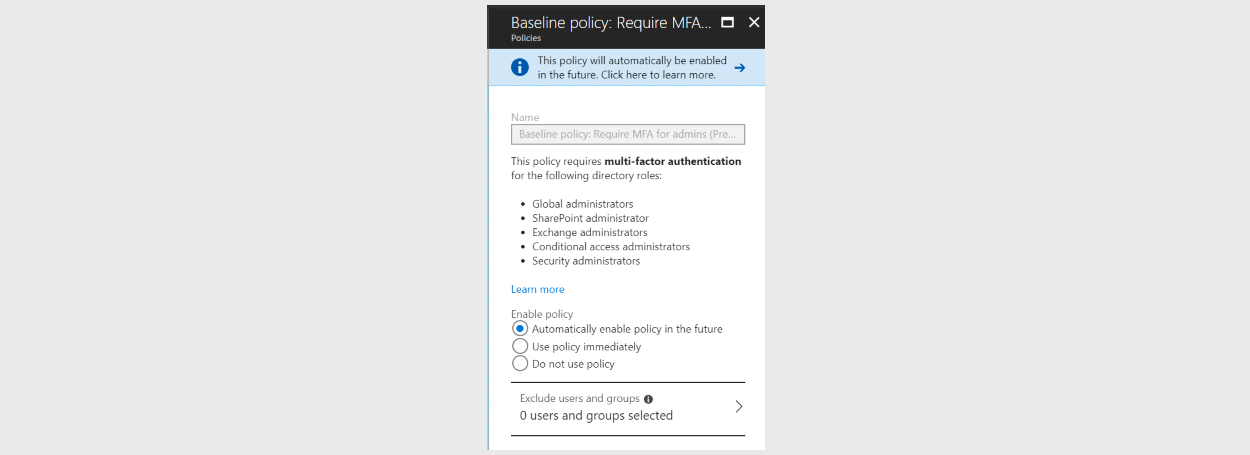
Microsoft will soon enable multi-factor authentication (MFA) for all high-privileged Azure AD accounts, the company said on Friday.
The MFA feature will be part of Microsoft Azure AD's "baseline policy," a set of security features that are enabled for accounts to support a minimum of security measures.
The "MFA-by-default for admin accounts" baseline policy is currently in a public preview phase, and any Azure AD customer can enable it by following the steps described here.
Microsoft says that once the feature goes out of "public preview" and into "general availability," the following Azure AD account types will be prompted to configure multi-factor authentication settings to access their accounts.
SharePoint administrator
Exchange administrator
Conditional access administrator
Security administrator
Azure AD multi-factor authentication options include:
SMS security code
Notification through mobile app
OATH verification code from mobile app
Azure AD tenants can opt out if it's an inconvenience
Azure AD tenants can opt out of using this baseline policy for their organization, if they wish to, albeit security researchers advise against it.
"Attackers who get control of privileged accounts can do tremendous damage, so it’s critical to protect these accounts first," said Alex Simons, Director of Program Management, Microsoft Identity Division.
#AzureAD baseline security policy for Admin accounts is now in public preview https://t.co/S0Cy8Wv6vo pic.twitter.com/3mL6qghRPM
— Alex Simons (@Alex_A_Simons) June 22, 2018
We already manually enable MFA for admin accounts, but this makes the whole process much easier and less prone to mistakes. Set and forget! #AzureAD #MFA https://t.co/E5WV7ncShq
— Gerbrand van der Weg (@gerbrandvdweg) June 22, 2018
Office365/Azure will soon force high-powered admin accounts to use 2FA, unless you specially go in and turn it off for your organization.
— SwiftOnSecurity (@SwiftOnSecurity) June 22, 2018
Good stuff. Good direction. https://t.co/jzMZtrRLxd
Third Azure AD feature launched last week
Last week, Microsoft also announced the public preview of two other Azure AD tools. The first is named Azure AD Password Protection and was designed to help customers eliminate easily guessable passwords from their setups.
The second is named Azure AD Smart Lockout and is a tool that detects brute-force attacks and temporarily locks access to the targeted accounts.
In 2016, Microsoft decided to ban users from using passwords that had been included in leaked lists of passwords that originated from data breaches at other companies.
At the time, Microsoft said its infrastructure handled over 13 billion authentications per day, of which 1.3 billion were for Azure AD accounts. Of these 13 billion, Microsoft said over 10 million authentication requests were malicious in nature.



Comments
sahanasharmaa - 5 years ago
Multifactor authentication (MFA) is a safety and security system that needs more than one method of authentication from objective categories of credentials to verify the user’s identity for a login or other transaction. This article gives a brief description of Multifactor authentication. I know a platform named Alcodes providing OTP services with multiple features.