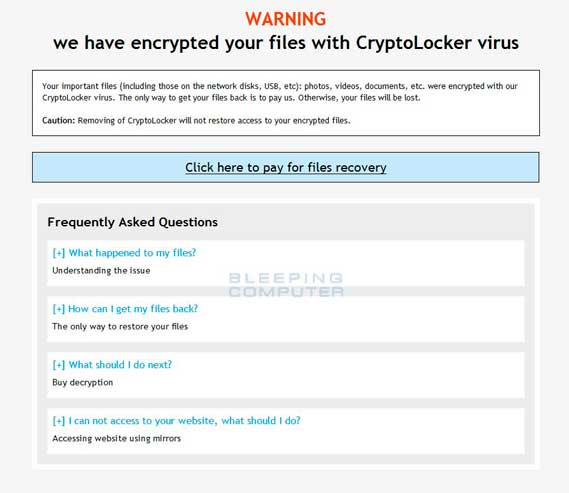
Previous Analysis of the ransomware shows that each victim has its own unique AES decryption key that is used to decrypt their files. That would mean that the only way to decrypt encrypted files would be to have access to the decryption keys from TorrentLockers Command & Control server. Due to this, it came as a surprise when in May 2015, a member named Wallak posted that paying customers of Dr.Web products were able to get their files decrypted for free.
Ok guys, seems that Dr.Web Russian antivirus has a solution. Some of my web visitors have confirmed that buying some product (antivirus, internet security suite, etc...) customers have a FREE tool to decrypt the files (a DOC file must be sent to the experts to get back the KEY with their tool to decrypt).
It works, I checked it, and also the KEY the send put inside (patching) the decrypters from the pirates, also work, so it is the real KEY.
Wallak further stated that he heard about this from Dr.Web partners in Spain.
As this seemed suspicious that a well-known company would have the ability to help victims and was not making it public, we were suspicious of this post. I therefore decided to reach out to Dr. Web and try to get confirmation. I emailed them and explained how we are trying to get information about whether they could actually decrypt TorrentLocker files before we referred visitors to them. To my surprise, I received a response back from Boris Sharov, the CEO of Dr.Web, who said they do not classify ransomware by their name, but rather by their own designation. He said I could send some files in and someone would get back to me whether or not they could decrypt it. I sent some files, waited 10 days, emailed them again about it, and never heard back.
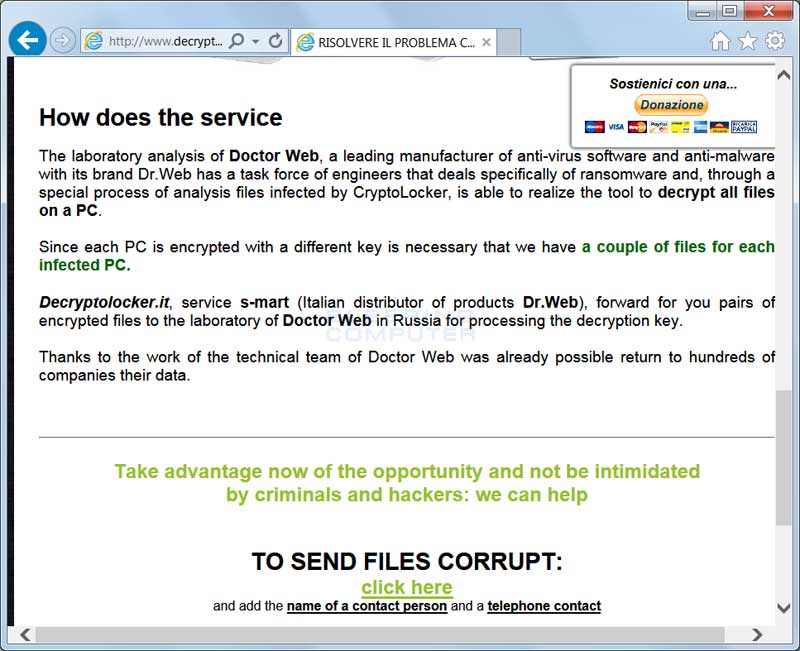
Today, someone else posted on BleepingComputer.com about an Italian site called www.decryptolocker.it that states that it can help get the decryption program for victims affected by TorrentLocker and CryptoL0cker. It further explains that they are a distributor of Dr.Web and are able to work with them to get a decryption program made if you send a couple of encrypted files in. This site does not require you to purchase a Dr.Web license.
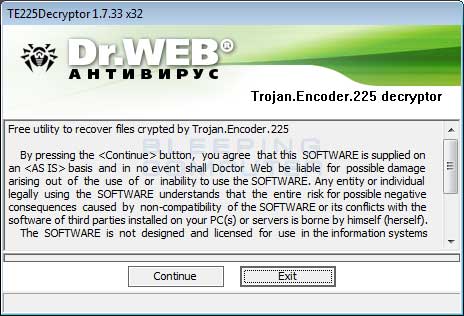
A sample of one of these Dr.Web decryption programs called te225decrypt is shown below.
Overall, this whole revelation has been welcome, surprising, confusing, and suspicious all rolled into one. The fact that they never responded to queries from myself and others, never publicly announced that they were able to decrypt this ransomware, and we have only heard about it through distributors just feels odd.
Regardless, this is still welcome news for those affected by the TorrentLocker ransomware and we hope that you will be able to use Dr.Web to recover your files. As for Dr.Web, we would still love to see some official reply from them regarding this.




 Back to top
Back to top