It is unsure how CryptoTorLocker 2015 is installed on a system, but once installed it will scan your computer and infect any data files and shortcuts that it finds. As it encrypts each file, it will append .CryptoTorLocker2015! to the end of each filename. So a file called invoice.doc would become invoice.doc.CryptoTorLocker2015!. It will also create a ransom note called HOW TO DECRYPT FILES.txt in each directory it encounters. The text of the ransom note is below. Please note that this ransom note was actually written this way.
Your important files strong encryption RSA-2048 produces on this computer:Photos,Videos,documents,usb disks etc.Here is a complete list of encrypted files,and you can personally verify this.CryptoTorLocker2015! which is allow to decrypt and return control to all your encrypted files.To get the key to decrypt files you have to pay 0.5 Bitcoin 100$ USD/EUR. Just after payment specify the Bitcoin Address.Our robot will check the Bitcoin ID and when the transaction will be completed, you'll receive activation,Purchasing Bitcoins,Here our Recommendations 1. Localbitcoins.com This is fantastic service,Coinbase.com Exchange,CoinJar =Based in Australia,We Wait In Our Wallet Your Transaction WE GIVE YOU DETAILS! Contact ME if you need help My Email = information@jupimail.com AFTER YOU MAKE PAYMENT BITCOIN YOUR COMPUTER AUTOMATIC DECRYPT PROCEDURE START! YOU MUST PAY Send 0.5 BTC To Bitcoin Address: 1KpP1YGGxPHKTLgET82JBngcsBuifp3noWWhen it has finished encrypting your data it will then change your wallpaper to a patchwork of images copied from other ransomware infections. If anything, it may be worth paying the ransom so you do not have to look at this wallpaper anymore.

Finally, the infection will display another alert about your files being encrypted and then displays a password prompt. Supposedly if you paid the ransom, the developer would send you a password, which you would enter to decrypt your files.
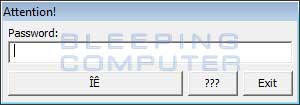
The fact that there was no discernable network traffic when it was installed indicated that the decryption key was built into the executable itself or stored somewhere on the computer. Also a password prompt hinted that it may be possible to patch the executable to make it think that any password entered was the correct one in order to begin the decryption process. When security researcher Nathan Scott looked at the executable, he confirmed that you could simply bypass the password to begin decrypting, but even better it was using XOR encryption. Once this was discovered he was able to quickly find the XOR key and whip up a decrypter for anyone who was affected.
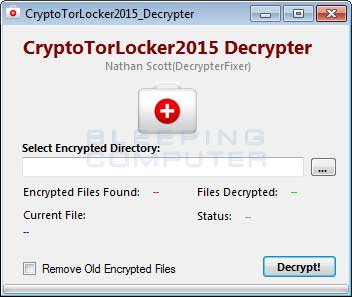
With that said, for those who are infected with CryptoTorLocker2015, you can easily decrypt your files by downloading and running Nathan Scott's decrypter. It should be noted that some anti-virus programs are detecting this infection based on its CryptoTorLocker2015 name and as that same string is used in the decrypter, some AV programs may detect it as malicious. This is a false positive, but if you are concerned about the safety of the decryption tool, you can always copy your encrypted data to a virtual machine and run the decrypter from there.
The decrypter can be downloaded from this link: http://ransomwareanalysis.com/CT2015_Decrypter.zip
Once you start the decrypter, select a folder to scan and any encrypted files will be decrypted. When using the tool, it is suggested that you select the root of the drive such as C:\ and let the decrypter recursively scan your entire drive. If you are finding that some files, most likely shortcuts, are not properly being decrypted, you should run the program with Administrator privileges.
As always, if you have any questions, please feel free to post them here.
Known CryptoTorLocker2015 Ransomware Files:
%Temp%\HOW TO DECRYPT FILES.txt %Temp%\<random>.bmp %Temp%\<random>.exeKnown CryptoTorLocker2015 Ransomware Registry keys:
HKLM\SOFTWARE\Classes\.CryptoTorLocker2015! HKLM\SOFTWARE\Classes\.CryptoTorLocker2015!\@ = "PRPASCBHJSZLMOM" HKLM\SOFTWARE\Classes\PRPASCBHJSZLMOM\@ = "CRYPTED!" HKLM\SOFTWARE\Classes\PRPASCBHJSZLMOM\DefaultIcon\@ = "%Temp%\<random>.exe,0" HKLM\SOFTWARE\Classes\PRPASCBHJSZLMOM\shell\open\command\@ = "%Temp%\<random>.exe" HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\Alcmeter = "%Temp%\<random>.exe" HKCU\Control Panel\Desktop\Wallpaper = "%Temp%\<random>.bmp"Host File Modifications:
93.189.44.187 dmidybmfxsaq.biz 93.189.44.187 aacthvhqbhbg.org 93.189.44.187 arlsolqovltp.co.uk 93.189.44.187 fyhatdpptohp.org 93.189.44.187 weotnaktbwgr.ru 93.189.44.187 ovenbdjnihhdlb.net




 Back to top
Back to top













