
Hackers are targeting websites using the PrestaShop platform, leveraging a previously unknown vulnerability chain to perform code execution and potentially steal customers' payment information.
The PrestaShop team issued an urgent warning last Friday, urging the admins of 300,000 shops using its software to review their security stance after cyberattacks were discovered targeting the platform.
The attack appears to impact PrestaShop versions 1.6.0.10 or later and versions 1.7.8.2 or later if they run modules vulnerable to SQL injection, such as the Wishlist 2.0.0 to 2.1.0 module.
The actively exploited vulnerability is being tracked with the identifier CVE-2022-36408.
Attack details
The attack begins by targeting a module or an older platform version vulnerable to SQL injection exploits. PrestaShop's team has not determined where these flaws exist at this time and warned that the compromise might be caused by a third-party component too.
"We believe attackers are targeting shops using outdated software or modules, vulnerable third-party modules, or a yet-to-be-discovered vulnerability," explains the PrestaShop security advisory.
To conduct the attack, hackers send a POST request to a vulnerable endpoint followed by a parameter-less GET request to the homepage that creates a "blm.php" file at the root directory.
The blm.php file appears to be a web shell that allows the threat actors to execute commands on the server remotely.
In many observed cases, the attackers used this web shell to inject a fake payment form on the shop's checkout page and steal customers' payment card details.
After the attack, the remote threat actors wiped their tracks to prevent the site owner from realizing they were breached.
Security update released
If the attackers weren't diligent with the cleanup of evidence, compromised site administrators might find entries in the web server's access logs for signs that they were compromised.
Other signs of compromise include file modifications to append malicious code and the activation of the MySQL Smarty cache storage, which serves as part of the attack chain.
This feature is disabled by default, but PrestaShop has seen evidence of the hackers enabling it independently, so the recommendation is to remove it if not needed.
To do that, locate the file "config/smarty.config.inc.php" on your shop and delete the following lines:
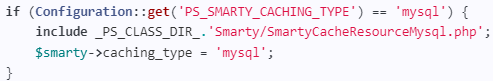
Finally, upgrade all used modules to the latest available version and apply the PrestaShop security update released today, version 1.7.8.7.
This security fix strengthens the MySQL Smarty cache storage against all code injection attacks, for those who want to continue using the legacy feature.
However, it is important to note that if your site has already been compromised, applying the security update won't remediate the problem.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now