
Purchased a car from Volkswagen in the last 20 years? If you did, chances are a group of researchers can now unlock your vehicle using a new wireless hack.
At the 25th Usenix Security Symposium in Austin, Texas, researchers Flavio D. Garcia and David Oswald along with colleagues from the University of Birmingham and the German engineering firm Kasper & Oswald will deliver a presentation entitled, Lock It and Still Lose It —on the (In)Security of Automotive Remote Keyless Entry Systems.
In it, they'll unveil two security vulnerabilities that together threaten the security of 100 million vehicles made by Volkswagen, Ford, and other well known car manufacturers.
The first vulnerability allows attackers to gain access to a Volkswagen car via a three-step process. The easy part comes first. Using a cheap radio receiver, actors intercept a single press of a remoteless key fob to intercept a radio signal sent to a target vehicle.
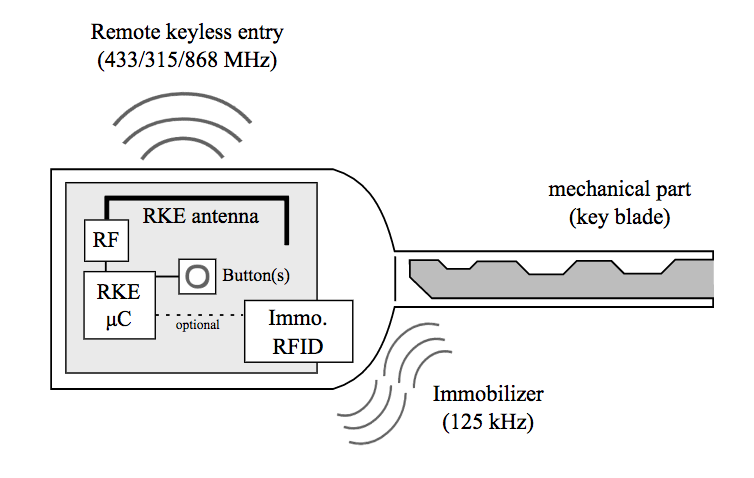
Next, they apply their reverse engineering skills to an unnamed component Volkswagen internal network, all in search of a single cryptographic key that is shared among nearly all vehicles made by the German car manufacturer.
Using those two elements, an attacker can essentially clone the key fob to unlock the vehicle.
None of that is particularly easy to pull off. An attacker has to be within 300 feet of the car, and even then, they need to find the correct component in Volkswagen's internal network.
But it could be worth it for a bad actor. Nearly 100 million cars sold by Volkswagen use just four cryptographic keys, which means attackers could use the same key across tens of millions of vehicles.
As the researchers explain in their research paper (PDF), finding a cryptographic key truly unlocks more doors than one:
"With the knowledge of these keys, an adversary only has to eavesdrop a single signal from a target remote control. Afterwards, he can decrypt this signal, obtain the current UID and counter value, and create a clone of the original remote control to lock or unlock any door of the target vehicle an arbitrary number of times."
 The second vulnerability involves a cryptographic scheme called HiTag2, which is used in millions of vehicles made by several different car manufacturers. Attackers can allegedly use a radio setup to intercept eight codes sent from a key fob to a target vehicle. Using those codes, the actors can get to work breaking the scheme.
The second vulnerability involves a cryptographic scheme called HiTag2, which is used in millions of vehicles made by several different car manufacturers. Attackers can allegedly use a radio setup to intercept eight codes sent from a key fob to a target vehicle. Using those codes, the actors can get to work breaking the scheme.
Garcia, Oswald, and their colleagues found they could break the code in as little as one minute.
This is not the first time researchers have demonstrated automobile-related vulnerabilities. In the summer of 2015, three Jeep owners filed a lawsuit against Chrysler after two researchers demonstrated they could turn on a Jeep's windshield wipers and radio, disable the vehicle’s brakes, and remotely drive the car into the ditch after exploiting a vulnerability in the Uconnect system.
That demonstration in part led the FBI to issue a public service announcement about the threat of vehicle hacking. Security companies have also published their own research on how attackers could potentially compromise a vehicle using hacking techniques.
At this time, there is no way for VW owners to protect themselves against these two vulnerabilities. Indeed, the car manufacturer would need to patch or replace every key fob it's produced in the past 20 years to create an appropriate fix--something which is utterly impossible.
With that in mind, as the researchers openly admit:
"[T]he only remaining (yet impractical) countermeasure is to fully deactivate or at least not use the [remote keyless entry] functionality and resort to the mechanical lock of the vehicle."



Comments
BigAlf - 7 years ago
"Volkswagen owns: Audi, Bentley, Bugatti, Lamborghini, Porsche, and overseas-brands SEAT and Skoda."
RIP
BinaryHedgehog - 7 years ago
I've never trusted keyless locks, and this proves my suspicion was right. It's much more comforting to have the only way into the car is to have a physical key.