
Two of today's biggest cloud service providers are now blocking a technique called "domain fronting" that has been used by websites and applications to avoid government-based censorship, but also by malware to secretly siphon stolen data to covert servers.
The first one to drop support for domain fronting was Google, at the start of April. Tor developers were the first ones to notice that Google App Engine had stopped working with domain-fronted services on April 13.
A Google spokesperson told the media at the time that Google never officially supported domain fronting in the first place, and that recent changes in its infrastructure had resulted in the feature ceasing to work.
Amazon follows Google and bans domain fronting as well
But last week, Amazon, too, announced that it would drop support for the same feature.
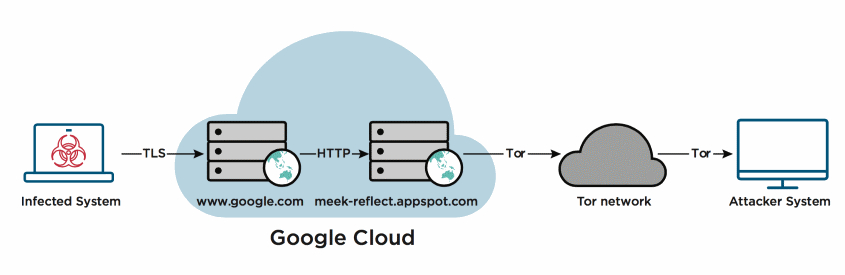
"Domain fronting" is a technique that app and website developers have used in the past to fool censorship tools. The technique relies on using an intermediary cloud server as a proxy for the real website. Connections are initiated for the proxy server, but the user is redirected to the actual website in a subsequent step.
But despite its simple scheme, domain fronting has allowed websites and apps to evade ISP-level censorship and traffic inspection tools for more than a decade.
Domain fronting has been used by apps like Signal, Tor-to-Web proxies, the GreatFire service to bypass China's Great Firewall, and lots of VPN providers to hide their servers' real locations.
Domain fronting became popular with malware operations
But despite the technique's use with legitimate apps trying to skirt government-based bans, the domain fronting had also slowly started to become quite popular on the malware scene, where cybercriminals had been using it to disguise the locations of command-and-control (C&C) servers and provide an extra layer of resiliency during law-enforcement takedown efforts.
The most famous use of domain fronting for a malware operation was by APT29, a cyber-espionage group suspected to be a branch of the FSB, one of Russia's intelligence agencies, according to cyber-security firm CrowdStrike.
In fact, Amazon cited the popularity of the domain fronting technique among malware operations as the main reason it decided to block its use on its infrastructure.
Based on the statements issued by both Amazon and Google, the banning of domain fronting has nothing to do with Russia's recent attempts to ban Telegram, during which Russia's communications watchdog ordered ISPs to block nearly 20 million IPs belonging to Amazon and Google's cloud services.
UPDATE: Shortly after this article's publication, the Signal team has published a blog post revealing that Amazon has threatened to kick the IM app off its servers if it doesn't stop using domain fronting.



Comments
forum11 - 6 years ago
So altruistic services using domain fronting to circumvent government censorship, spying, and assorted civil rights violations (in the case such rights even exist) are just out of luck I guess. Way to throw the baby out with the bath water, Google and Amazon. Or maybe they've decided there is more money to be made by working with oppressive states.
Cauthon - 4 years ago
Right, but do you really need to be as big as Google or Amazon to provide that kind of service for lots of Chinese students and grandmothers? Or is there something else that would work? Always seemed to me that even as big as the Chinese government is - or the Iranians etc - there are lots of people and lots of web sites and keeping it under control is going to be hard to do.