
A new wave of BazarCall attacks uses Google Forms to generate and send payment receipts to victims, attempting to make the phishing attempt appear more legitimate.
BazarCall, first documented in 2021, is a phishing attack utilizing an email resembling a payment notification or subscription confirmation to security software, computer support, streaming platforms, and other well-known brands.
These emails state that the recipient is being auto-renewed into an outrageously expensive subscription and should cancel it if they do not want to be charged.
However, instead of containing a link to a website, the email historically included a phone number to an alleged customer service agent of that brand, who may be contacted to dispute charges or cancel the subscription.
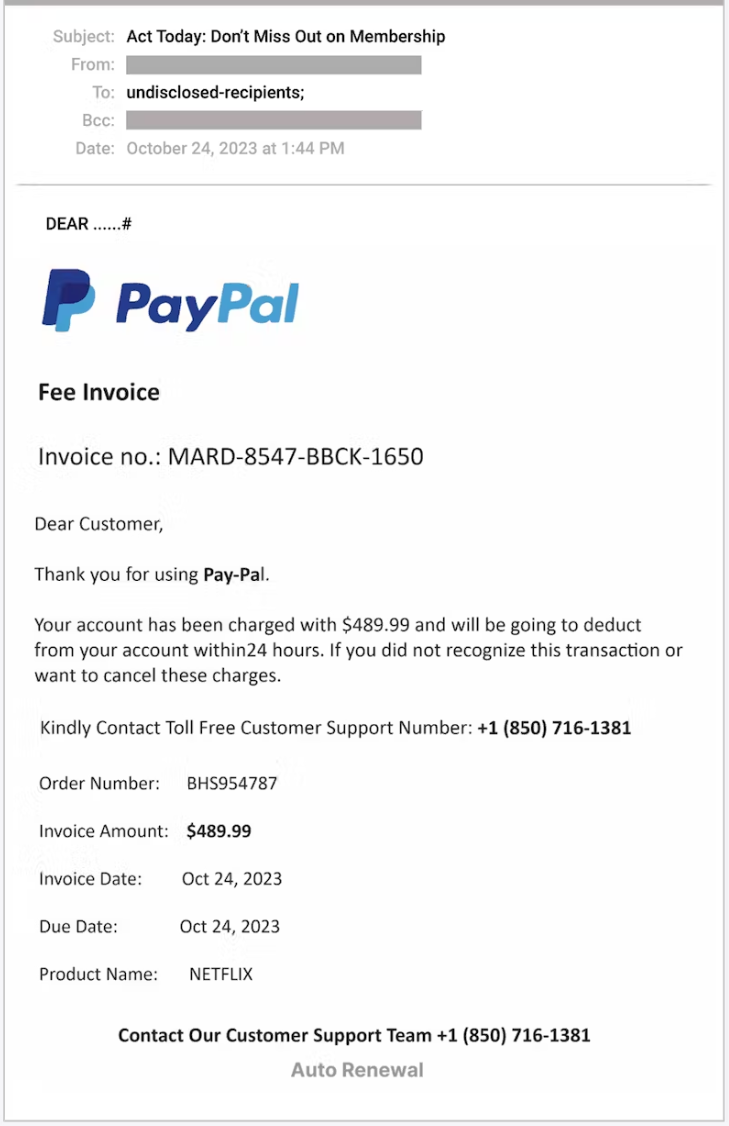
The calls are answered by a cybercriminal pretending to be customer support, tricking the victims into installing malware on their computers by guiding them through a deceptive process.
The malware is named BazarLoader, and as the name suggests, it is a tool for installing additional payloads on the victim's system.
Abuse of Google Forms
Email security firm Abnormal reports that it has encountered a new variant of the BazarCall attack, which now abuses Google Forms.
Google Forms is a free online tool that allows users to create custom forms and quizzes, integrate them on sites, share them with others, etc.
The attacker creates a Google Form with the details of a fake transaction, such as the invoice number, date, payment method, and miscellaneous information about the product or service used as bait.
Next, they enable the "response receipt" option in the settings, which sends a copy of the completed form to the submitted email address.
Using the target's email address, a copy of the completed form, which looks like a payment confirmation, is sent to the target from Google's servers.
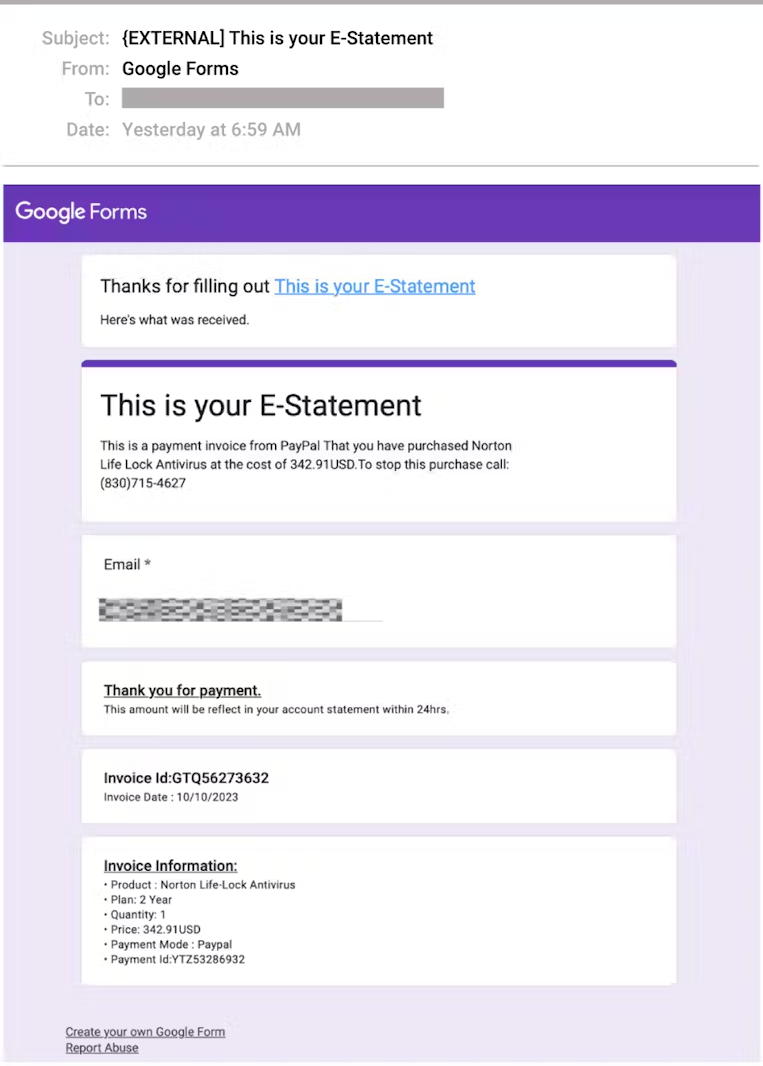
As Google Forms is a legitimate service, email security tools will not flag or block the phishing email, so delivery to the intended recipients is guaranteed.
Also, the fact that the email originates from a Google address ("noreply@google.com”) lends it additional legitimacy.
The invoice copy includes the threat actor's phone number, which recipients are told to call within 24 hours from the reception of the email to make any disputes, so the element of urgency is present.
Abnormal's report does not delve into the later stages of the attack. However, BazarCall was used in the past to gain initial access to corporate networks, usually leading to ransomware attacks.
Update 12/19 - A Google spokesperson has sent us the following comment:
Workspace has numerous layers of defenses to keep users safe. We are aware of the recent phishing attacks using Forms, and while they appear to be isolated to a small number of users, we are working to improve detection



Comments
ypicklesmom - 6 months ago
Just joined today and thankful this article popped up on my feed.
Working at a bank in disputes dept. THIS scam is starting to increase more and more to our customers unfortunately quite a few called the imposter.
I will now be later than I normally am to work all because I will be "here" reading previous and new News.