exploited to execute arbitrary code remotely.
Three days later, the company warned that threat actors were exploiting the security issue to target several organizations in the South Asia region.
This week, cybersecurity company Volexity detailed an attack from a Chinese advanced persistent threat group they track as DriftingCloud, which exploited CVE-2022-1040 since early March, a little over three weeks before Sophos released a patch.
The adversary used the zero-day exploit to compromise the firewall to install webshell backdoors and malware that would enable compromising external systems outside the network protected by Sophos Firewall.
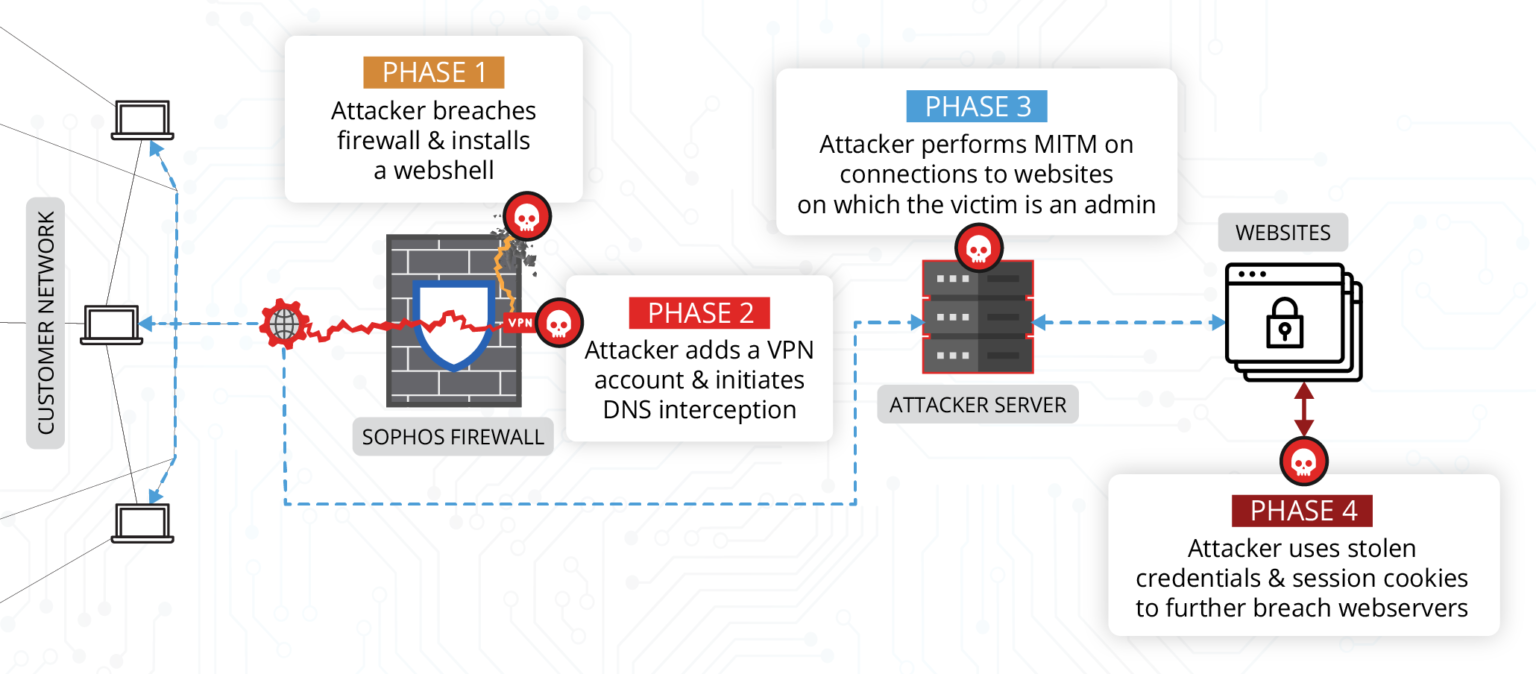
When Volexity started the investigation, the threat actor was still active and the researchers could monitor the steps of the attack, revealing a sophisticated adversary that made an effort to remain undetected.
The researchers note that the attacker tried to blend its traffic by accessing the installed webshell through requests to the legitimate file "login.jsp."
“At first glance, this might appear to be a brute-force login attempt instead of an interaction with a backdoor. The only real elements that appeared out of the ordinary in the log files were the referrer values and the response status codes” - Volexity
Digging deeper, the researchers found that the attacker was using the Behinder framework, which they believe was also used by other Chinese APT groups that exploited CVE-2022-26134 in Confluence servers.
Getting access to web servers
Apart from the webshell, Volexity found more malicious activity that ensured persistence and allowed the threat actor to take their attack further:
- Creating VPN user accounts and associating certificate pairs on the firewall for legitimate remote network access
- Writing “pre_install.sh” to ‘/conf/certificate/’
- "pre_install.sh" runs a malicious command to download a binary, execute it, then delete it from the disk
The researchers say that gaining access to Sophos Firewall was the first step of the attack, allowing the adversary to perform man-in-the-middle (MitM) activity by way of modifying DNS responses for specific websites managed by the victim company.
“This allowed the attacker to intercept user credentials and session cookies from administrative access to the websites' content management system (CMS)” - Volexity
It appears that the attacker was successful in this attempt as they accessed the CMS admin pages using stolen session cookies and installed the File Manager plugin for handling files on the website (upload, download, delete, edit).
Once they got access to the web server, DriftingCloud hackers installed PupyRAT, Pantegana, and Sliver - three malware families for remote access that are publicly available.
Detect similar attacks
Volexity assesses that the DrifitingCloud hacking group is sufficiently sophisticated to develop zero-day vulnerabilities, or well-funded enough to buy them.
Sophos provided hotfixes that address CVE-2022-1040 automatically as well as mitigations that help organizations using its firewall protect against exploiting the vulnerability.
To identify similar attacks, Volexity recommends deploying network security monitoring mechanisms that detect and log traffic from gateway devices.
The company also recommends using the auditd tool on Unix-based servers for easier investigating compromises. Vendors or perimeter devices should also provide methods for examining potential compromises.
Volexity also made available a set of YARA rules that could flag suspicious activity from this type of attack.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now