-
SLocker Android Ransomware Makes Furious Comeback with 400 New Variations
The SLocker Android ransomware is back with a new wave of infections, after previously wreaking havoc in the summer of 2016.
- May 11, 2017
- 01:40 PM
 0
0
-
Hackers Use Flaws in Telephony Core Protocol to Bypass 2FA on Bank Accounts
Hackers have exploited decades-old flaws in the SS7 mobile telephony protocol to hijack phone numbers and SMS messages, in order to bypass two-factor authentication (2FA) and steal money from bank accounts.
- May 05, 2017
- 01:36 AM
 0
0
-
Open Ports Create Backdoors in Millions of Smartphones
Mobile applications that open ports on Android smartphones are opening those phones to remote hacking, claims a team of researchers from the University of Michigan.
- April 28, 2017
- 02:25 PM
 0
0
-
Over Two Million Users Infected With New Android Adware
A new form of Android malware is wreaking havoc on Google Play. The malware, called FalseGuide was found in several Android apps that have been installed by over two million users.
- April 26, 2017
- 04:41 AM
 0
0
-
Android O Will Contain Special Feature to Fight Off Ransomware
Google has removed a feature of the Android operating system that has been used in the past in ransomware attacks.
- April 22, 2017
- 04:15 AM
 0
0
-
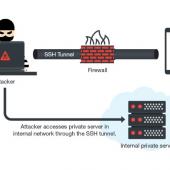
MilkyDoor Android Malware Uses SSH Tunnels to Access Secure Corporate Networks
A new form of Android malware, named Milkydoor, uses remote port forwarding via Secure Shell (SSH) tunnels to hide malicious traffic and grant attackers access to firewall-protected networks.
- April 21, 2017
- 10:11 AM
 0
0
-
Spyware Disguised as System Update Survived on Play Store for Almost Three Years
An Android app named "System Update" that secretly contained a spyware family named SMSVova, survived on the official Google Play Store for at least three years, since 2014, when it was updated the last time.
- April 20, 2017
- 06:32 AM
 0
0
-
Malware Reaches Play Store as Google Wages War Against BankBot Trojan
The BankBot Android banking trojan is giving Google engineers headaches, as this particular piece of malware has a knack for avoiding Google's security scans and reaching the official Play Store on a regular basis.
- April 17, 2017
- 07:20 PM
 0
0
-
Attackers Can Decipher PINs and Passwords From the Way Users Tilt Their Phone
A JavaScript file secretly loaded without your knowledge on a site, or app you load on your mobile device, can access data from various sensors and collect information needed to guess the passwords or PIN a user is entering on his device.
- April 11, 2017
- 10:26 AM
 0
0
-
Scientists Create New Material That May Lead to Self-Healing Electronics
Scientists have developed a new type of material that could be used in the future to create self-healing electronics, such as smartphones, batteries, speakers, robotics, and others.
- April 09, 2017
- 03:00 AM
 0
0
-
Google and Apple Issue Security Updates for Critical Broadcom WiFi Vulnerabilities
Owners of Android and iOS devices should pay special attention to security updates released by Google and Apple on Monday, as they contain fixes for a series of critical bugs affecting their phone's WiFi component.
- April 04, 2017
- 05:08 PM
 0
0
-
You Can Bypass Facial Recognition on New Samsung Galaxy S8 Phones Using a Photo
Even before its official launch, smartphone experts are criticizing Samsung Galaxy S8 phones after one of their colleagues managed to bypass the facial recognition feature that ships with these phones by flashing a photo of himself in front of the phone.
- March 31, 2017
- 08:55 AM
 0
0
-
Google: Ransomware on Android Is Exceedingly Rare
Android apps spreading ransomware aren't as common as most users and security experts think, says Jason Woloz, Sr. Program Manager for Android Security at Google.
- March 30, 2017
- 11:44 AM
 3
3
-
Nearly One Million Android Users Installed 87 Malicious Minecraft Mods
News of malicious Android apps hosted on the Google Play Store doesn't seem to stop coming these days, as ESET and Zscaler researchers recently disclosed they've reported nearly 100 malicious apps they recently come across.
- March 24, 2017
- 05:20 AM
 0
0
-
The Next Big Thing for Android Malware Is "Plugin Frameworks"
Android malware is evolving, and a clear trend has become visible in the past six months, with several malware strains implementing their malicious behavior via plugin frameworks.
- March 22, 2017
- 06:45 PM
 2
2
-
Chinese Crooks Use Fake Cellular Telephony Towers to Spread Android Malware
Malware authors in China are using fake base transceiver stations (BTSs), which is equipment usually installed on cellular telephone towers, to send spoofed SMS messages that contain links to Android malware.
- March 21, 2017
- 06:00 PM
 0
0
-
Researchers Find Vulnerability in WhatsApp and Telegram's Web Clients
WhatsApp and Telegram have patched their respective web clients against a common security flaw discovered by researchers from Israeli firm Check Point, a security issue that would have allowed an attacker to take over user accounts and spy on conversations or steal user account data.
- March 15, 2017
- 04:15 PM
 0
0
-
Google Kicks Chamois Android Adware off the Play Store
Following an internal audit, Google engineers say they'd discovered a new massive ad-fraud botnet that was infecting users via Android apps hosted on the official Play Store.
- March 14, 2017
- 12:00 AM
 0
0
-
13 Google Play Store Apps Caught Stealing Instagram Credentials
Instagram users are once again the targets of malicious Android apps hosted on the Play Store, apps which steal their credentials on false claims of boosting their account's follower numbers.
- March 13, 2017
- 10:23 AM
 0
0
-
Android Adware and Ransomware Found Preinstalled on High-End Smartphones
Two companies have discovered that someone had covertly installed malware on 38 devices used by their employees. According to security firm Check Point, the installation of the malicious apps took place somewhere along the supply chain, after phones left the manufacturer's factory and before they arrived at the two companies.
- March 10, 2017
- 06:21 PM
 0
0