
Security researchers discovered two malicious file management applications on Google Play with a collective installation count of over 1.5 million that collected excessive user data that goes well beyond what's needed to offer the promised functionality.
The apps, both from the same publisher, can launch without any interaction from the user to steal sensitive data and send it to servers in China.
Despite being reported to Google, the two apps continue to be available in Google Play at the time of publishing.
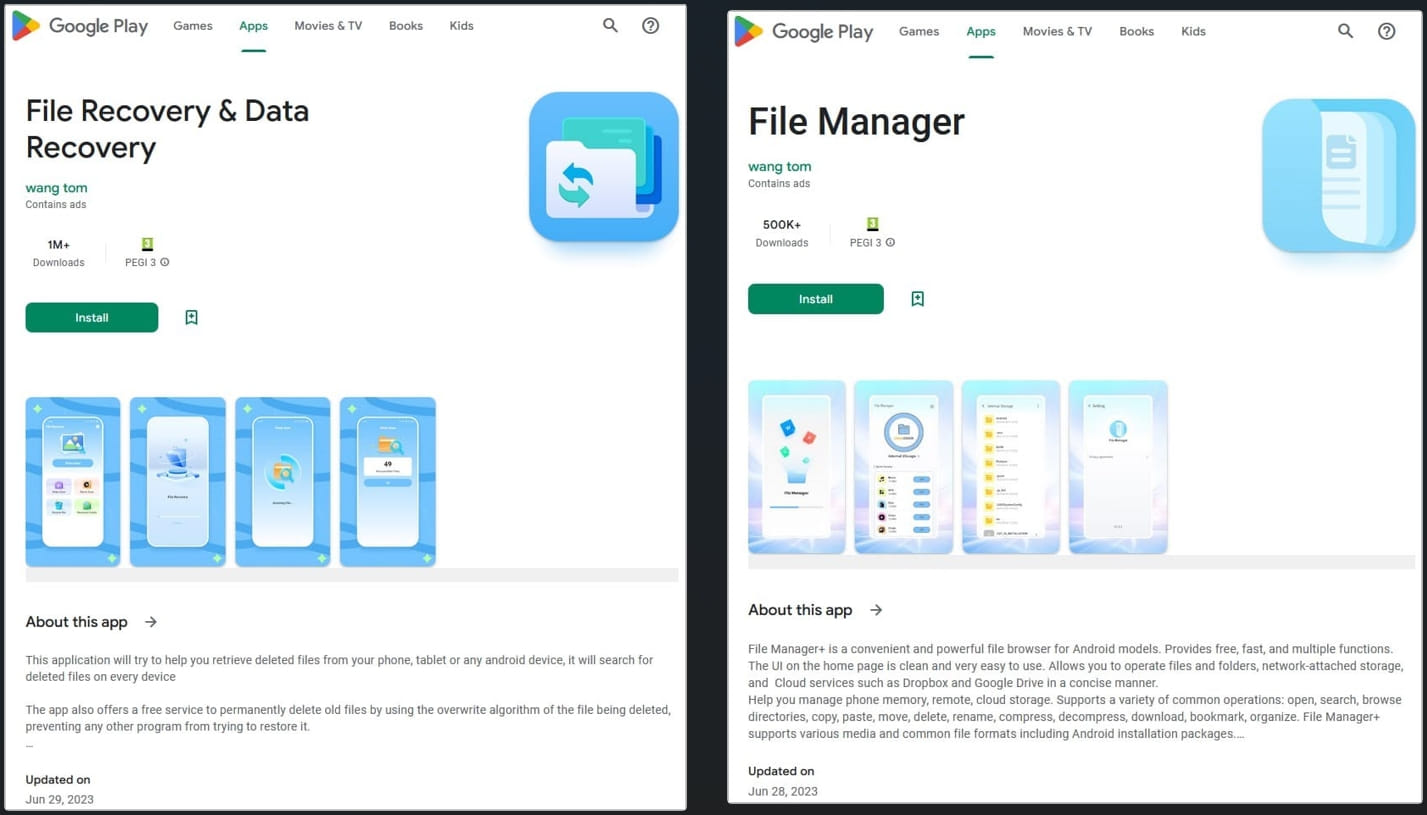
File Recovery and Data Recovery, identified as "com.spot.music.filedate" on devices, has at least 1 million installs. The install count for File Manager reads at least 500,000 and it can be identified on devices as "com.file.box.master.gkd."
The two apps were discovered by the behavioral analysis engine from mobile security solutions company Pradeo and their description states that they do not collect any user data from the device on the Data Safety section of their Google Play entry
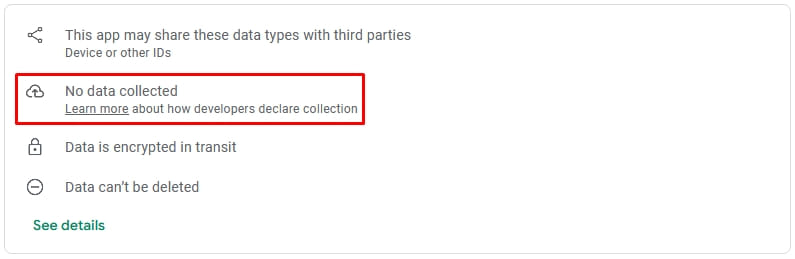
However, Pradeo found that the mobile apps exfiltrate the following data from the device:
- Users' contact list from on-device memory, connected email accounts, and social networks.
- Pictures, audio, and video that are managed or recovered from within the applications.
- Real-time user location
- Mobile country code
- Network provider name
- Network code of the SIM provider
- Operating system version number
- Device brand and model
While the apps might have a legitimate reason to collect some of the above to ensure good performance and compatibility, much of the collected data is not necessary for file management or data recovery functions. To make matters worse, this data is collected secretly and without gaining the user's consent.
Pradeo adds that the two apps hide their home screen icons to make it more difficult to find and remove them. They can also abuse the permissions the user approves during installation to restart the device and launch in the background.
It is likely that the publisher used emulators or install farms to bloat popularity and make their products appear more trustworthy, Pradeo speculates.
This theory is supported by the fact that the number of user reviews on the Play store is way too small compared to the reported userbase.
It is always recommended to check user reviews before installing an app, pay attention to the requested permissions during app installation, and only trust software published by reputable developers.
Update 7/6/23 5:51 PM ET: Google shared the following statement with BleepingComputer and said that they removed the apps from Google Play.
"These apps have been removed from Google Play. Google Play Protect protects users from apps known to contain this malware on Android devices with Google Play Services, even when those apps come from other sources outside of Play."



Comments
Hmm888 - 11 months ago
It sounds like these researchers may have missed a lot of apps like Tiktok and WeChat.
NoneRain - 11 months ago
I think they send data to servers on US and Europe. Also, they describe they collect data.
Not saying they don't send users' data to China, neither that they collect only what they say... but at least, they're working legally under PlayStore and gov rules.
NoneRain - 11 months ago
"Google Play Protect protects users from apps known to contain this malware on Android devices with Google Play Services"
Play Protect is as useless as it can be... just like their statement.
shade - 11 months ago
...and all the rest of our data gets sent to America so who gives af? Why do all these sensationalized stories keep trying to make China out to be the bad guys. It's just thinly vailed racism masquerading as a security threat.
EndangeredPootisBird - 11 months ago
Or maybe it's due to the fact that China is a dictatorship where the government has complete control over all businesses?
shade - 11 months ago
As opposed to America who weaponized the economy and tries to control not just their own country but the entire world.
shade - 11 months ago
...oh yeah not to mention social media, pretty sure they were the 1st to weaponize that and every other media industry like for ever. ie. news, movies, video games and basically any thing you can think of throughout the history of pop-culture is full of American propaganda.
AutomaticJack - 11 months ago
"...and all the rest of our data gets sent to America so who gives af? Why do all these sensationalized stories keep trying to make China out to be the bad guys. It's just thinly vailed racism masquerading as a security threat. "
I was thinking the same but after doing some digging it turns out that if there is a large enough populous being data mined then that counts as a greater risk of mass manipulation/social engineering to say sway elections vs the odd password or crypto wallet. Same idea with tiktok. When such a gov has data+/control of millions of western users -our side don't want to take a risk with what they might be able to do with it now, or in the future.
shade - 11 months ago
The fact you used the term "our side" made me giggle. What use is swaying an election in an already corrupt two party system? You would actually need ties to Washington to make any meaningful difference and as we've seen, presidents can't even back their own election promises let alone some kind of backdoor deal with a perceived threat actor.
shade - 11 months ago
I think this shared paranoia (that keeps getting amplified by these types of headlines) that all Americans seem to suffer from on some level, is a side effect of the lifelong consumption of Uncle Sams propaganda machine.
AutomaticJack - 11 months ago
"The fact you used the term "our side" made me giggle. What use is swaying an election in an already corrupt two party system? You would actually need ties to Washington to make any meaningful difference and as we've seen, presidents can't even back their own election promises let alone some kind of backdoor deal with a perceived threat actor."
Just a figure of speech. I agree - no good system exists at this time on our planet. But it's well known the prc continue to work on such operations for their gain - and as per in any war the other side is going to counteract. We do it, they do it, nothing new.
Kbohent - 11 months ago
Social credits +1000000