For a third time in four months, a security researcher announces a zero-day vulnerability in Microsoft Windows and provides exploit code that allows reading into unauthorized locations.
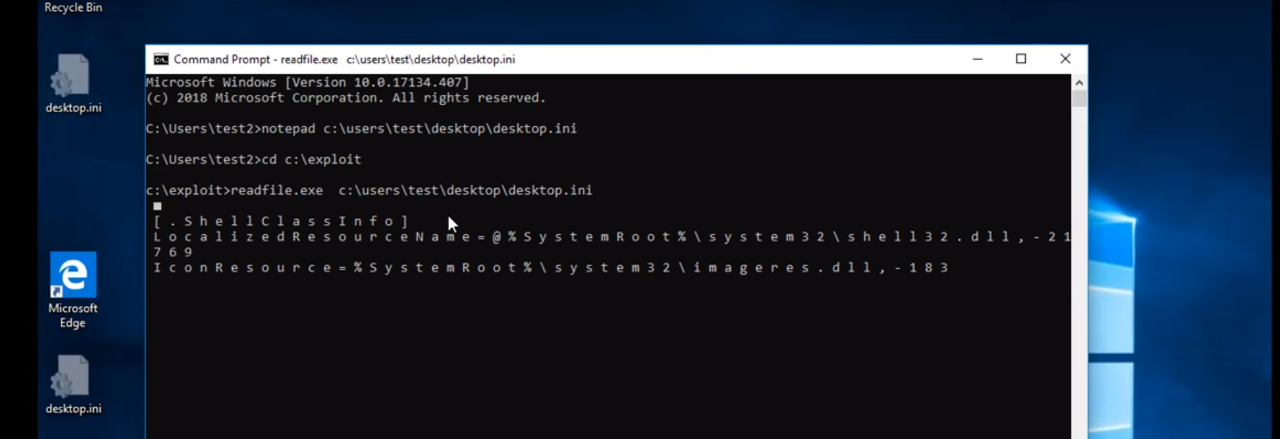
Known by the moniker SandboxEscaper, the researcher released details about a security vulnerability affecting ReadFile.exe, which, as its name indicates, allows reading data from specific locations.
Exploit code works
The glitch is in the "MsiAdvertiseProduct" function, which Microsoft describes as being able to generate an advertise script or advertises a product to the computer" and that it "enables the installer to write to a script the registry and shortcut information used to assign or publish a product."
Calling this function leads to an arbitrary file copy by the installer service, which is controllable by the attacker, the researcher explains.
SandboxEscaper explains that despite a check being done, the protection can be bypassed via a time to check to time to use (TOCTOU) race condition type.
The end result, she says, is the possibility to copy any files with SYSTEM privileges, with the destination being readable at all times. Because of this, she calls it an arbitrary file read vulnerability.
SandboxEscaper also makes available a video to demonstrate her findings:
The researcher says that the "easiest way to confirm the bug is to make two local accounts and read the desktop.ini of the other account."
The validity of the PoC has been confirmed today by Mitja Kolsek, CEO of Acros Security and founder of the 0Patch platform that pushes temporary fixes (micropatches) to its clients until vulnerabilities are fully addressed.
We have confirmed this POC to work and in fact provide read access to a chosen file that the initiating user didn't have read access to. https://t.co/GSP1YLo43U
— 0patch (@0patch) December 20, 2018
Kolsek told BleepingComputer that they hope to get a micropatch out before the holidays.
Third 0day and FBI is interested in the researcher
This is the third zero-day in Windows that SandboxEscaper releases publicly, without giving Microsoft a heads-up.
The first one was published at the end of August and allowed privilege escalation via Windows Task Scheduler
The second one was published towards the end of October and it was also a privilege escalation vulnerability. It allowed deleting without permission any files on the system.
Since publishing the first 0day in Windows, SandboxEscaper lost access to her GitHub account, where she posted bug details and proof-of-concept code. In a message on her blog, the researcher blames Microsoft directly for this.
She also managed to get the attention of the FBI, as she received a notification from Google about the agency issuing a subpoena for information release about her Google account.
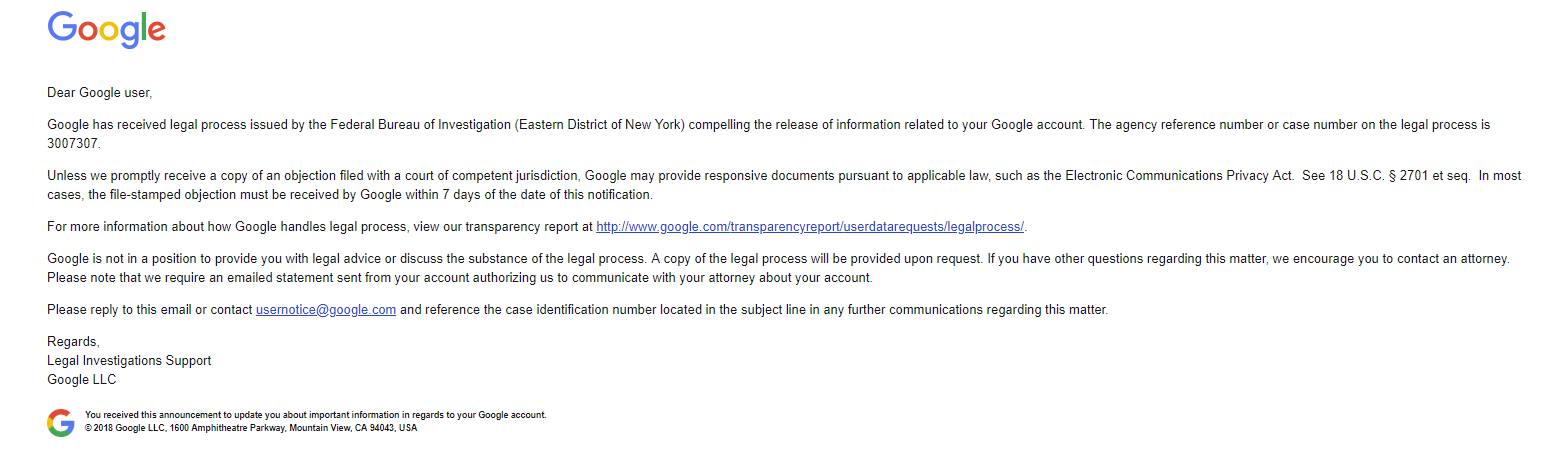
The reason before FBI's move is currently unknown, but it may not be in relation to SandboxEscaper dumping Windows zero-days and exploit code into the public space. It could have something to do with a short-lived tweet from her allegedly containing a threat against the US President.



Comments
JohnnyJammer - 5 years ago
Mate i have really grave concerns and feel for this person who is going through a real life struggle. They need to speak with someone soon because reading the blog is basically what i see as a letter before they die.
Please Polarbear, speak openly and be safe and who cares what people say about your transition because its none of their business.
andySF - 5 years ago
This person needs help.