
VMware patched today a VMware ESXi zero-day vulnerability exploited by a Chinese-sponsored hacking group to backdoor Windows and Linux virtual machines and steal data.
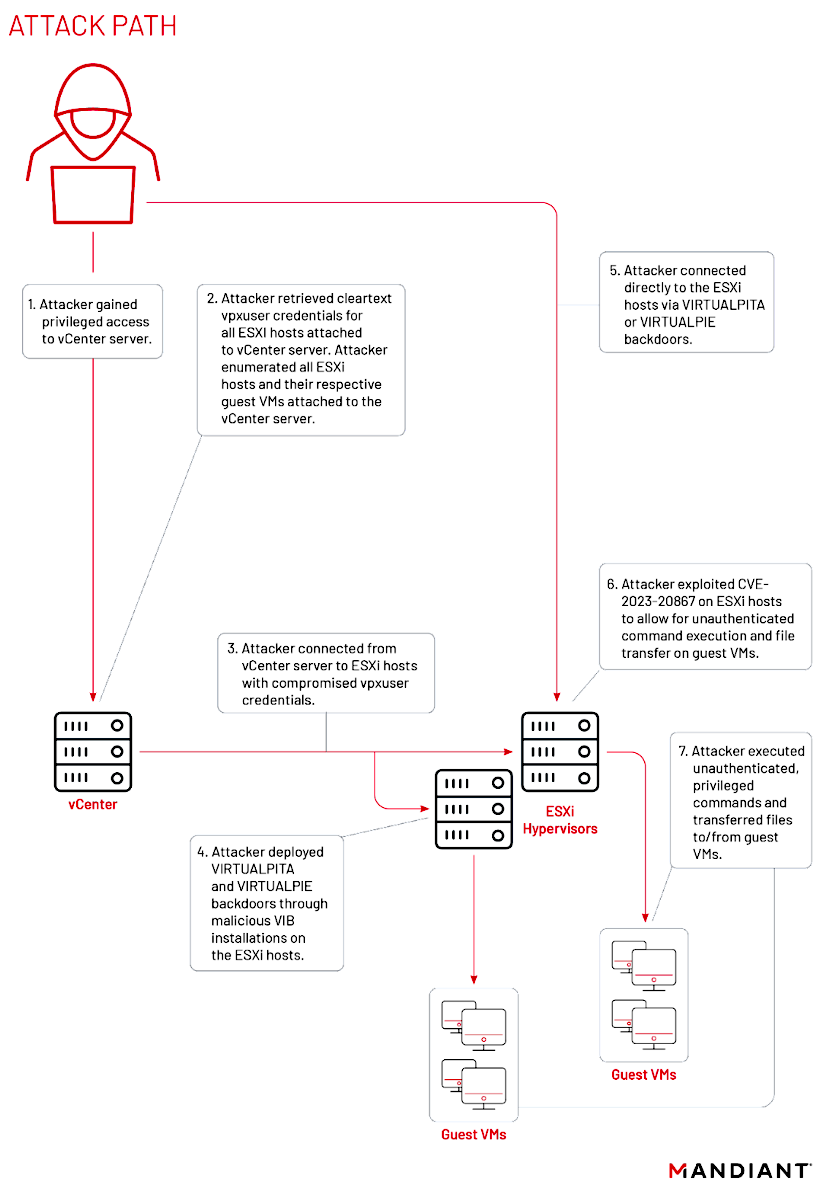
The cyber espionage group—tracked as UNC3886 by cybersecurity firm Mandiant who discovered the attacks—abused the CVE-2023-20867 VMware Tools authentication bypass flaw to deploy VirtualPita and VirtualPie backdoors on guest VMs from compromised ESXi hosts where they escalated privileges to root.
"A fully compromised ESXi host can force VMware Tools to fail to authenticate host-to-guest operations, impacting the confidentiality and integrity of the guest virtual machine," VMware said in today's security advisory.
The attackers installed the backdoor malware using maliciously crafted vSphere Installation Bundles (VIBs), packages designed to help admins create and maintain ESXi images.
A third malware strain (VirtualGate) that Mandiant spotted during the investigation acted as a memory-only dropper that deobfuscated second-stage DLL payloads on the hijacked VMs.
"This open communication channel between guest and host, where either role can act as client or server, has enabled a new means of persistence to regain access on a backdoored ESXi host as long as a backdoor is deployed and the attacker gains initial access to any guest machine," Mandiant said.
"This [..] further reinforces UNC3886's deep understanding and technical knowledge of ESXi, vCenter and VMware's virtualization platform. UNC3886 continues to target devices and platforms that traditionally lack EDR solutions and make use of zero-day exploits on those platforms."
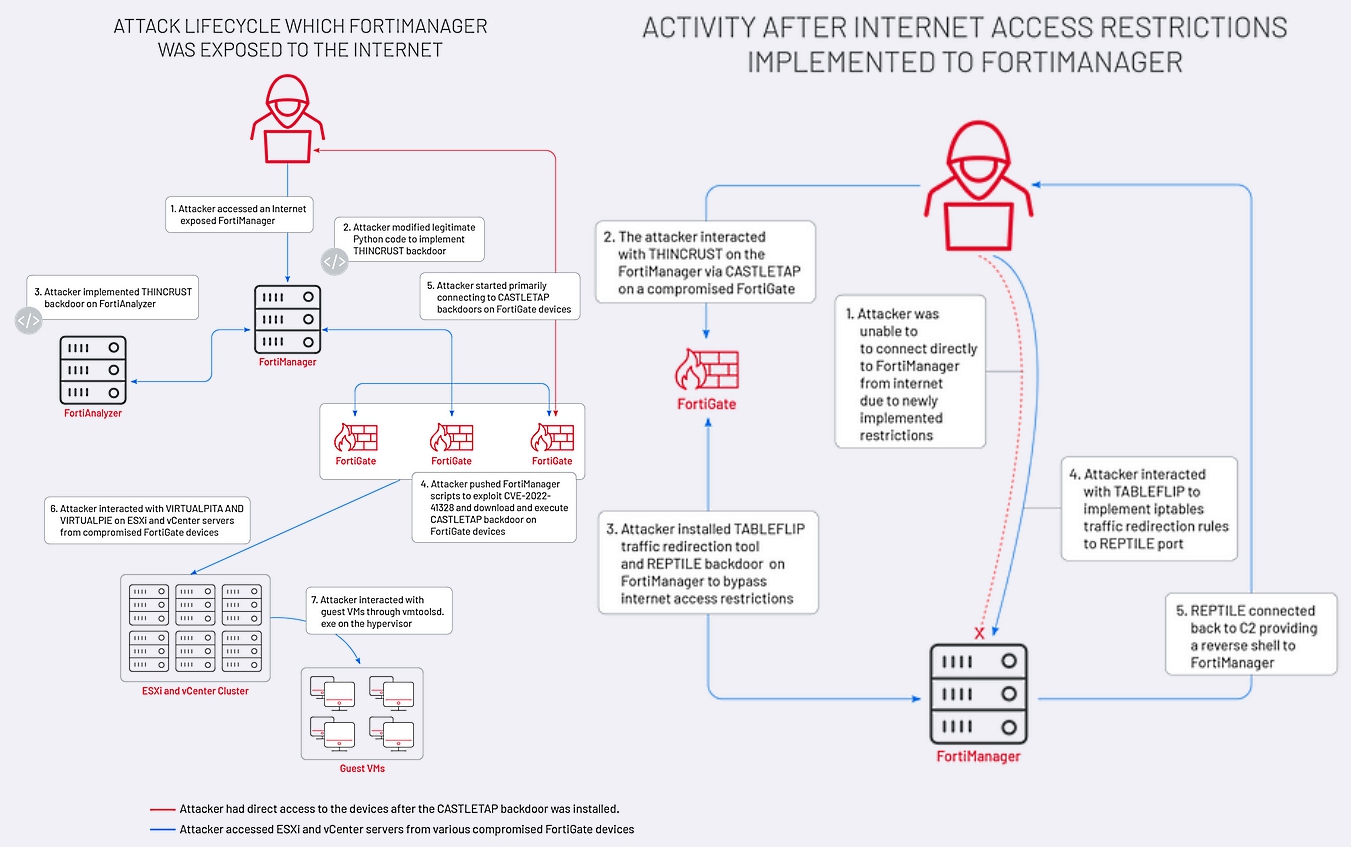
In March, Mandiant also revealed that the Chinese UNC3886 hackers abused a zero-day vulnerability (CVE-2022-41328) in the same mid-2022 campaign to compromise FortiGate firewall devices and deploy previously unknown Castletap and Thincrust backdoors.
They used the access gained after hacking the Fortinet devices and gaining persistence on FortiManager and FortiAnalyzer devices to move laterally through the victims' network.
In the next stage, they backdoored ESXi and vCenter machines using VirtualPita and VirtualPie malware to ensure their malicious activities remained undetected.
"The attack is highly targeted, with some hints of preferred governmental or government-related targets," Fortinet said.
"The exploit requires a deep understanding of FortiOS and the underlying hardware. Custom implants show that the actor has advanced capabilities, including reverse-engineering various parts of FortiOS."
This cyber-espionage group is known for focusing its attacks on organizations in the defense, government, telecom, and technology sectors in the U.S. and APJ regions.
Their favorite targets are zero-day vulnerabilities in firewall and virtualization platforms that don't have Endpoint Detection and Response (EDR) capabilities.
UNC3886's use of a wide range of new malware families and malicious tools tailored explicitly for the platforms they're targeting suggests substantial research capabilities and an out-of-ordinary ability to understand the complex tech employed by the targeted appliances, according to Mandiant.
"This is a continuation of Chinese espionage that has been going on for years. This tradecraft is very clever and hard to detect. We are sure there are other victims that are dealing with this that don’t yet know," Mandiant CTO Charles Carmakal told BleepingComputer.
"They've successfully compromised defense, technology, and telecommunications organizations with mature security programs in place."



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now