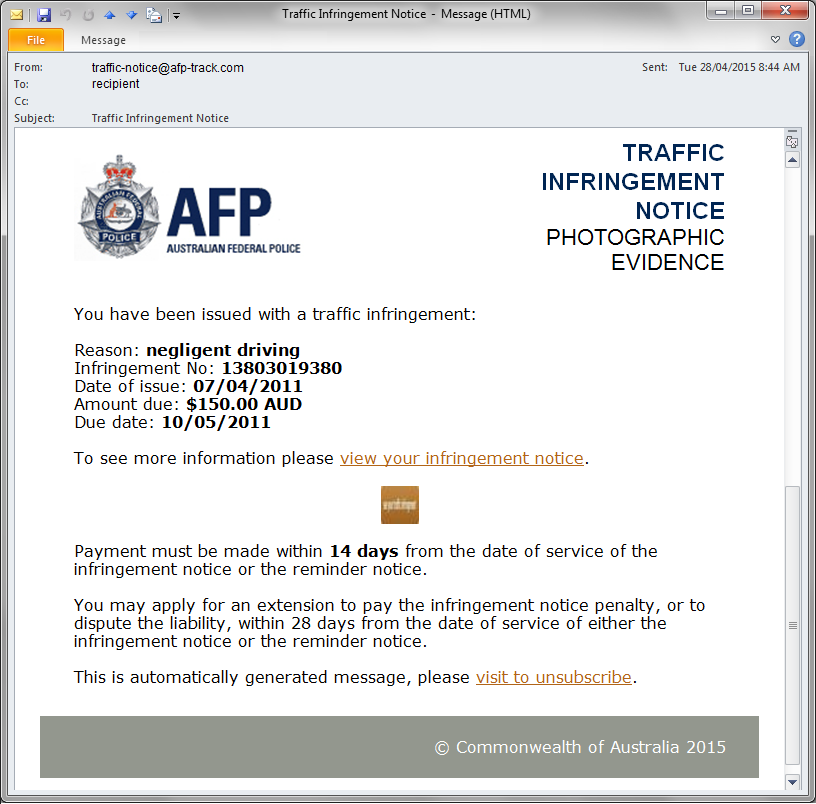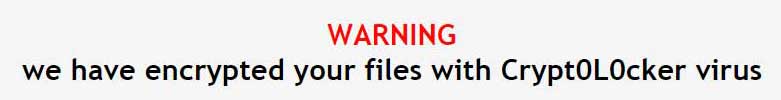
A new ransomware called Crypt0L0cker (the OHs have been replaced with ZEROs) has been released that appears to be a new version of TorrentLocker. This ransomware was first sighted at the end of April in European and Asian countries and in Australia. Unlike TorrentLocker, for some reason this variant is Geo-Locked so that it will not install on US based computers. This ransomware is currently being distributed through emails that pretend to be traffic violations or other government notices. At this point it is unknown what encryption method is used and if its possible to recover encrypted files. The ransom amount is currently set for 2.2 Bitcoins.
At a brief glance, Crypt0L0cker uses the same communication methods as TorrentLocker. When first installed, Crypt0L0cker will connect to a Command & Control server and send the victim's unique identifier as well as the campaign ID. The Command & Control server will then send back the HTML ransom note and the name of the file it should be saved as. Currently the HTML ransom note is DECRYPT_INSTRUCTIONS.html and text version is DECRYPT_INSTRUCTIONS.txt. An example of the ransom note can be found below:
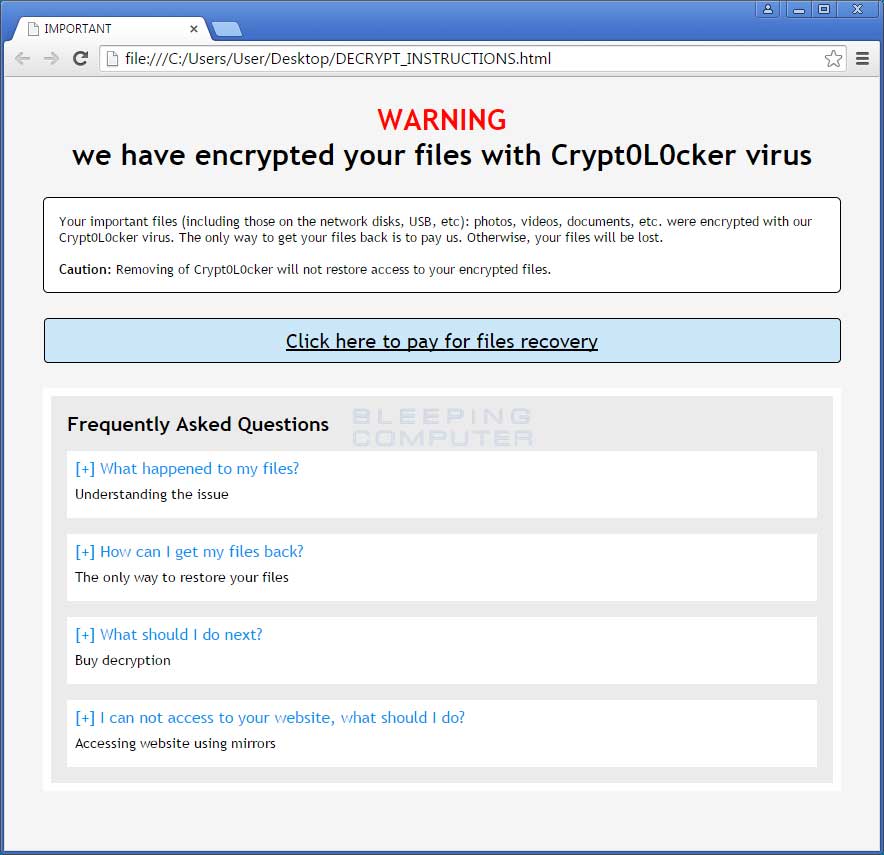
DECRYPT_INSTRUCTIONS.html
Crypt0L0cker will then begin to scan all hard drive letters and encrypt any files that do not match an exclude list. When a file is encrypted it will append the .encrypted extension to the file name. Unlike TorrentLocker, which had a hard coded extension list that it targeted, Crypt0L0cker has a hard coded list of extensions that it does not target. This allows it to encrypt any file type other than the select few that it deems would cause a problem with Windows. The lists of excluded file types are:
avi,wav,mp3,gif,ico,png,bmp,txt,html,inf,manifest,chm,ini,tmp,log,url,lnk,cmd,bat,scr,msi,sys,dll,exeDuring this process, Crypt0L0cker will also delete all of your Shadow Volume Copies so that you are unable to recover your files from them.
When the encryption process is done, it will display the ransom notes, which were created in every folder on your computer. It will also configure Crypt0L0cker to start every time you login into Windows by adding a system.pif to your Startup folder and an autorun to the Windows Registry. These startups allow the malware to display the ransom note every time you login to Windows.
Like TorrentLocker, the ransom notes contain personal links to the Buy Decryption site where you can get instructions on how to make a payment. These links contain your personal ID and password so that you only have access to your own information. It is on this site that you will be told how many bitcoins you must pay, how long you have to pay it, and what bitcoin address you must send the payment to. Like TorrentLocker, the Crypt0L0cker's Buy Decryption site is broken up into Buy Decryption, Free Decrypt Single File, Frequently Asked Questions, and Support pages. This is essentially the exact same site as the TorrentLocker one.
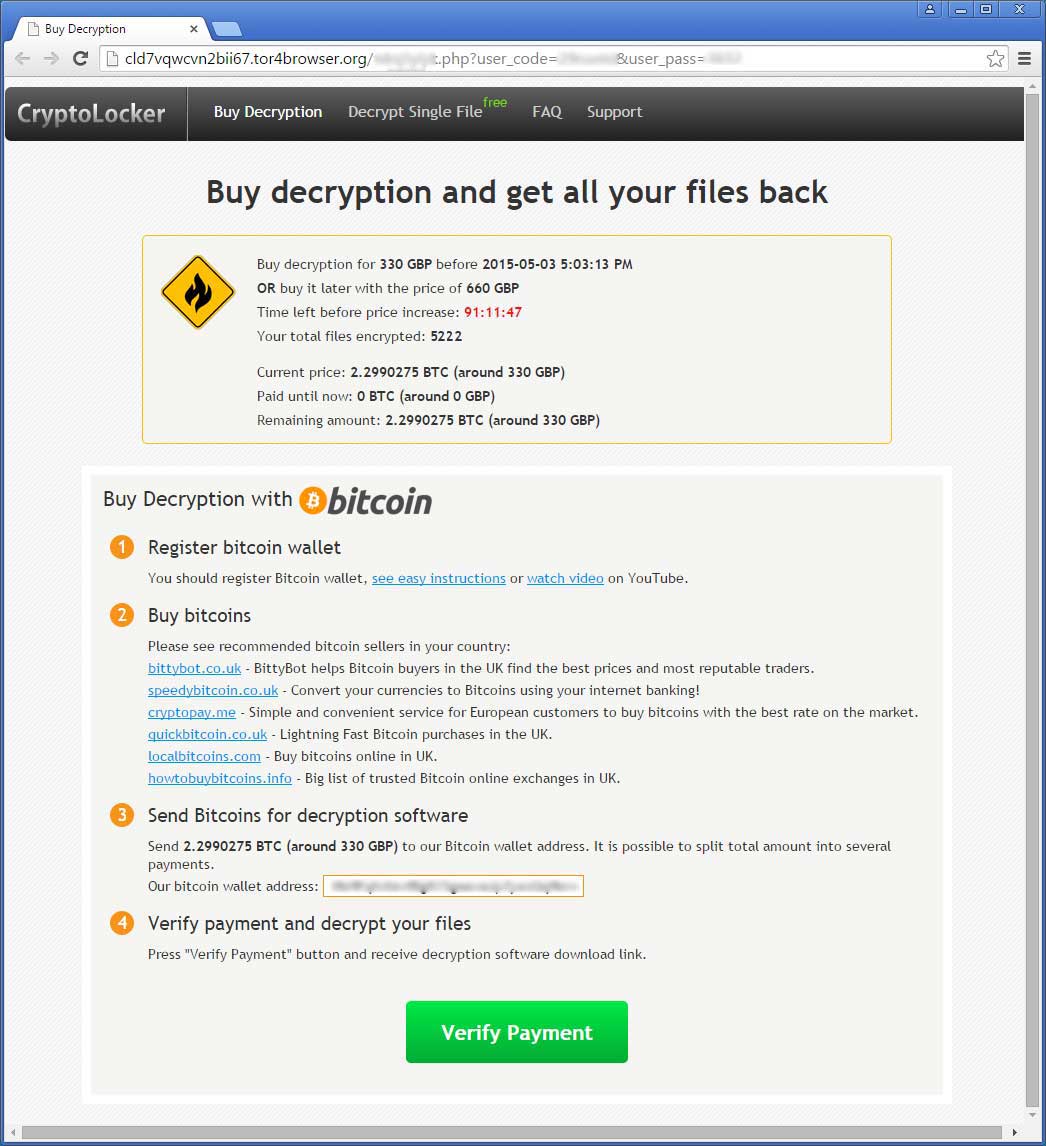
Crypt0L0cker's Decryption Site
At this time there is no known way to decrypt your files for free. It is suggested that you restore your files from backup, and if that is not an option, attempt to use recovery software to recover your files. For those who want to discuss this infection, a dedicated Crypt0L0cker Support Topic has been created.
As new information is released, we will be sure to update this story.
Known Crypt0L0cker Scareware Files:
C:\ProgramData\iwymyzucasakodon\ C:\ProgramData\iwymyzucasakodon\00000000 C:\ProgramData\iwymyzucasakodon\01000000 C:\ProgramData\iwymyzucasakodon\02000000 C:\ProgramData\iwymyzucasakodon\03000000 C:\ProgramData\iwymyzucasakodon\04000000 C:\ProgramData\iwymyzucasakodon\05000000 C:\ProgramData\iwymyzucasakodon\06000000 %StartMenu%\Programs\Startup\system.pif %WinDir%\<random>.exeKnown Crypt0L0cker Scareware Registry keys:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\<random> "C:\Windows\<random>.exe"




 Back to top
Back to top