Nayana, a web hosting provider based in South Korea, announced it is in the process of paying a three-tier ransom demand of nearly $1 million worth of Bitcoin, following a ransomware infection that encrypted data on customer' servers.
The ransomware infection appears has taken place on June 10, but Nayana admitted to the incident two days later, in a statement on its website.
Attackers asked for an initial ransom payment of 550 Bitcoin, which was worth nearly $1.62 million at the time of the request.
Company negotiated a smaller ransom payment
After two days of negotiations, Nayana staff said they managed to reduce the ransom demand to 397.6 Bitcoin, or nearly $1 million.
In a subsequent announcement, Nayana officials stated that they negotiated with the attackers to pay the ransom demand in three installments, due to the company's inability to produce such a large amount of cash in a short period of time.
On Saturday, June 17, the company said it already paid two of the three payment tranches. In subsequent announcements [1, 2], Nayana updated clients on the server decryption process, saying the entire operation would take up to ten days due to the vast amount of encrypted data.
The company said 153 Linux servers were affected, servers which stored the information of more than 3,400 customers.
Servers encrypted by Erebus Linux ransomware
According to Nayana, the name of this ransomware is Erebus. The name is the same with a ransomware family that appeared last year and resurfaced again in February 2017, but that ransomware targeted Windows computers.
This version — analysis here by AhnLab, Hauri, and Trend Micro — targets only Linux computers. It is unclear if the two Windows versions spotted previously are related to the Linux version that hit Nayana, or if this is just another case where crooks used the same name for their ransomware strain.
The ransomware encrypts the following file types:
tar, gz, tgz, taz, bz, tbz, bz2, lz, lzma, lz4, contact, dbx, doc, docx, jnt, jpg, mapimail, msg, oab, ods, pdf, pps, ppsm, ppt, pptm, prf, pst, rar, rtf, txt, wab, xls, xlsx, xml, zip, 1cd, 3ds, 3g2, 3gp, 7z, 7zip, accdb, aoi, asf, asp, aspx, asx, avi, bak, cer, cfg, class, config, css, csv, db, dds, dwg, dxf, flf, flv, html, idx, js, key, kwm, laccdb, ldf, lit, m3u, mbx, md, mdf, mid, mlb, mov, mp3, mp4, mpg, obj, odt, pages, php, psd, pwm, rm, safe, sav, save, sql, srt, swf, thm, vob, wav, wma, wmv, xlsb, 3dm, aac, ai, arw, c, cdr, cls, cpi, cpp, cs, db3, docm, dot, dotm, dotx, drw, dxb, eps, fla, flac, fxg, java, m, m4v, max, mdb, pcd, pct, pl, potm, potx, ppam, ppsm, ppsx, pptm, ps, pspimage, r3d, rw2, sldm, sldx, svg, tga, wps, xla, xlam, xlm, xlr, xlsm, xlt, xltm, xltx, xlw, act, adp, al, bkp, blend, cdf, cdx, cgm, cr2, crt, dac, dbf, dcr, ddd, design, dtd, fdb, fff, fpx, h, iif, indd, jpeg, mos, nd, nsd, nsf, nsg, nsh, odc, odp, oil, pas, pat, pef, pfx, ptx, qbb, qbm, sas7bdat, say, st4, st6, stc, sxc, sxw, tlg, wad, xlk, aiff, bin, bmp, cmt, dat, dit, edb, flvv, gif, groups, hdd, hpp, log, m2ts, m4p, mkv, mpeg, ndf, nvram, ogg, ost, pab, pdb, pif, png, qed, qcow, qcow2, rvt, st7, stm, vbox, vdi, vhd, vhdx, vmdk, vmsd, vmx, vmxf, 3fr, 3pr, ab4, accde, accdr, accdt, ach, acr, adb, ads, agdl, ait, apj, asm, awg, back, backup, backupdb, bank, bay, bdb, bgt, bik, bpw, cdr3, cdr4, cdr5, cdr6, cdrw, ce1, ce2, cib, craw, crw, csh, csl, db_journal, dc2, dcs, ddoc, ddrw, der, des, dgc, djvu, dng, drf, dxg, eml, erbsql, erf, exf, ffd, fh, fhd, gray, grey, gry, hbk, ibank, ibd, ibz, iiq, incpas, jpe, kc2, kdbx, kdc, kpdx, lua, mdc, mef, mfw, mmw, mny, moneywell, mrw, myd, ndd, nef, nk2, nop, nrw, ns2, ns3, ns4, nwb, nx2, nxl, nyf, odb, odf, odg, odm, orf, otg, oth, otp, ots, ott, p12, p7b, p7c, pdd, pem, plus_muhd, plc, pot, pptx, psafe3, py, qba, qbr, qbw, qbx, qby, raf, rat, raw, rdb, rwl, rwz, s3db, sd0, sda, sdf, sqlite, sqlite3, sqlitedb, sr2, srf, srw, st5, st8, std, sti, stw, stx, sxd, sxg, sxi, sxm, tex, wallet, wb2, wpd, x11, x3f, xis, ycbcra, yuv, mab, json, ini, sdb, sqlite-shm, sqlite-wal, msf, jar, cdb, srb, abd, qtb, cfn, info, info_, flb, def, atb, tbn, tbb, tlx, pml, pmo, pnx, pnc, pmi, pmm, lck, pm!, pmr, usr, pnd, pmj, pm, lock, srs, pbf, omg, wmf, sh, war, ascx, tif
... but it skips encryption for files found in the following folders:
/bin, /boot, /dev, /etc, /lib, /lib64, /proc, /run, /sbin, /srv, /sys, /tmp, /usr, /var, /.gem, /.bundle, /.nvm, /.npm
Once the encryption process ends, it drops two ransom notes named "_DECRYPT_FILE.html" and "_DECRYPT_FILE.txt" on the user's desktop.
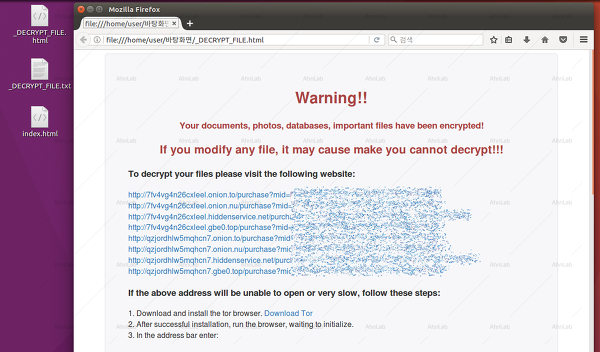
Payments are handled via two Tor onion sites:
7fv4vg4n26cxleel.onion
7fv4vg4n26cxleel.onion.to
7fv4vg4n26cxleel.onion.nu
7fv4vg4n26cxleel.hiddenservice.net
7fv4vg4n26cxleel.gbe0.top
qzjordhlw5mqhcn7.onion
qzjordhlw5mqhcn7.onion.to
qzjordhlw5mqhcn7.onion.nu
qzjordhlw5mqhcn7.hiddenservice.net
qzjordhlw5mqhcn7.gbe0.top
|
|
|
|
A Trend Micro analysis of the Nayana systems reveals endemic problems. It is no surprise that the hosting provider fell victim to this infection.
Currently, there is no information of the initial point of entry, but with such poor security practices, the hosting provider risks getting reinfected within hours if it will not patch its systems.
SHA256 hashes:
0b7996bca486575be15e68dba7cbd802b1e5f90436ba23f802da66292c8a055f
d889734783273b7158deeae6cf804a6be99c3a5353d94225a4dbe92caf3a3d48




Comments
GT500 - 7 years ago
They don't just need to patch their systems, they need to get all of their servers upgraded to newer versions of whatever Linux distro they use, and then properly secure those upgraded systems. With 153 servers, they're going to have to take their entire service offline for weeks (maybe longer) in order to get that done.