Damn Bastard,
Who are you referring to?

Posted 06 January 2015 - 10:42 AM
Damn Bastard,
Posted 06 January 2015 - 10:59 AM
Damn Bastard,
Who are you referring to?
The genius that make this ransomware crap.
To rename all the files and overwrite the new ones Im use Flexible Renamer V 8.4. Works for me.
Posted 06 January 2015 - 11:02 AM
/sensitive
I'm sorry couldn't help myself ![]()
Posted 06 January 2015 - 11:06 AM
Wozar's tools would save not only my zip and documents. It would save part of my history. Two years of life of my dougther. I can't re download that things
Posted 06 January 2015 - 11:11 AM
You might need to re-run the tool.
He did say if it was not encrypted, the tool would encrypt untouched files.
OR
It could be part of the new script the virus is running...
/shrug
Volanz
(Sorry, Grinler... )
Edited by Volanz, 06 January 2015 - 11:18 AM.
Posted 06 January 2015 - 11:16 AM
Posted 06 January 2015 - 11:20 AM
Yes, the malware author extended the list of files that are targeted. Previous version targeted the following file types:Also gets some zip, pdf files encrypted too,
|.3fr|.accdb|.ai|.arw|.bay|.cdr|.cer|.cr2|.crt|.crw|.h|.dbf|.dcr|.der|.dng|.doc|.docm|.docx|.dwg|.dxf|.dxg|.eps|.erf |.indd|.jpe|.jpg|.kdc|.mdb|.mdf|.mef|.mrw|.nef|.nrw|.odb|.odm|.odp|.ods|.odt|.orf|.p12|.p7b|.p7c|.pdd|.pef|.pem|.pfx |.ppt|.pptm|.pptx|.psd|.pst|.ptx|.r3d|.raf|.raw|.rtf|.rw2|.rwl|.srf|.srw|.wb2|.wpd|.wps|.xlk|.xls|.xlsb|.xlsm|.xlsx|The new variant targets the following file types:
|.3fr|.3gp|.accdb|.ai|.amv|.arw|.asf|.avi|.bay|.cdr|.cer|.cr2|.crt|.crw|.dbf|.dcr|.der|.divx|.dng|.doc|.docm|.docx |.dwg|.dxf|.dxg|.eps|.erf|.fla|.indd|.jpe|.jpg|.kdc|.mdb|.mdf|.mef|.mov|.mp3|.mp4|.mpg|.mrw|.nef|.nrw|.odb|.odm|.odp |.ods|.odt|.orf|.p12|.p7b|.p7c|.pdd|.pef|.pem|.pfx|.ppt|.pptm|.pptx|.psd|.pst|.ptx|.r3d|.raf|.rar|.raw|.rtf|.rw2|.rwl |.srf|.srw|.tar|.wb2|.wma|.wmv|.wpd|.wps|.xlk|.xls|.xlsb|.xlsm|.xlsx|.zipSo if you find .zip or .mp3 files on your system have been encrypted you were hit by the new variant and not the old one. In that case the current decrypter will not work for you.
Edited by Fabian Wosar, 06 January 2015 - 11:20 AM.
Posted 06 January 2015 - 11:24 AM
Nice.....
Any eta on updates for your tool?
(Maybe I should leave this topic alone..Sorry if I'm annoying. Just home from work with nothing to do.)
Edited by Volanz, 06 January 2015 - 11:25 AM.
Posted 06 January 2015 - 12:16 PM
Posted 06 January 2015 - 06:40 PM
No ETA yet. But I am working on it. I am optimistic I can provide a solution though.
Thanks for the great work Fabian,
Ive been getting the same results as Royalflush, The decoder says files are ok when i list them individually but jpg open with a blank page. If i run the list the Not responding problem happens.
Do you want me to send any affected files? I only hope to help.
Thank you so much for the great efforts with this problem, the world needs more good guys like yourself.
Thanks Jimmygothit too.![]()
Posted 06 January 2015 - 07:03 PM
Posted 06 January 2015 - 08:12 PM
PClock VB6 Cryptolocker Patcher
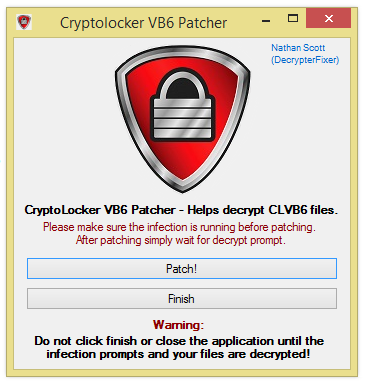
Link: http://download.bleepingcomputer.com/Nathan/CryptolockerVB6_Patcher.exe
This patcher was made to help victims of PClock Cryptolocker (VB6 CryptoLocker) get their files back. This patcher works with both versions of the infection. As Fabian said above, this patcher will only work if you still have the infection present and running on the machine. If you no longer have the infection on the machine you can download it again from the URL below:
Hxxp://invisioncorp.com.au/scripts/wl/cl.exe
(THIS LINK DOES CONTAIN A INFECTION! DO NOT DOWNLOAD UNLESS YOU HAVE ALREADY BEEN INFECTED BY THIS INFECTION AND HAVE REMOVED IT!)
If you do not want to deal with downloading an infection and you have accidentally removed your infection, you can wait for Fabian to come out with a Decrypter for the new version.
If you have ran Fabians decrypter, you will need to not only install the infection again, but also rename all backed up encrypted files back to their original name before running my patcher.
If you are a victim that just got this infection and it is still on your machine and you have no tried Fabians decrypter, you may ignore all the above comments.
Instructions:
1.) Make sure the infection is running and you can see the main screen of the infection (Says 'Your Personal Files Have Been Encrypted').
2.) Download the patcher and place it on your desktop or similar location, and run the application.
3.) You will see a application that looks like the image above, simply click on "Patch!" to begin. (If you get errors at this step ensure the infection is running, and you have correct permissions.)
4.) A Messagebox will prompt and tell you to wait 5-10 minutes so the patch can work. Make sure to NOT close the application after this. Do not close the application until all files are decrypted.
5.) After a few minutes the virus screen will turn into a Decrypt Screen. Click the Decrypt button and all your files will be decrypted.
6.) Click "Finish!" and enjoy your files.
REMEMBER!
This infections code is very unstable and armature, and sometimes it can put files in the list of encrypted files that are NOT encrypted. This means when the decryption process is ran, it can corrupt files that aren't encrypted. So before decryption you should try and check the list and make sure there aren't files that are ok on the list. Sometimes this is not possible with the volume of files encrypted and that is understandable, this is simply a warning.
Enjoy.
Edited by Nathan, 06 January 2015 - 08:12 PM.
Posted 06 January 2015 - 08:44 PM
I Tried your solution Nathan. So far so good. I can see encrypted mp4 been decrypted with no harm. It's promising. Your rocks guys. Thanks a lot.
Posted 06 January 2015 - 08:56 PM
Edited by royalflush, 06 January 2015 - 08:58 PM.
Posted 06 January 2015 - 09:08 PM
if you have removed the infection or ran Fabians tool you have to use your better judgement. You can try it, or wait.
but it you have not removed the infection you are 100%
0 members, 1 guests, 0 anonymous users