
Hackers working for the Main Directorate of the General Staff of the Armed Forces of the Russian Federation, more commonly known as the GRU, have been targeting Android devices in Ukraine with a new malicious framework named ‘Infamous Chisel.
The toolkit provides hackers backdoor access through a service hidden in The Onion Router (Tor) anonymity network, lets them scan local files, intercept network traffic, and exfiltrate data.
The malware was first highlighted in a warning from the Ukrainian Security Service (SSU) earlier this month about efforts from the Sandworm hacking group to penetrate military command systems.
Reports today from the UK National Cyber Security Center (NCSC) and the US Cybersecurity and Infrastructure Security Agency (CISA) dive deeper into the technical details of Infamous Chisel, showing its capabilities and sharing information that can help defend against it.
Infamous Chisel details
The NCSC describes Infamous Chisel as "a collection of components which enable persistent access to an infected Android device over the Tor network, and which periodically collates and exfiltrates victim information from compromised devices."
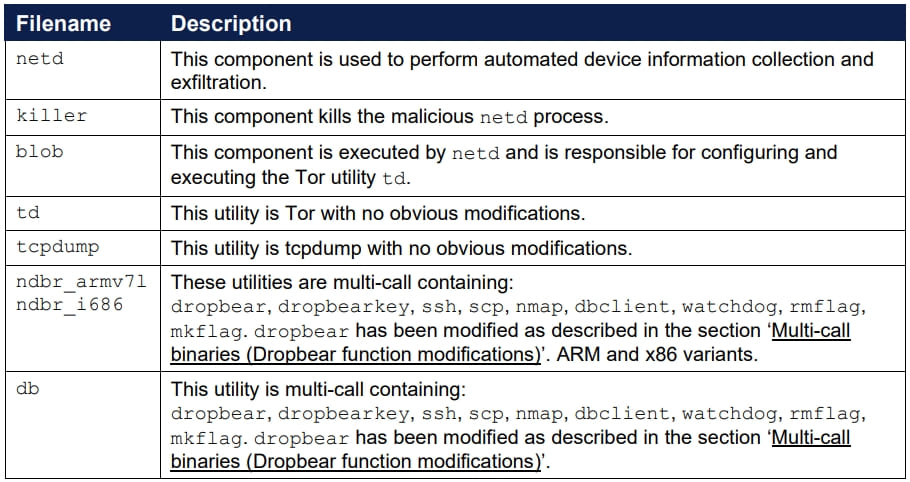
Once it infects a device, the primary component, ‘netd,’ which controls a set of commands and shell scripts, replaces the legitimate netd Android system binary to achieve persistence.
The malware targets Android devices and scans them to locate information and applications related to the Ukrainian military to send it to the attacker's servers.
A hidden file (“.google.index”) keeps track of the files sent to the hackers using MD5 hashes to prevent duplicate data. The system’s limit is 16,384 files, though, so duplicates are sent beyond that point.
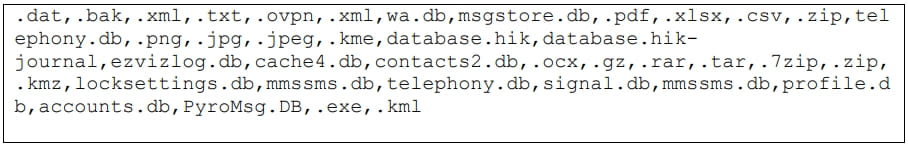
Infamous Chisel targets the file extensions in the image below and the directories it scans include the device’s internal memory and any SD cards available.
Android's /data/ directory is scanned for applications like Google Authenticator, OpenVPN Connect, PayPal, Viber, WhatsApp, Signal, Telegram, Gmail, Chrome, Firefox, Brave, Microsft One Cloud, Android Contacts, and many more.
The malware can also gather hardware information, probe the local area network for open ports and active hosts, and give attackers remote access via SOCKS and an SSH connection passed through a randomly generated .ONION domain.
File and device data exfiltration takes place every 86,000 seconds, which is one day, LAN scanning takes place every two days, and the most critical military data are siphoned much more frequently, every 600 seconds, which translates to ten minutes.
Configuration and execution of Tor services that facilitate remote access happens every 6,000 seconds, and a network connectivity check onto the “geodatatoo[.]com” domain occurs every 3 minutes.
The NCSC notes that Infamous Chisel isn’t particularly stealthy and appears to aim at quick data exfiltration and pivoting to more valuable military networks.
The agency says that the toolkit's components are not particularly sophisticated (low to medium complexity) and they seem to have been developed "developed with little regard to defence evasion or concealment of malicious activity."
NCSC's report includes a set of indicators of compromise, rules and signatures for detection



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now