
Google has announced new, real-time scanning features for Google Play Protect that make it harder for malicious apps employing polymorphism to evade detection.
This represents a significant step toward enhancing safety for all Android users and aims to decrease malware infections on the platform.
Real-time code scans
Google's Play Protect platform is Android's built-in protection system for performing on-device scans for unwanted software and malware, powered by data derived from 125 billion daily scans.
The tool works for apps downloaded from Google Play, Android's official app store, and APKs (Android packages) downloaded from external sources and third-party app stores.
When Play Protect detects something suspicious on an app, it warns users not to proceed with its installation.
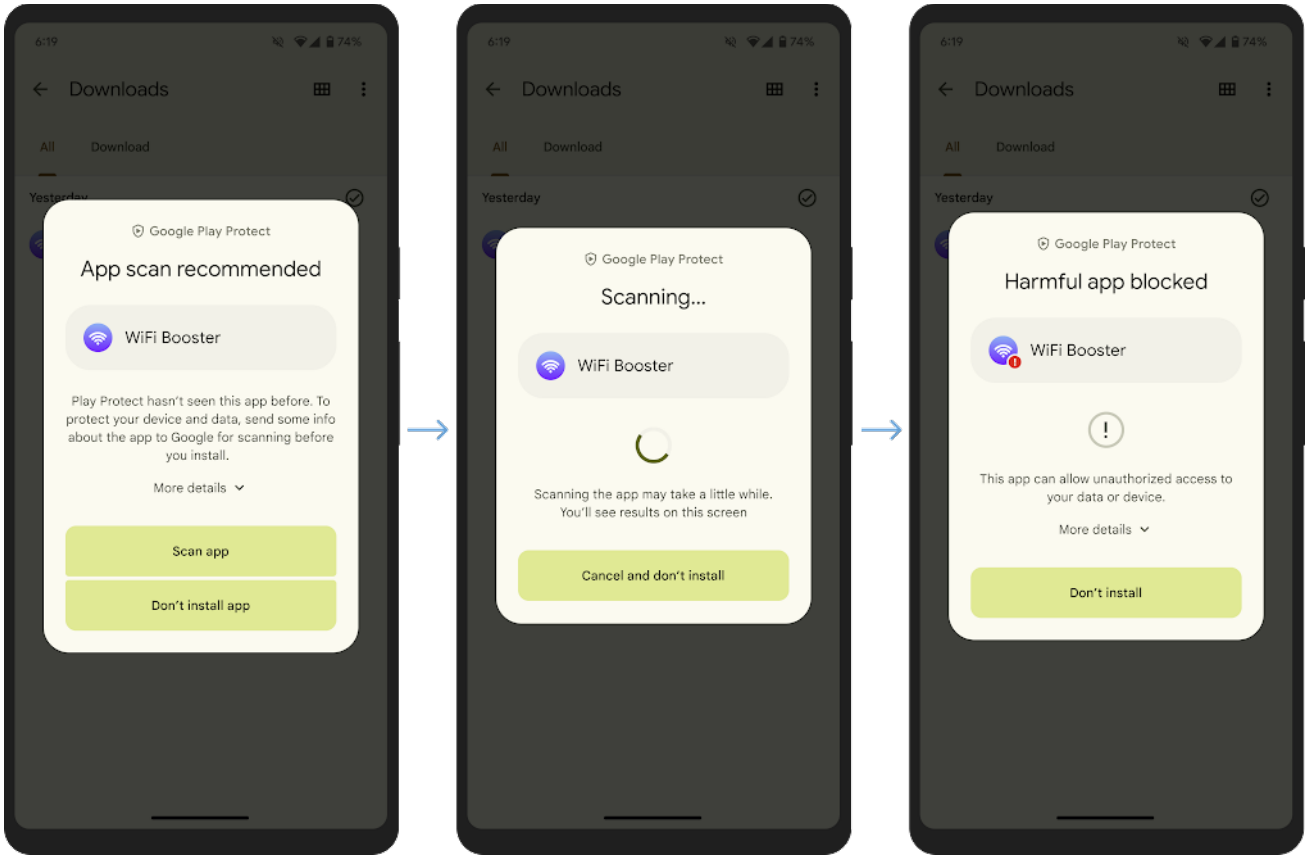
The problem is that authors of malicious apps promoted outside Google Play have resorted to AI and polymorphic malware that frequently alters identifiable information in a malicious program to bypass automated security platforms, making those scans ineffective.
Once the apps are installed on the user's device, they fetch additional code from an external resource, completing their malicious functionality at the post-check phase where there are no mechanisms to stop them.
However, Google told BleepingComputer after publishing that they re-review apps, including collecting signals of dynamic code loading to protect users when this behavior is found.
To address this gap, Google has now enhanced Play Protect with the ability to perform real-time scanning at the code level and adds a recommendation to perform scans on apps that haven't been scanned before.
The scanning will extract signals from the app, sending them to the Play Protect backend infrastructure for an in-depth code-level analysis, returning a result on the app's safety.
"Our security protections and machine learning algorithms learn from each app submitted to Google for review, and we look at thousands of signals and compare app behavior," explains Google in a press release.
"Google Play Protect is constantly improving with each identified app, allowing us to strengthen our protections for the entire Android ecosystem."
The enhanced Play Protect scanner will leverage static analysis, alongside heuristics and machine learning, to identify patterns indicative of malicious activity. The extracted signals from the app serve as key inputs for its AI-driven analysis.
That being said, there might still be some malicious apps that can slip past the new system by adding long delays before malicious code is downloaded or other behavior.
However, the amount of undetected malware should be reduced by this new system, at least until malware authors can adjust their techniques to trick or bypass these scans.
The real-time code-level scan on Google Play Protect has already been made available in India and other select countries and will be gradually rolled out worldwide in the upcoming months.
Play Protect works with and is regularly updated on the majority of Android devices, including Android 5 and later.
This allows the security system to be regularly updated independently of the monthly Android updates release.
Update 10/18/23: Added some clarifications from Google.



Comments
FizzyDizzy - 8 months ago
Nice in theory. I received an Amazon Fire stick recently. I chose to set it up via QR code. The QR code opened Brave browser. A few steps later it asked for credit card details. Big companies are in the habit of asking for credit cards to configure free things. I didn't think long enough fed it what it asked for. It said there was a problem, asking for re-input. Like a fool, I gave it an alternative CVC. This time the non-dynamic CVC. My phone popped up two messages from my bank about declined payments. The penny dropped. Let's rule out a genuine credit card check (some companies withdraw then refund when setting things up).
I lost a lot of time contacting the bank and Amazon. Amazon confirmed (eventually) they did not try to deduct a charge.
Back to the phone. I tested another QR code read. Brave browser opened and requested credit card details. Winner, winner, chicken dinner. I scanned the phone via play store, play protect. "No harmful apps found", it said. We know that's wrong. So, out went a highly rated QR scanner and Brave were replaced. The next QR scan behaved as it should, the replacement browser opened and behaved as it should.
I am a PC user and use the phone browser (you could count my history on one hand after a few years) and a QR scanner even less. I don't use the mail app at all. I've never clicked a link in the phone browser. In other words, my chance of bad habits installing malware are miniscule. The Fire device came direct from Amazon and arrived in a sealed state. things are pointing to the bad app coming via a play store update. Amazon are supposed to check store apps. Irrespective, A scan did not detect an issue when I knew there was malware on my phone.
So, how will a Google 'real time' scan do anything more than instill a false sense of security in users, which I suspect led to my problem?
BTW. No cash lost and I just received a declined attempt to use my now replaced credit card.
NoneRain - 8 months ago
Your phone was infected m8.
There are a lot of ways to compromise your device, including downloading unknown apps from App Store.
Play Protect has being better than nothing, but that's it. Their results against malware are as poor as them can get. They basically have success blocking already well-known malicious apps.
To protect your phone, and any other device:
1 - Keep it updated with the last security fixes (OS/Apps).
2 - Have a good antimalware installed.
3 - Avoid risky stuff (apps from unknown developers, received links/files, access unknown websites, connect to open/shared WIFI, etc).
4 - Have certain about what you're doing, if not, don't do it.
FizzyDizzy - 8 months ago
Thanks for the reply.
My work involved PC and laptop support over a lot of years. I disinfected many. My eyesight is not strong so I tend to avoid the phone in favor of the large screen PC and follow the rules of safe hex well (haven't had genuine malware on PC since naive days of 1990s and then only once). Everything else has been PUP, PUM or riskware.
On the phone:
1) Updated religiously (and an app update is where I think the malware came from). I use few apps and all are well-known, if not broadly then in my country.
2) I tried a variety of malware detectors, albeit after manual removal of suspect apps . None found m8. My phone still seems to churn through battery noticeably faster than it was about two month ago despite 'force stop' of everything possible other than when notification is wanted (e.g. banking app).
3) I do anything that may be risky AND needs to be checked in a sandbox on PC.
4) Yes, I rushed it and made a mistake.