TeslaCrypt and Alpha Crypt Ransomware Information Guide and FAQ
This guide contains all known information about these ransomware.
Over the past couple of days the TeslaCrypt ransomware has changed its name to Alpha Crypt with only a few noticeable differences. Recently we had heard about a new ransomware that was similar to TeslaCrypt but was not able to find an installer. It wasn't until today, thanks to Cody Johnston and http://malware-traffic-analysis.net that we were able to get a sample of this infection. After analyzing it and its associated TOR payment site, we can see that Alpha Crypt is the same as TeslaCrypt.
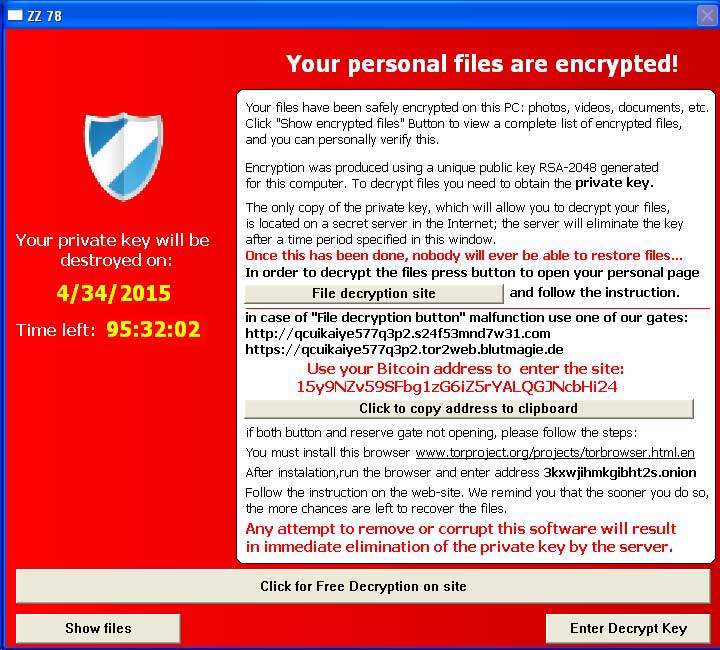
According to Malware-traffic-analysis, Alpha Crypt is being distributed through the Angler Exploit Kit. When installed, Alpha Crypt will scan your computer's drive letters for data files that match certain file extension. When a targeted file is found, it will encrypt it and append the .ezz extension to it. The use of the .ezz extension rather than the .ecc extension is one of the differences between Alpha Crypt and TeslaCrypt. The file types targeted by Alpha Crypt are:
.sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .odtFor the most part, the targeted extensions are the some with some additions and removals. During the encryption process it will create the %AppData%\key.dat file and store information in the key. We are unsure at this time if the information stored in this file can be used to decrypt encrypted files like it could for TeslaCrypt. It will also store a list of all encrypted files in the %AppData%\Log.html file.
When the encryption has finished, it will change your wallpaper to the %Desktop%\HELP_TO_SAVE_FILES.bmp ransom note and then open the %Desktop%\HELP_TO_SAVE_FILES.txt ransom note. Finally it will open the Alpha Crypt application shown above. The Alpha Crypt application and ransom notes contain links and information on how you can pay pay the ransom to decrypt your files.
When you access the decryption site, you will be greeted with a site that is identical to the one used by TeslaCrypt. The only difference is that the name of the ransomware has changed, the title of the site has been changed to AlphaTool Decryption Service, and that PayPal MyCash cards are no longer a payment option. Like TeslaCrypt the Alpha Crypt site offers a free decryption of one file and a support page where you can communicate with the developers. The current ransom cost is .7 bitcoins.
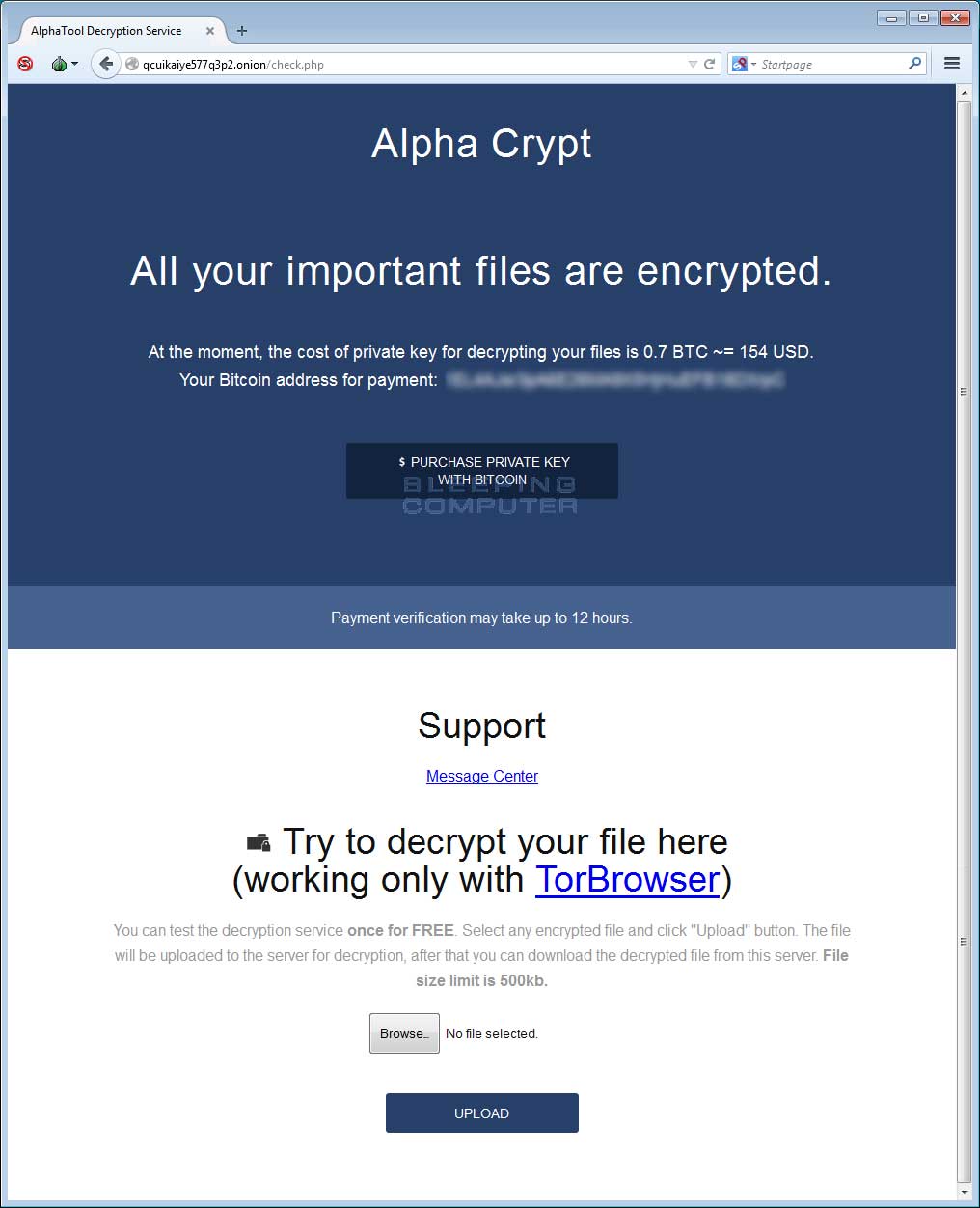
As this is a fairly new variant it is unknown whether the existing decryption techniques for TeslaCrypt will work with Alpha Crypt. As soon we know, we will post the info here.
Known Alpha Crypt Ransomware Files:
%AppData%\<random>.exe %AppData%\log.html %AppData%\key.dat %Desktop%\HELP_TO_SAVE_FILES.txt %Desktop%\HELP_TO_SAVE_FILES.bmp %Desktop%\Save_Files.lnk %Documents%\RECOVERY_FILE.TXTKnown Alpha Crypt Ransomware Registry keys:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\AVSvc %AppData%\<random>.exe




 Back to top
Back to top














