
Microsoft has highlighted a novel attack dubbed "Dirty Stream," which could allow malicious Android apps to overwrite files in another application's home directory, potentially leading to arbitrary code execution and secrets theft.
The flaw arises from the improper use of Android's content provider system, which manages access to structured data sets meant to be shared between different applications.
This system incorporates data isolation, URI permissions, and path validation security measures to prevent unauthorized access, data leaks, and path traversal attacks.
When implemented incorrectly, custom intents, which are messaging objects that facilitate communication between components across Android apps, could bypass these security measures.
Examples of incorrect implementations include trusting unvalidated filenames and paths in intents, misuse of the 'FileProvider' component, and inadequate path validation.
Dirty Stream allows malicious apps to send a file with a manipulated filename or path to another app using a custom intent. The target app is misled into trusting the filename or path and executes or stores the file in a critical directory.
.png)
Source: Microsoft
This manipulation of the data stream between two Android apps turns a common OS-level function into a weaponized tool and can lead to unauthorized code execution, data theft, or other malicious outcomes.
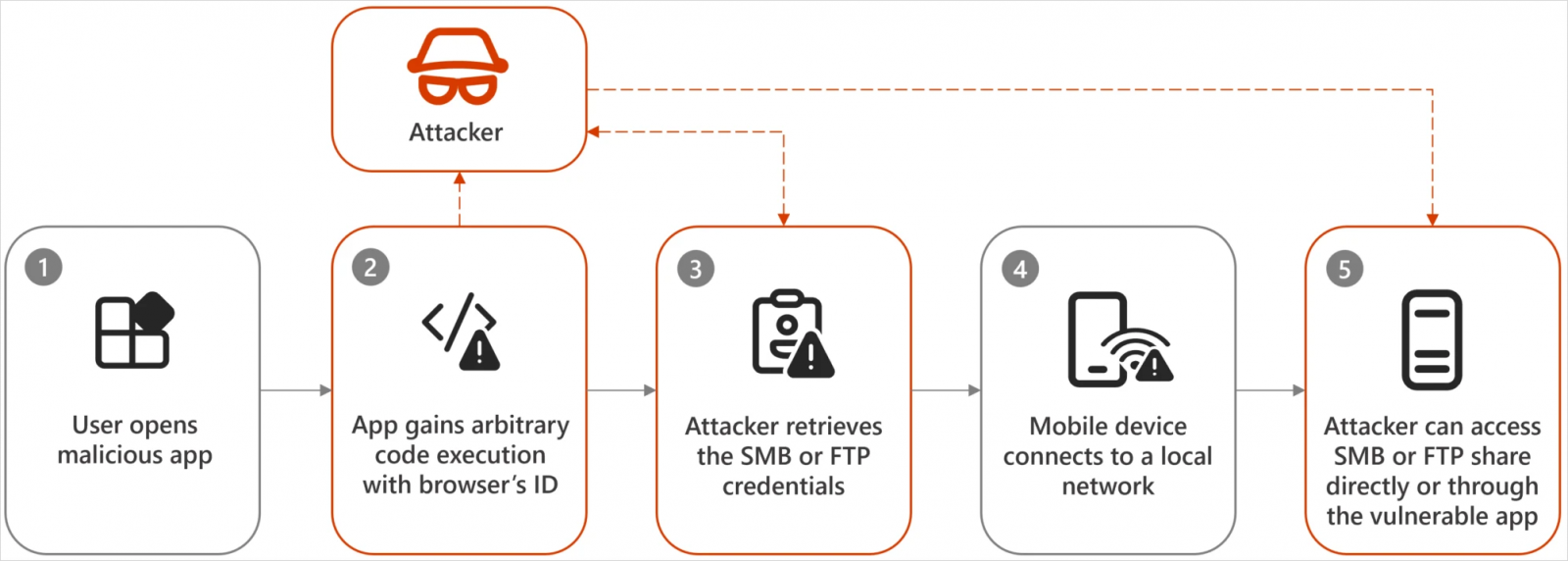
Source: Microsoft
Microsoft researcher Dimitrios Valsamaras noted that these incorrect implementations are unfortunately abundant, impacting apps installed over four billion times and offering a massive attack surface.
"We identified several vulnerable applications in the Google Play Store that represented over four billion installations," reads the report.
"We anticipate that the vulnerability pattern could be found in other applications. We're sharing this research so developers and publishers can check their apps for similar issues, fix as appropriate, and prevent introducing such vulnerabilities into new apps or releases."
Two apps highlighted as vulnerable to Dirty Stream attacks in Microsoft's report are Xiaomi's File Manager application, which has over a billion installations, and WPS Office, which counts around 500 million installs.
Both companies were responsive to the findings and collaborated with Microsoft to deploy fixes to mitigate the risks posed by the vulnerability.
Microsoft's findings were shared with the Android developer community through an article on the Android Developers website to prevent similar vulnerabilities in future builds.
Google also updated its app security guidance to highlight common implementation errors in the content provider system that allow security bypasses.
As for end users, there's not much they can do besides keeping the apps they use up to date and avoiding downloading APKs from unofficial third-party app stores and other poorly vetted sources.



Comments
0Willy - 2 months ago
I struck a problem months ago. As you know, a TV is no longer a just a device to display a TV broadcast. It is actually a computer.
Setting up a new TV very recently, the screen popped up a message offering a choice to scan using QR code or manually. I chose QR code. During the subsequent configuration, there were a lot of routine questions, then came "enter your credit card details". I went reset and did it manually. There was no credit card question during manual configuration. Since, there are more than usual attempted phone scams since. One day, three different variations on a toll road scam in about 15 minutes.
It seems highly likely the QR Code scanner had code injected before being updated automatically 'for my convenience' in the background. QR scanner uninstalled, then phone scanned by three separate malware scanner revealed the phone clean.
Do not trust play store apps. Any claim Google makes about Play store security is hogwash! Similarly, Android is Linux based. How does this scenario make Linux any safer than Windows?
U_Swimf - 1 month ago
DUH. stop using QR code registrations. It's persistent access by a third party directly to your phone, even if u unregister it somehow. It's one and done thing.
There have been more permissions flags for cars and tvs in the past years added than anyone has actually seen being used yet. Mostly because they're all auto granted assuming u A. Downloaded it B. opened it and C. the devs have a privacy policy linked to google's saying by using their program we agee to * x
It isnt safer. Ppl are just as likely if not more confused when told to run everything as sudo or root there. In fact i wouldnt be surprised if in some cases MS has safer security in some regaurds just cause they need to have it in order to comply with laws and stuff. Trust nothing.
0Willy - 1 month ago
"DUH. stop using QR code registrations."
First time bitten for a very, very long time. I learn fast, but have to admit not putting in the same level of security effort using using phone and TV and had a false sense of security with phone apps from Google store. All I can say is "learnt immediately, lost nothing and trashed the QR app".
U_Swimf - 1 month ago
the thing about modern malware, is iit's not flagged as malware. Javascript injection is a feature. There's a reason it isnt changing. Check your apps libraries for usage of cetain TV related software. Leanback Launcher, anything with Apple's A logo that is used for personalizations. Looks like sticks or bones making the letter A crossing each other.
Hmm888 - 1 month ago
Linux missionaries, much like Trump's will defend and recommend Linux to everyone. Like maga supporters, they're wired differently than most people.
Hmm888 - 1 month ago
Google and the Android ecosystem is a joke. Google rarely acts upon complaints from customers for malware especially in their extensions. I suppose they must have X number of complaints before their dweebs who mostly sit all day and watch TikTok videos take action.