
With the Coronavirus pandemic in full swing, threat actors are torn about how they should operate during the pandemic, and like everyone else, are also seeing a downturn in the underground hacker marketplace.
In mid-March, BleepingComputer asked numerous ransomware operators whether they would stop targeting health care companies during the Coronavirus pandemic.
Some operators stated they would no longer target healthcare organizations during the pandemic and other ransomware operators did not respond and continue to target hospitals.
Just like the ransomware operators, threat actors are also split on how they should operate target the Coronavirus pandemic in their attacks.
Threat actors split on using Coronavirus-themed attacks
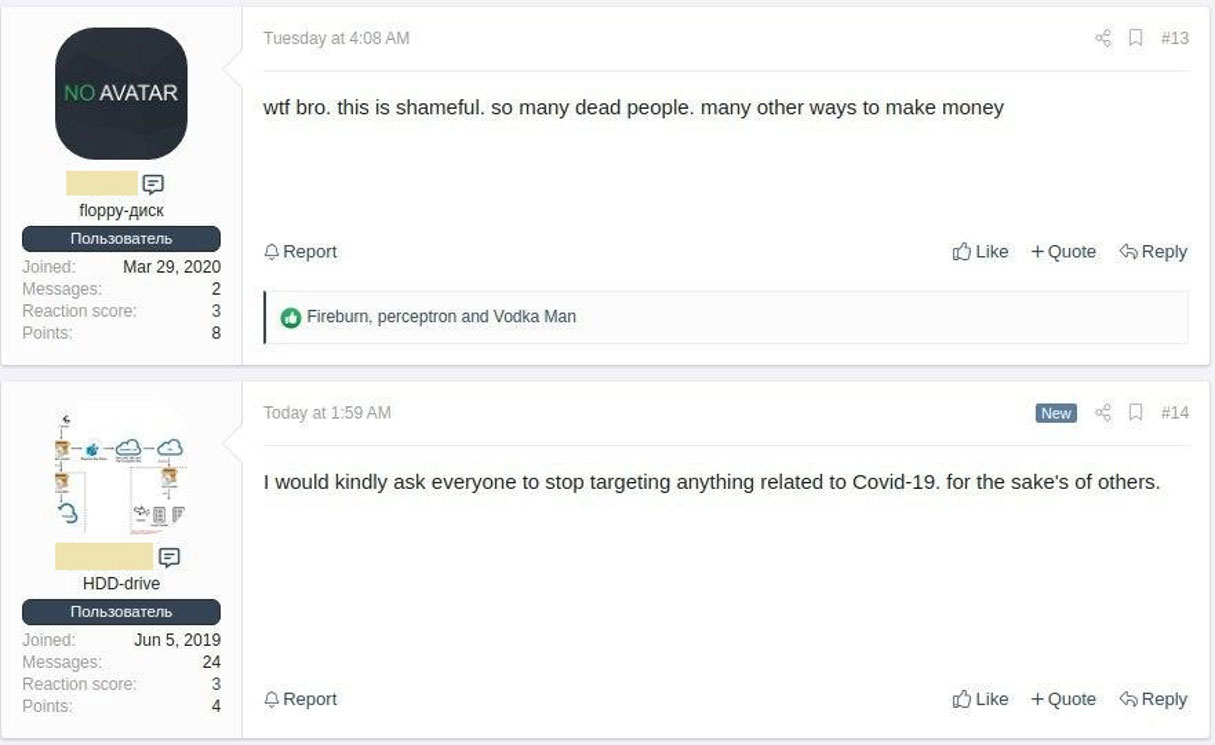
While we have definitely seen an increase in attacks using Coronavirus themes and lures, a new report by cybersecurity firm Group-IB indicates that some threat actors feel that it is morally wrong to exploit COVID-19 in their attacks.
"Group-IB’s Threat Intelligence team has also detected a number of underground forum posts by users who urge others to stop exploiting COVID-19 for malicious purposes," the security researchers stated in their report.
Source: Group-IB
With the threat of illness not only affecting attackers, but also their family and loved ones, this may cause hackers to avoid Coronavirus-related attacks or show more compassion to those who are affected.
Unfortunately, this is not the first time the hacker community disliked a particular attack or threat and nothing came out of it.
For example, when ransomware first became active, some threat actors and hacker forum administrators disliked this new type of cyberattack, yet we see further attacks daily.
Hacker economy takes a hit during the Coronavirus pandemic
There are very few people, companies, or even hackers who have not been affected economically by the Coronavirus pandemic whether it be a loss of a job, loss of customers, or simply being shut down due to shelter-in-place orders.
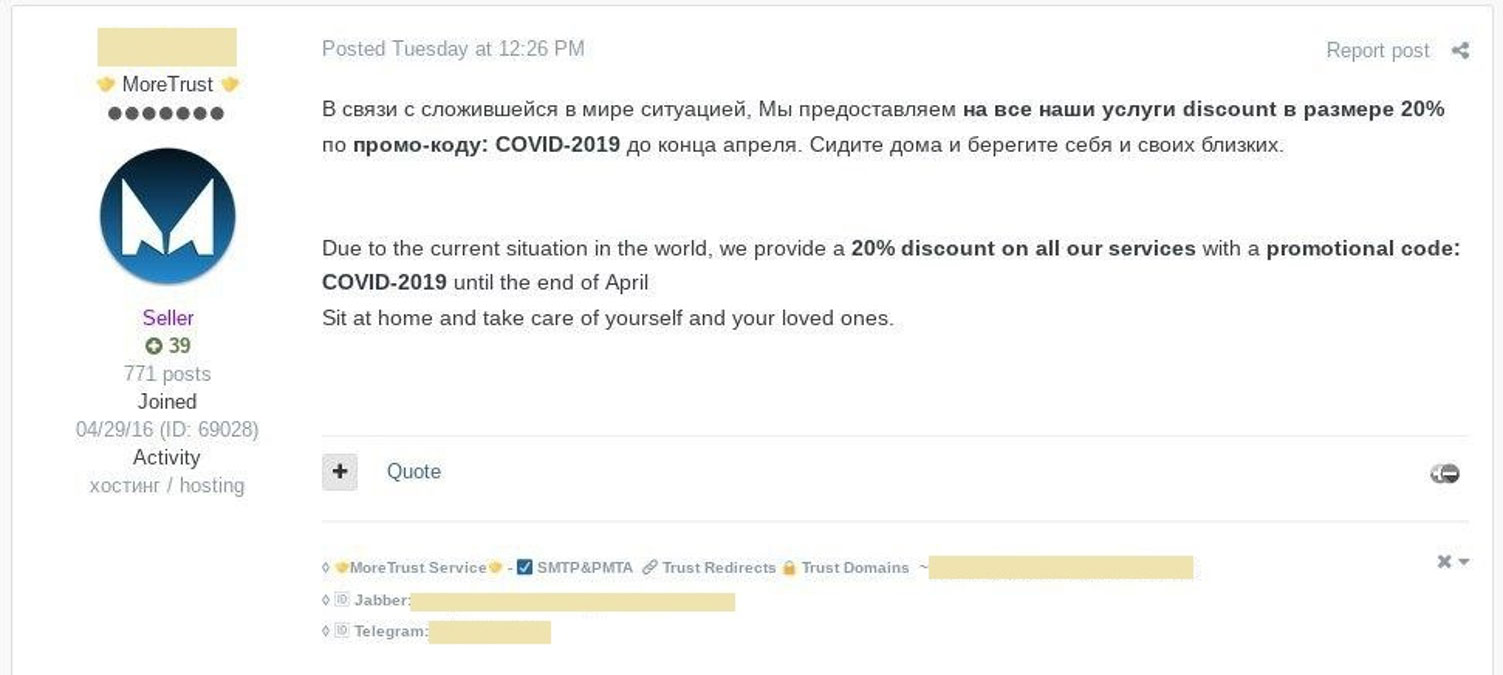
According to forums posts seen by Group-IB, hackers are also seeing a downturn in the underground hacker marketplaces and have begun to offer discounts on their services.
For example, the below image shows a threat actor who sells spamming and domain registration services offering a 20% discount on their services to stimulate the hacker economy.
Source: Group-IB
Group-IB has seen more than 500 hacker forum posts where threat actors are offering similar discounts for distributed denial of service (DDoS) attacks, spam attacks, and other services.
This could cause hackers to increase their attacks to try and make up for lost revenue.
“We predict an increase in the number of cyberattacks on unprotected home networks used by employees who have switched to remote work as the virus spreads offline. Corporate security teams should reassess their approach to securing corporate digital space by strengthening their perimeter, which now includes employees’ home devices. A single employee who opens a malicious file from an undetected phishing email could jeopardize the whole company’s operations,” Group-IB warns.
Due to this, everyone needs to stay vigilant and be on the lookout for phishing emails, attacks on home routers, and to make sure their software and operating system have the latest security updates installed.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now