Security researchers from Pen Test Partners have discovered pretty glaring security flaws in Aga's line of smart ovens.
According to researchers, these flaws can be exploited via SMS messages. The reason appears to be that Aga management opted to use a GSM SIM module to control its devices, instead of the classic option of using a Wi-Fi module.
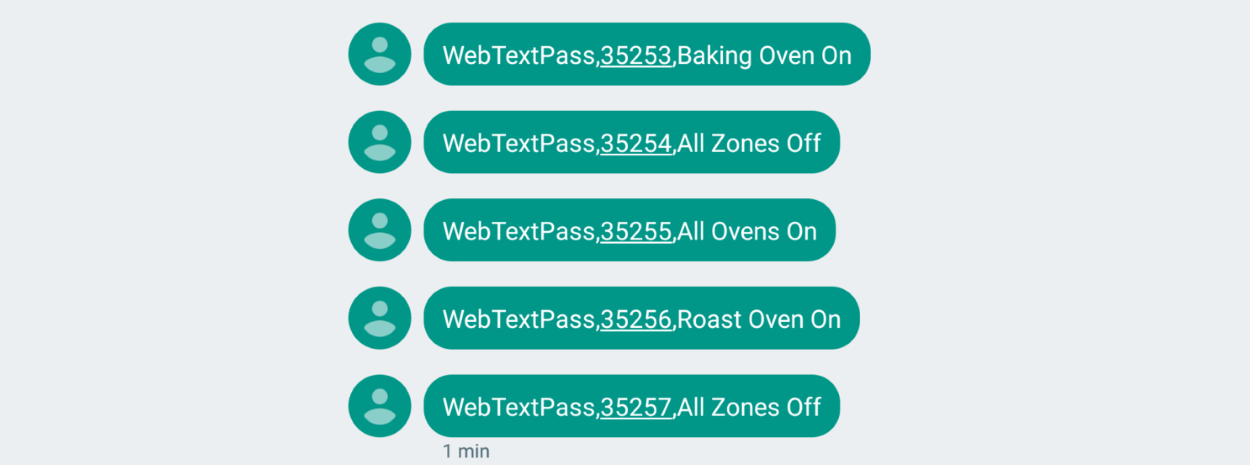
This SMS-based management feature allows Aga users to turn ovens on or off from remote locations by sending an SMS to their device.
Aga ovens can be hijacked via SMS messages
In this scenario, an attacker would need a victim's oven SMS number, but Pen Test Partners researchers say the web-based administration panel contains flaws that allow attackers to scrape for all active SIM card numbers assigned to Aga ovens.
There's no authentication involved with the SMS management commands, meaning anyone could send them, and mess around with people's "smart" ovens.
Professional cooking ovens, like the Aga iTotal Control, need hours of warming before reaching optimal cooking temperatures. While attackers could annoy oven owners by turning their ovens off, Pen Test Partners say that an ill-intent miscreant could also turn all known Aga ovens on, and cause a spike in electric energy consumption within an area, albeit this could be an exaggerated claim, as there would need to be thousands of these devices laying around.
Besides the non-authenticated SMS-based remote management feature, the research team also discovered other major problems with Aga's smart ovens.
Several other problems plague Aga's smart oven
For starters, the Aga web administration panel doesn't use HTTPS and forces users to use a five-digit password, one that's incredibly easy to brute-force.
Second, the Aga mobile app also works via HTTP, but even if developers used HTTPS, the app disables certificate validation on purpose, meaning attackers could use any SSL certificate to intercept traffic coming in and to the app.
By any stretch of the imagination, these aren't critical security flaws and should be easy to fix. The problem is that Aga representatives have been ignoring the research team, going as far as blocking on Twitter one of the researchers that was trying to inform the company of its security flaws.
Aga was unresponsive to security report
After spending two weeks attempting to alert the UK-based IoT manufacturer, Pen Test Researchers decided to go public with their findings yesterday.
Furthermore, Pent Test Partners say that the GSM SIM remote management module used for Aga's iTotal Control smart oven was created by a company called Tekelek, which also ships similar SMS management components for oil storage tanks, heating systems, process control and medical devices.
"These appear to be monitored using SMS, so I wonder where else this bizarre unauthenticated text messaging process might lead," said Ken Munro, Pen Test Partners expert.
At the time of writing, and following the public disclosure of the iTotal Control issues, Aga appears to have taken down its web-based administration portal, as Pen Test Partners initially suggested.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now