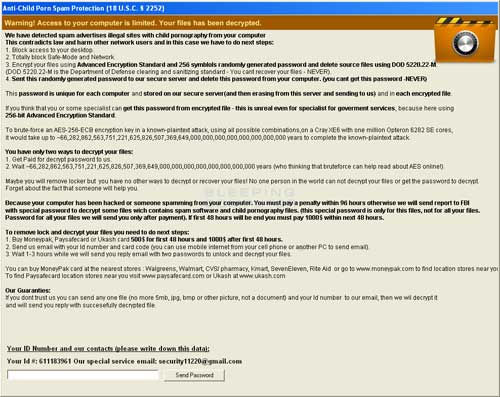
A new variant of the Malware Protection ransomware has been released called Anti-Child Porn Spam Protection. This ransomware pretends to be from a legitimate government organization that states that the infected computer is sending out SPAM that contains links to child pornography sites. The ransom program then states that in order protect yourself, and others, it has encrypted your data using Advanced Encryption Standards, or AES, encryption. Just like the Malware Protection and the ACCDFISA Protection Program variants, these files are not actually encrypted but are password protected RAR files. The hackers then require you to send them a Moneypak, PaySafeCard, or Ukash card for values ranging from $500 - 1,000 USD in order to get the password for your files.
When first run, this program will scan your computer for data files and convert them to password protected RAR .exe files. These password protected data files will be named in a format similar to test.txt(!! to decrypt email id 712113261 to security11220@gmail.com !!).exe. It will then use Sysinternal's SDelete to delete the original files in such a way that they cannot be undeleted using file recovery tools. It will also set a Windows Registry Run entry to start c:\dvsdlk\svchost.exe when your computer starts. This program is launched immediately when you logon and blocks access to your Windows environment. If you boot your computer using a Windows Recovery disk or another offline recovery CD, you can delete or rename the c:\dvsdlk\svchost.exe file in order to regain access to your Windows Desktop. This "lockout" screen will also prompt you to send the hackers the ransom in order to get a passcode for the system lockout screen and for your password protected files.The files that this infection creates when it is installed are:
c:\Documents and Settings\All Users\Desktop\fvd31234.bat
c:\Documents and Settings\All Users\Desktop\fvd31234.txt
c:\dvsdlk\svchost.exe
c:\ProgramData\rbnedwdels\svchost.exe
c:\ProgramData\sgcvsap\svchost.exe
c:\ProgramData\tcvedwdcv\ghzsrwhbfg.dlls
c:\ProgramData\tcvedwdcv\udsjaqsksw.dlls
c:\ProgramData\thcgds\dkpslqhnsoa.dll
c:\ultimatedecrypter\dc.exe
c:\WINDOWS\system32\cfwin32.dll
c:\WINDOWS\system32\csrss32.dll
c:\WINDOWS\system32\csrss64.dll
c:\WINDOWS\system32\default2.sfx
c:\WINDOWS\system32\NoSafeMode.dll
c:\WINDOWS\system32\nsf.exe
c:\WINDOWS\system32\sdelete.dll
c:\WINDOWS\system32\svschost.exe
The Anti-Child Porn Spam Protection ransomware will also create a Windows service with a service name of fdPHosts, a display name of Function Discovery Provider Host Records, and a imagepath of C:\WINDOWS\system32\svschost.exe. This service will run in the background created password-protected copies of new data files that are created on the computer and then delete the originals. Therefore, once you regain access to your computer you should immediately disable this service.Unfortunately, at this time there is no method to create the passcodes, though one may be created in the future.
Update: 4/17/12
This ransomware has been updated today.It still uses the name Anti-Child Porn Spam Protection, but uses some different file names and service names.
The new Windows service that is created is the NIaSvc, with a display name Network Locatlon Awareness and a imagepath of C:\WINDOWS\system32\svschost.exe.
The files that are installed with this variant are:
c:\dc.exe
c:\svchost.exe
c:\Documents and Settings\All Users\Desktop\.bat
c:\Documents and Settings\All Users\Desktop\.txt
c:\ProgramData\.bat
c:\ProgramData\.dll
c:\ProgramData\.dll.dlls
c:\ProgramData\.dlls
c:\ProgramData\svchost.exe
c:\WINDOWS\system32\cfwin32.dll
c:\WINDOWS\system32\csrss32.dll
c:\WINDOWS\system32\csrss64.dll
c:\WINDOWS\system32\default2.sfx
c:\WINDOWS\system32\NoSafeMode.dll
c:\WINDOWS\system32\nsf.exe
c:\WINDOWS\system32\sdelete.dll
c:\WINDOWS\system32\svschost.exe
Update 03/13/2013
There may be a way to recover your decryption password. Please follow the steps in this post.
Edited by Grinler, 13 March 2013 - 08:48 AM.
Possible way to decrypt passwords




 Back to top
Back to top













