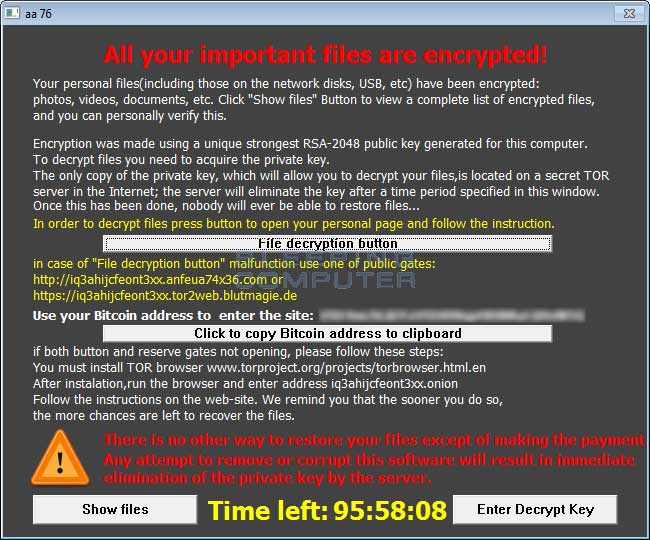
New TeslaCrypt version
TeslaCrypt versions do not include the name of the ransomware in the application itself. It is only till you go to the decryption site that you will see the namw of the particular version. With this new version the ransomware no longer has an identifying name associated with it. My guess for not naming this new version is to make it harder for people to search for help topics, like on our forums for example, to receive help. You can see the header of the decryption service site where the name usually appears below.
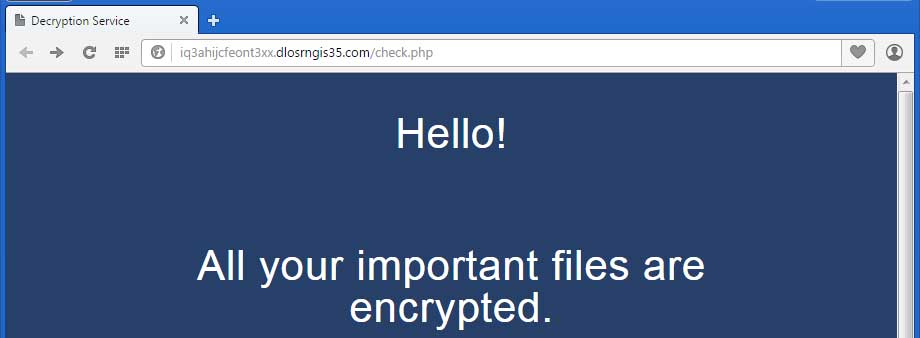
Decryption Service site header with lack of distinguishing name.
Just like Alpha Crypt, it will search out files with the following extensions, encrypt them, but now uses the .EXX extension.
.sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .odtWhen it is done it will change your wallpaper to the Desktop%\HELP_RESTORE_FILES.bmp ransom note and also display a text note found here %Desktop%\HELP_RESTORE_FILES.txt.
Finally, there are some file name and file location changes with this new version. In the past encryption information was stored in the %AppData%\key.dat file. In this version the information is stored in %LocalAppData%\storage.bin.
At this point there is no way to decrypt your files and TeslaDecrypt will not work with this infection. As more information is discovered, we will be sure to post it here. As always the best way to get the most up-to-date information on the TeslaCrypt family can be found in this guide:
TeslaCrypt and Alpha Crypt Ransomware Information Guide and FAQ
Known new TeslaCrypt Files:
%LocalAppData%\<random>.exe %LocalAppData%\log.html %LocalAppData%\storage.bin %Desktop%\Save_Files.lnk %Desktop%\HELP_RESTORE_FILES.bmp %Desktop%\HELP_RESTORE_FILES.txt %Documents%\RECOVERY_FILE.TXTKnown new TeslaCrypt Ransomware Registry keys:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\AVrSvc %LocalAppData%\<random>.exe HKCU\Control Panel\Desktop\Wallpaper "%Desktop%\HELP_RESTORE_FILES.bmp"




 Back to top
Back to top












