
Security researchers estimate that the financial impact of cryptominers infecting cloud servers costs victims about $53 for every $1 worth of cryptocurrency threat actors mine on hijacked devices.
This activity is generally attributed to certain financially motivated hacking groups, most notably TeamTNT, that perform large-scale attacks against vulnerable Docker Hubs, AWS, Redis, and Kubernetes deployments.
The threat actors load modified OS images containing XMRig, a miner for Monero (XMR), which is a privacy-oriented hard-to-trace cryptocurrency, and currently the most profitable CPU-based mining.
The mining programs use the hacked device's CPUs, so the threat actor generates income by hijacking hardware.
Compared to ransomware, rogue crypto mining is a lower-risk activity for the attacker, much less likely to attract law enforcement attention.
Estimating the damage
Researchers at Sysdig approximated the financial damage of cryptominers by looking into one of TeamTNT's largest campaigns, "Chimaera," which compromised over 10,000 endpoints.
The threat actors used XMRig-Proxy to hide wallet addresses from the compromised machines and make tracking even harder, but the analysts recovered a sample of 10 wallet IDs used in the campaign.
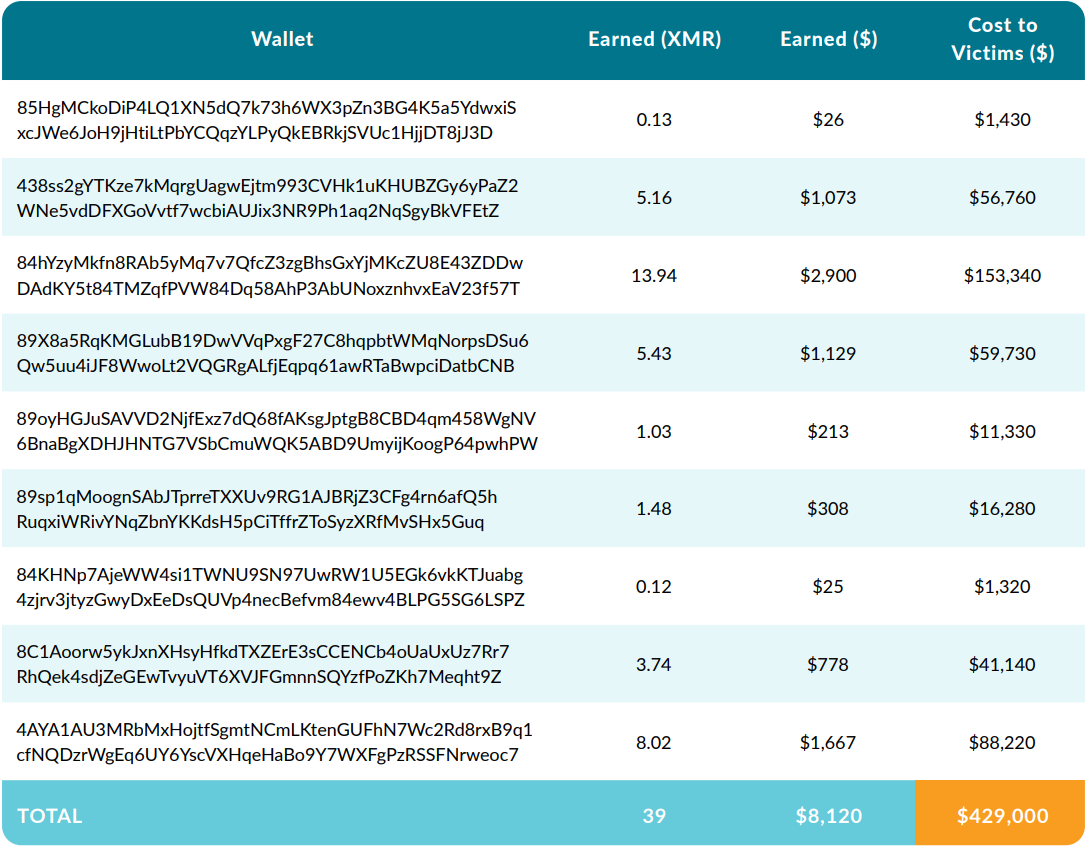
Collectively, these ten wallets held a total of 39 XMR, having a value equivalent to $8,120. However, Sysdig reports that the cost to the victim incurred from mining those 39 XMR is estimated to be $429,000 ($11,000 per 1 XMR).
"Better provisioned instances (such as c6a.8xl) will mine the coin faster, but the cost per hour scales roughly linearly with the amount of vCPUs," details Sysdig in the report.
"There are many possible configurations to increase the cost of an EC2 instance, such as adding additional RAM or storage, but $11,000 is the median cost across many different tested configurations."
The financial damage estimation does not consider amounts on unknown older wallets, the hardware damage impacting the server owner, potential online service interruptions caused by hogging processing power and the resulting business disruption, or the strategic changes firms had to make to sustain excessive cloud bills.
The figures presented in Sysdig's report underline the significance of defending against crypto mining threats by keeping cloud instances up to date and ensuring their configuration is secure.
Earlier this month, a report by AquaSec warned about a potential TeamTNT rebound into high-volume operations, employing a mix of known, renewed, and novel attack pathways targeting Docker servers with cryptominers.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now