The owners of Polyfill.io have relaunched the JavaScript CDN service on a new domain after polyfill.io was shut down as researchers exposed it was delivering malicious code on upwards of 100,000 websites.
The Polyfill service claims that it has been "maliciously defamed" and been subject to "media messages slandering Polyfill."
Polyfill: "Someone has maliciously defamed us"
The Polyfill.io domain appears to have been shut down as of today by its registrar Namecheap.
The service owners have, however, relaunched the service on a new domain and claim that there are "no supply chain risks."
In a series of posts on X (formerly Twitter), the dubious CDN company has spoken out against allegations of it being involved in a large scale supply chain attack:
"We found media messages slandering Polyfill. We want to explain that all our services are cached in Cloudflare and there is no supply chain risk," writes Polyfill.
The service further claims that it has been "defamed" and dismissed that a risk exists from usage of its CDN:
Someone has maliciously defamed us. We have no supply chain risks because all content is statically cached. Any involvement of third parties could introduce potential risks to your website,
— Polyfill (@Polyfill_Global) June 26, 2024
but no one would do this as it would be jeopardize our own reputation.
We have already…
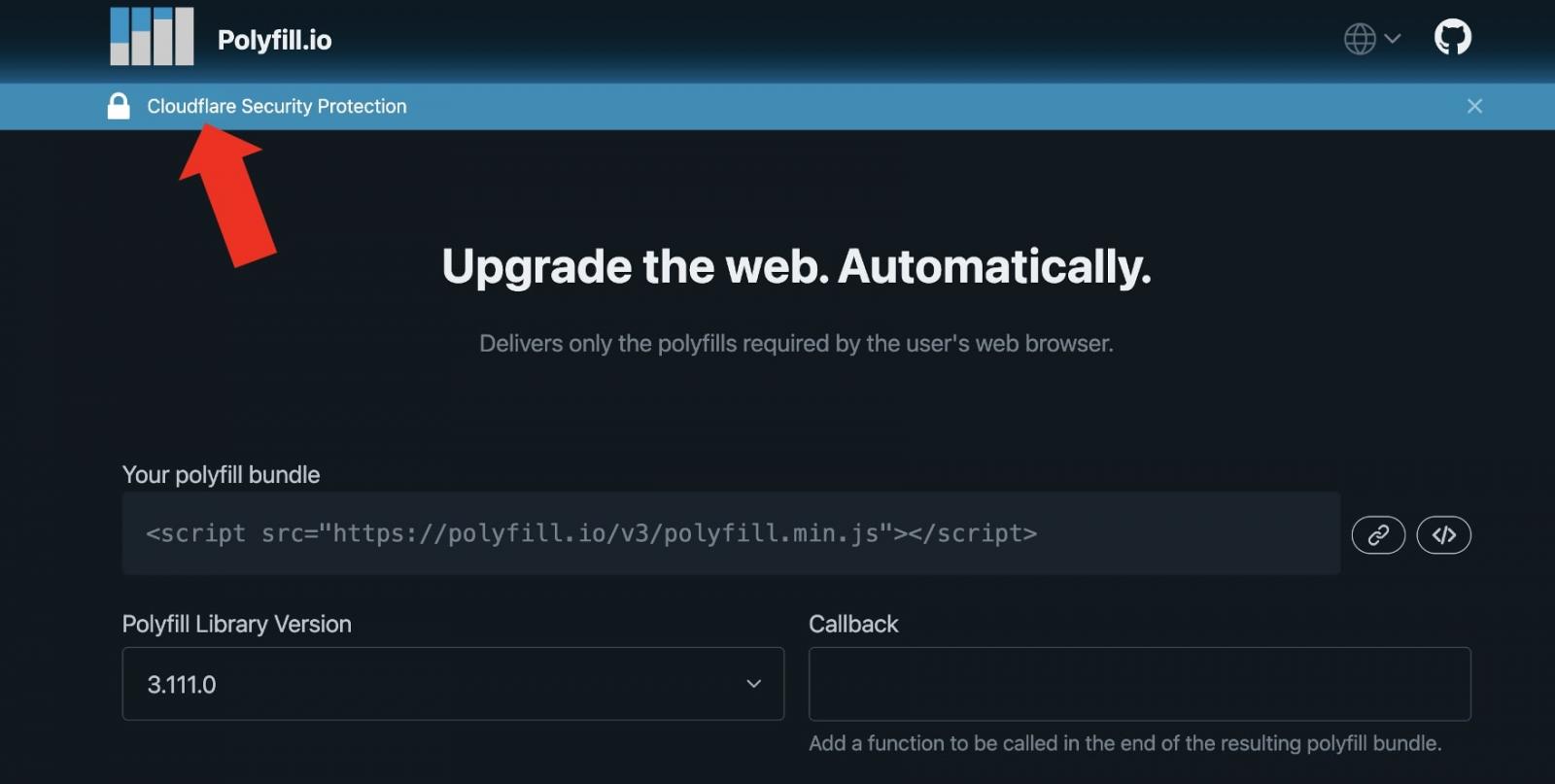
The service providers have relaunched the service on polyfill.com—also registered with Namecheap and fully functional at the time of test by BleepingComputer.
Trust no polyfill just yet
Despite Polyfill's lofty claims of being safe for use, however, facts and findings made by security practitioners prove otherwise.
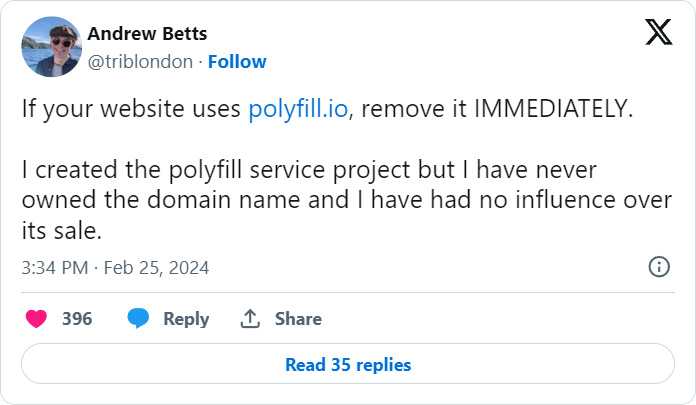
The original open source project, Polyfill was released for JavaScript developers to add modern functionality to older browsers that do not usually support such features. But, its creator, Andrew Betts never owned and had no association with the polyfill.io domain which provided Polyfill's code via a CDN:
In February, a Chinese entity named 'Funnull' bought polyfill.io and introduced malicious code in scripts delivered by its CDN.
Sansec researchers recently identified that the supply chain attack resulting from Polyfill.io's modified scripts had hit more than 100,000 websites. The domain would inject malware on mobile devices visiting websites that embedding code directly from cdn.polyfill[.]io.
Yesterday, cloud security company, Cloudflare also raised eyebrows on Polyfill.io's unauthorized use of the Cloudflare name and logo. It stated that Polyfill.io's failure to remove the "false statement" from their website despite being contacted by Cloudflare was "yet another warning sign that they cannot be trusted."
(BleepingComputer)
Cloudflare further corroborated Sansec's claims that code delivered by Polyfill.io's CDN was in fact redirecting users to sports betting sites and did so using a typosquatted domain name (googie-anaiytics[.]com) which was an intentional mispelling of the Google Analytics one.
Cloudflare co-founder and CEO, Matthew Prince also revealed that 4% of the internet, or tens of millions of websites used polyfill.io and called the aftermath from the attack "extremely concerning."
Furthermore, Google began notifying advertisers about this supply chain attack, warning them that their landing pages included malicious code and could redirect visitors away from the intended site without the website owner's knowledge or permission.
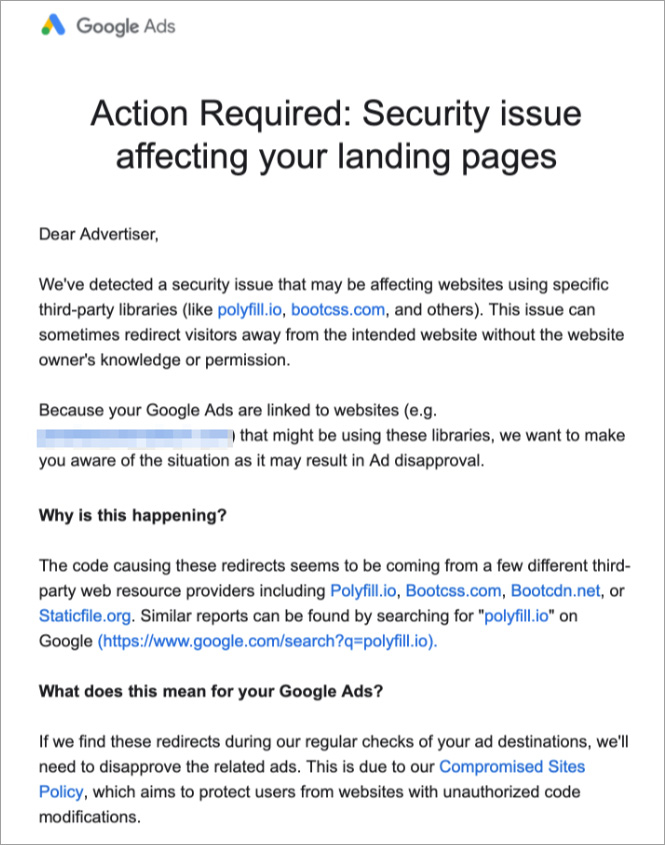
"The code causing these redirects seems to be coming from a few different third-party web resource providers including Polyfill.io, Bootcss.com, Bootcdn.net, or Staticfile.org," reads the email from Google.
"Similar reports can be found by searching for "polyfill.io" on Google (https://www.google.com/search?q=polyfill.io).
Simon Wijckmans, founder of web security service c/side, also advised against using the Polyfill.io CDN, stating that while Polyfill open source project was itself "solid," and could be self-hosted by anyone in a controlled environment, "the issue lies within the domain cdn.polyfill.io which should immediately be removed from your sites."
As such, websites and developers should refrain from using either polyfill.io or polyfill.com, and consider replacing existing usage of the service with safe alternatives set up by Cloudflare and Fastly.
Updates:
June 27th, 08:45 AM ET: Added copy of email from Google to advertisers and a reference to c/side blog post.
July 3rd, 02:09 AM ET: Corrected the typosquatted domain name spelling. We regret the error.



Comments
arby2024 - 2 days ago
"using a typosquatted domain name (google-anaiytics[.]com)"
FYI, It was actually googie-anaiytics[.]com
AxSharma - 2 days ago
Thank you. Corrected and added an update.